As introduced by the US Division of Justice – the FBI and US DoD’s Protection Legal Investigative Service (DCIS) have managed to disrupt the infrastructure of the infamous infostealer, Danabot. ESET is likely one of the many cybersecurity firms to take part on this long-term endeavor, changing into concerned again in 2018. Our contribution included offering technical analyses of the malware and its backend infrastructure, in addition to figuring out Danabot’s C&C servers. The joint takedown effort additionally led to the identification of people answerable for Danabot growth, gross sales, administration, and extra. ESET took half within the effort alongside with Amazon, CrowdStrike, Flashpoint, Google, Intel471, PayPal, Proofpoint, Crew Cymru, Zscaler, Germany’s Bundeskriminalamt, the Netherlands’ Nationwide Police, and the Australian Federal Police.
These legislation enforcement operations had been performed beneath Operation Endgame – an ongoing world initiative geared toward figuring out, dismantling, and prosecuting cybercriminal networks. Coordinated by Europol and Eurojust, the operation efficiently took down essential infrastructure used to deploy ransomware via malicious software program.
Since Danabot has largely been disrupted, we are going to use this chance to share our insights into the workings of this malware-as-a-service (MaaS) operation, masking the options used within the newest variations of the malware, the authors’ enterprise mannequin, and an outline of the toolset supplied to associates. Other than exfