Scaling information entry securely whereas sustaining operational effectivity is a crucial problem for organizations. Entry rights are sometimes fragmented throughout numerous AWS providers, as completely different enterprise items personal and handle completely different information shops, comparable to Amazon Easy Storage Service (Amazon S3) and Amazon Redshift. As information grows, modeling entry in AWS Id and Entry Administration (IAM) insurance policies turns into difficult for information house owners, as they attempt to handle entry for various teams and customers throughout accounts within the group. Managing these distributed entry rights requires substantial overhead, as a result of safety groups and information house owners should collaborate to replace and monitor permissions to ensure information is simply accessible to licensed customers.
Recognizing this problem, the Amazon S3 Entry Grants integration with Amazon Redshift permits centralized consumer authentication by AWS IAM Id Heart, offering unified id throughout the group. S3 Entry Grants permits particular IAM Id Heart customers or teams to entry registered Amazon S3 places by a grant. Making a grant with a gaggle as grantee lets the group members entry solely the S3 bucket, prefix, or object throughout the grant’s scope. Which means that entry might be managed by merely making a grant for a gaggle and including or eradicating the consumer from the group, decreasing administrative overhead.
On this submit, we present the way to grant Amazon S3 permissions to IAM Id Heart customers and teams utilizing S3 Entry Grants. We additionally take a look at the combination utilizing an IAM Id Heart federated consumer to unload information from Amazon Redshift to Amazon S3 and cargo information from Amazon S3 to Amazon Redshift.
Resolution overview
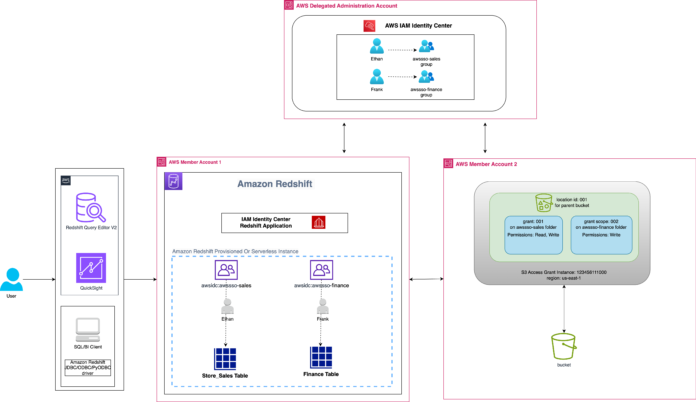
This submit covers a use case the place a big group manages hundreds of company customers throughout a number of enterprise items by their id supplier (IdP). These customers recurrently work together with huge quantities of information saved throughout quite a few S3 buckets, regularly performing extract, rework, and cargo (ETL) operations by Amazon Redshift. Their objective is to have a less complicated ETL course of of information loading and unloading operations in Amazon Redshift with out managing a number of IAM roles and insurance policies for Amazon S3 entry. Additionally, they need a centralized entry administration answer that seamlessly integrates their company identities from current IdP with AWS providers.
For this answer, AWS Organizations is enabled and IAM Id Heart is configured within the delegated administration account. The group has two member accounts: Member Account 1 runs analytical workloads on Amazon Redshift, with all of the providers enabled with trusted id propagation, and Member Account 2 manages information saved in Amazon S3; right here you’ll arrange S3 Entry Grants. Amazon Redshift will load the user-specific information from Amazon S3 saved in Member Account 2 utilizing entry management primarily based on IAM Id Heart customers and teams. This improves the consumer expertise sustaining a single authentication mechanism inside a corporation, retaining entry management, and useful resource separation utilizing AWS accounts as a boundary per enterprise items.
The next diagram illustrates the answer structure.
Determine 1: Structure exhibiting the answer
To run this answer in a single account, configure Amazon Redshift and S3 Entry Grants with account situations of IAM Id Heart. Evaluation When to make use of account situations for extra data.
The answer workflow consists of the next steps:
The consumer configures and connects with their respective shoppers (comparable to Amazon Redshift Question Editor v2 or a SQL shopper) to entry Amazon Redshift utilizing IAM Id Heart.
A brand new browser home windows opens and is redirected to the login web page of the IdP.
The consumer logs in with their IdP consumer title and password.
After the login is profitable, the consumer is redirected to the shopper utility, such because the Amazon Redshift Question Editor.
When the consumer tries to entry information in Amazon S3 utilizing the LOAD or UNLOAD SQL command, Amazon Redshift in Member Account 1 will request credentials from the S3 Entry Grants occasion from Member Account 2, the place the Amazon S3 information is saved. This request will comprise the consumer context.
S3 Entry Grants will then consider the request towards the grants it has, matching the id specified within the grant with the one acquired within the request. If there’s a match, the requestor will obtain non permanent entry to the Amazon S3 places specified within the grant’s scope.
To implement the answer, we stroll you thru the next steps:
Allow S3 Entry Grants in your Amazon Redshift managed utility.
Replace IAM position permissions used within the utility.
Create a bucket for S3 Entry Grants.
Create an IAM coverage and position for S3 Entry Grants.
Arrange S3 Entry Grants.
Permit cross-account entry of assets.
Create Redshift tables.
Unload and cargo information in Amazon Redshift.
Conditions
You need to have the next stipulations already arrange:
Allow S3 Entry Grants from the Amazon Redshift managed utility
After you could have created your Redshift utility in IAM Id Heart, it’s worthwhile to carry out the next steps to allow S3 Entry Grants within the account the place Amazon Redshift exists. For this submit, we use Member Account 1:
Log in to the AWS Administration Console as admin.
On the Amazon Redshift console, select IAM Id Heart connection within the navigation pane.
Choose the managed Redshift utility and select Edit.
Select Amazon S3 entry grants in Trusted id propagation.
Select Save adjustments.
The next screenshot exhibits the up to date configuration.
Determine 2: Redshift managed utility
Replace the IAM position permission connected to the Amazon Redshift managed utility
The Amazon Redshift managed utility has an IAM position connected (within the previous screenshot, you may see the position known as IAMIDCRedshiftRole below IAM position for IAM Id Heart entry. We now want to change the coverage on this position and add permissions to permit interplay with Amazon S3. Edit the position and add s3:GetAccessGrantsInstanceForPrefix and s3:GetDataAccess as proven within the following coverage:
{
“Model”: “2012-10-17”,
“Assertion”: (
{
“Sid”: “AllowGetRedsfhitInformation”,
“Impact”: “Permit”,
“Motion”: (
“redshift-serverless:ListNamespaces”,
“redshift-serverless:ListWorkgroups”,
“redshift:DescribeQev2IdcApplications”,
“redshift-serverless:GetWorkgroup”
),
“Useful resource”: “*”
},
{
“Sid”: “AllowDescribeIdentityCenter”,
“Impact”: “Permit”,
“Motion”: (
“sso:DescribeApplication”,
“sso:DescribeInstance”
),
“Useful resource”: (
“arn:aws:sso:::occasion/”,
“arn:aws:sso:::utility//*”
)
},
{
“Sid”: “RetrieveAGinstanceforParticularPrefix”,
“Impact”: “Permit”,
“Motion”:
“s3:GetAccessGrantsInstanceForPrefix”,
“Useful resource”: “*”
},
{
“Sid”: “CrossAccountAccessGrantsPolicy”,
“Impact”: “Permit”,
“Motion”: (
“s3:GetDataAccess”
),
“Useful resource”: “arn:aws:s3:::access-grants/default”
}
)
}
Substitute together with your IAM Id Heart occasion ID and with the account ID the place IAM Id Heart is ready up. You additionally want to exchange the useful resource in CrossAccountAccessGrantscasePolicy together with your S3 Entry Grants occasion data.
Create an S3 bucket for S3 Entry Grants
On this step, you create a S3 bucket that you just need to grant entry to or use an current bucket. For this submit, we create a bucket known as amzn-s3-demo-bucket. You possibly can select one other acceptable title. For extra data, see Making a normal goal bucket.
The bucket have to be situated in the identical AWS Area as your S3 Entry Grants occasion and IAM Id Heart.
Subsequent, create two folders within the newly created S3 bucket. In case you’re utilizing an current S3 bucket, determine two folders to make use of for this walkthrough. For this weblog submit, we create two folders: awssso-sales and awssso-finance, below a bucket named amzn-s3-demo-bucket. The aim of making two folders is in order that customers from completely different teams have entry solely to their respective folder.
Create an IAM coverage and position for S3 Entry Grants
Full the next steps to create an IAM coverage to scope the permissions for a particular entry grant:
Create an IAM coverage with the next permissions. For extra data on creating IAM coverage, see Create IAM insurance policies. To get extra data on the next particular coverage, consult with Register a location.
{
“Model”: “2012-10-17”,
“Assertion”: (
{
“Sid”: “ObjectLevelReadPermissions”,
“Impact”: “Permit”,
“Motion”: (
“s3:GetObject”,
“s3:GetObjectVersion”,
“s3:GetObjectAcl”,
“s3:GetObjectVersionAcl”,
“s3:ListMultipartUploadParts”
),
“Useful resource”: “arn:aws:s3:::/*”,
“Situation”: {
“StringEquals”: {
“aws:ResourceAccount”: “”
},
“ArnEquals”: {
“s3:AccessGrantsInstanceArn”: (
“arn:aws:s3:::access-grants/default”
)
}
}
},
{
“Sid”: “ObjectLevelWritePermissions”,
“Impact”: “Permit”,
“Motion”: (
“s3:PutObject”,
“s3:PutObjectAcl”,
“s3:PutObjectVersionAcl”,
“s3:DeleteObject”,
“s3:DeleteObjectVersion”,
“s3:AbortMultipartUpload”
),
“Useful resource”: “arn:aws:s3:::/*”,
“Situation”: {
“StringEquals”: {
“aws:ResourceAccount”: “”
},
“ArnEquals”: {
“s3:AccessGrantsInstanceArn”: “arn:aws:s3:::access-grants/default”
}
}
},
{
“Sid”: “BucketLevelReadPermissions”,
“Impact”: “Permit”,
“Motion”: (
“s3:ListBucket”
),
“Useful resource”: “arn:aws:s3:::”,
“Situation”: {
“StringEquals”: {
“aws:ResourceAccount”: “”
},
“ArnEquals”: {
“s3:AccessGrantsInstanceArn”: “arn:aws:s3:::access-grants/default”
}
}
}
)
}
Create an IAM position that has permission to entry your S3 information within the Area. For extra data, see IAM position creation. On this instance, we create an IAM position known as iamidcs3accessgrant. You might want to connect the previous coverage to the IAM position.
Use the next belief coverage for the IAM position:
{
“Model”: “2012-10-17”,
“Assertion”: (
{
“Sid”: “ForAccessGrants”,
“Impact”: “Permit”,
“Principal”: {
“Service”: “access-grants.s3.amazonaws.com”
},
“Motion”: (
“sts:AssumeRole”,
“sts:SetContext”,
“sts:SetSourceIdentity”
),
“Situation”: {
“StringEquals”: {
“aws:SourceAccount”:””,
“aws:SourceArn”:”arn:aws:s3:::access-grants/default”
}
}
}
)
}
Arrange S3 Entry Grants
The S3 Entry Grants occasion serves because the container in your S3 Entry Grants assets, which embrace registered places and grants. You possibly can create just one S3 Entry Grants occasion per Area per account. You possibly can affiliate this S3 Entry Grants occasion to your company listing together with your IAM Id Heart occasion. After you’ve accomplished so, you may create grants in your company customers and teams. S3 Entry Grants requires registering a location to map an S3 bucket or prefix to an IAM position, enabling safe entry by offering non permanent credentials to grantees for that particular location.
Full the next steps to arrange S3 Entry Grants:
On the Amazon S3 console, select your most well-liked Area.
Within the navigation pane, select Entry Grants.
Select Create S3 Entry Grants occasion.
Choose Add IAM Id Heart occasion in and enter the IAM Id Heart occasion Amazon Useful resource Identify (ARN). For this submit, we use the delegated administration account IAM Id Heart ARN.
Select Subsequent.
Determine 3: S3 Entry Grants occasion
After you create an Amazon S3 Entry Grants occasion in a Area in your account, you register an Amazon S3 location in that occasion. For Location scope, select Browse S3 or enter the S3 URI path to the placement that you just need to register. After you enter a URI, you may select View to browse the placement. On this instance, we offer the scope as s3://amzn-s3-demo-bucket.
For IAM position, choose Select from current IAM roles and select the IAM position you beforehand created (iamidcs3accessgrant).
Select Subsequent.
It will register a location in your S3 Entry Grants occasion.
Determine 4: S3 Entry Grants occasion location scope
You’ll now create a grant.
In case you chosen the default Amazon S3 location, use the Subprefix field to slender the scope of the entry grant. For extra data, see Working with grants in S3 Entry Grants.
In case you’re granting entry solely to an object, choose Grant scope is an object. In our instance, we register the placement as s3://amzn-s3-demo-bucket after which for the subprefix, we specify the folder title adopted by an asterisk (awssso-sales/*).
Beneath Permissions and entry, choose the Permission stage, both Learn, Write, or each. On this instance, we choose each as a result of we’ll first unload from Amazon S3 to Amazon Redshift after which copy from the identical bucket to Amazon Redshift.
For Grantee kind, select Listing id from IAM Id Heart.
For Listing id kind, you may select both Person or Group. On this instance, we select Group.
For IAM Id Heart group ID, enter the group ID from IAM Id Heart the place consumer and group data belongs.
To get this worth, open the IAM Id Heart console and select Teams within the navigation pane, then select one of many teams you need to present entry and replica the worth below Group ID. Within the following instance, we accumulate the group ID data from the delegated administration account.
Determine 5: IAM Id Heart group data
Select Subsequent.
Determine 6: S3 Entry Grants occasion permissions and entry
Select End.
Determine 7: S3 Entry Grants occasion assessment data web page
You possibly can view the small print of the entry grant on the Amazon S3 console, as proven within the following screenshot. For extra data, see View a grant.
Determine 8: S3 Entry Grants grants
Equally, you will get the small print of a location that’s registered in your S3 Entry Grants occasion. For extra data, see View the small print of a registered location.
Determine 9: S3 Entry Grants places
Permit cross-account entry of assets and create preliminary tables
Now we need to share assets to make our cross-account state of affairs work. This step is simply wanted in case your Amazon Redshift and Amazon S3 assets are in several accounts. This needs to be accomplished within the account the place Amazon S3 is ready up. Full the next steps:
On the AWS RAM console, within the navigation pane, select Useful resource shares.
Select Create useful resource share.
For Identify, enter a descriptive title for the useful resource share (for instance, s3accessgrant).
For Assets – non-obligatory, select S3 Entry Grants. The S3 Entry Grants occasion you created will likely be proven; choose the default S3 Entry Grant occasion ARN.
Select Subsequent.
Beneath Managed permission for s3:AccessGrants, you may select to affiliate a managed permission created by AWS with the useful resource kind, select an current buyer managed permission, or create your personal buyer managed permission for supported useful resource sorts. On this submit, we select the present permission named AWSRAMPermissionAccessGrantsData.
Select Subsequent.
For Grant entry to principals, select Permit sharing solely inside your group and enter the account ID the place the Redshift occasion exists.
Select Add.
Select Subsequent.
Select Create useful resource share.
The next screenshot exhibits the brand new useful resource share particulars.
Determine 10: AWS RAM – create useful resource share wizard
Create tables in Amazon Redshift
As an Amazon Redshift admin consumer, it’s worthwhile to first create the tables you’ll use to unload information. Within the following code, we create a brand new store_sales_s3access desk:
CREATE TABLE IF NOT EXISTS
sales_schema.store_sales_s3access (
ID INTEGER ENCODE az64,
Product varchar(20),
Sales_Amount INTEGER ENCODE az64
)
DISTSTYLE AUTO ;
Additionally be certain that the next permissions are utilized on the respective IAM Id Heart group; this group is represented in Amazon Redshift as a Redshift position. For this submit, we grant permissions to the awssso-sales group:
grant utilization on schema sales_schema to position “awsidc:awssso-sales”;
grant choose,insert for tables in schema sales_schema to position “awsidc:awssso-sales”;
As an Amazon Redshift admin consumer, you could have created a Redshift desk and assigned related permissions to the Redshift database position awsidc:awssso-sales. Now when an authenticated consumer that belongs to the group awssso-sales runs a question in Amazon Redshift to entry Amazon S3 (comparable to a COPY, UNLOAD, or Amazon Redshift Spectrum operation), Amazon Redshift retrieves non permanent Amazon S3 entry credentials scoped to that IAM Id Heart consumer from S3 Entry Grants. Amazon Redshift then makes use of the retrieved non permanent credentials to entry the licensed Amazon S3 places for that question.
Unload and cargo information in Amazon Redshift
On this step, we log in to the Amazon Redshift Question Editor utilizing IAM Id Heart authentication and run an UNLOAD command to unload information from the desk created earlier into the S3 bucket. After that, we run the COPY command to repeat data from Amazon S3 into the identical desk in the identical listing we unloaded the information from.
Full the next steps to entry the Amazon Redshift Question Editor with an IAM Id Heart consumer:
On the Amazon Redshift console, open the Amazon Redshift Question Editor.
Select (right-click) your Redshift occasion and select Create connection.
Select IAM Id Heart as your authentication technique.
A pop-up will seem. As a result of your IdP credentials are already cached, it makes use of the identical credentials and connects to the Amazon Redshift Question Editor utilizing IAM Id Heart authentication.
Now you’re able to run the SQL queries in Amazon Redshift.
Unload information
As a federated consumer, you’ll first run an unload command from the desk store_sales within the bucket s3://amzn-s3-demo-bucket/awssso-sales/.
On this submit, we run an UNLOAD command as a federated IAM Id Heart consumer (Ethan), the place we will likely be unloading the information from a Redshift desk. Substitute the S3 bucket title with the one you created.
UNLOAD (‘SELECT * FROM “dev”.”sales_schema”.”store_sales”‘)
TO ‘s3://amzn-s3-demo-bucket/awssso-sales/’;
The previous command doesn’t embrace an IAM position ARN. This simplified syntax not solely makes your code extra readable, but in addition reduces the potential for configuration errors. The underlying permissions are dealt with mechanically by S3 Entry Grants and trusted id propagation, sustaining strong safety whereas simplifying permissions administration.
Load information
Now we exhibit a typical information workflow utilizing the identical federated IAM Id Heart consumer (Ethan), the place we will likely be working the COPY command accessing the identical Amazon S3 location the place we beforehand unloaded our information. Use to following command to load information right into a separate desk known as store_sales_s3access:
copy dev.sales_schema.store_sales_s3access
from ‘s3://amzn-s3-demo-bucket/awssso-sales/’ delimiter ‘|’
If consumer Ethan tries to unload “sales_schema”.”store_sales” in sales_schema to a distinct folder within the S3 bucket (awssso-finance), they get a permission denied error. It is because entry is managed by S3 Entry Grants, and this consumer doesn’t have a grant to the awssso-finance folder. Use the next command to check the entry denied use case:
UNLOAD (‘SELECT * FROM “dev”.”sales_schema”.”store_sales”‘)
TO ‘s3://amzn-s3-demo-bucket/awssso-finance/’;
Determine 11: QEv2 question consequence error
IAM Id Heart associated operations are mechanically captured and logged in AWS CloudTrail, providing enhanced visibility and complete audit capabilities. To view detailed error data on the CloudTrail console, select Occasion historical past within the navigation pane, then specify s3.amazonaws.com because the occasion supply and open GetDataAccess.
The next screenshot exhibits the snippet from the CloudTrail logs exhibiting that consumer entry is denied.
Determine 12: Amazon CloudTrail
Clear up
Full the next steps to wash up your assets:
Delete the IdP purposes that you just created to combine with IAM Id Heart.
Delete the IAM Id Heart configuration.
Delete the Redshift utility and the Amazon Redshift provisioned cluster or serverless occasion that you just created for testing.
Delete the IAM position and IAM insurance policies that you just created on this submit.
Delete the permission set from IAM Id Heart that you just created for the Amazon Redshift Question Editor within the administration account.
Delete the S3 bucket and related S3 Entry Grants occasion.
Conclusion
On this submit, we explored the way to combine Amazon Redshift with S3 Entry Grants utilizing IAM Id Heart. We established cross-account entry to allow centralized consumer authentication by IAM Id Heart within the delegated administrator account, whereas protecting Amazon Redshift and Amazon S3 remoted by enterprise unit in separate member accounts. We additionally confirmed simplified variations of working COPY and UNLOAD instructions as a federated IAM Id Heart consumer with out utilizing an IAM position ARN. This setup creates a sturdy and safe analytics surroundings that streamlines information entry for enterprise customers.
For added steering and detailed documentation, consult with the next key assets:
In regards to the Authors
 Maneesh Sharma is a Senior Database Engineer at AWS with greater than a decade of expertise designing and implementing large-scale information warehouse and analytics options. He collaborates with numerous Amazon Redshift Companions and prospects to drive higher integration.
Maneesh Sharma is a Senior Database Engineer at AWS with greater than a decade of expertise designing and implementing large-scale information warehouse and analytics options. He collaborates with numerous Amazon Redshift Companions and prospects to drive higher integration.
 Laura is an Id Options Architect at AWS, the place she thrives on serving to prospects overcome safety and id challenges. In her free time, she enjoys wreck diving and touring around the globe.
Laura is an Id Options Architect at AWS, the place she thrives on serving to prospects overcome safety and id challenges. In her free time, she enjoys wreck diving and touring around the globe.
 Praveen Kumar Ramakrishnan is a Senior Software program Engineer at AWS. He has almost 20 years of expertise spanning numerous domains together with filesystems, storage virtualization and community safety. At AWS, he focuses on enhancing the Redshift information safety.
Praveen Kumar Ramakrishnan is a Senior Software program Engineer at AWS. He has almost 20 years of expertise spanning numerous domains together with filesystems, storage virtualization and community safety. At AWS, he focuses on enhancing the Redshift information safety.
 Yanzhu Ji is a Product Supervisor within the Amazon Redshift group. She has expertise in product imaginative and prescient and technique in industry-leading information merchandise and platforms. She has excellent talent in constructing substantial software program merchandise utilizing internet growth, system design, database, and distributed programming methods. In her private life, Yanzhu likes portray, images, and taking part in tennis.
Yanzhu Ji is a Product Supervisor within the Amazon Redshift group. She has expertise in product imaginative and prescient and technique in industry-leading information merchandise and platforms. She has excellent talent in constructing substantial software program merchandise utilizing internet growth, system design, database, and distributed programming methods. In her private life, Yanzhu likes portray, images, and taking part in tennis.















Looks like my earlier comment didn’t appear, but I just wanted to say—your blog is so inspiring! I’m still figuring things out as a beginner,and reading your posts makes me want to keep going with my own writing journey.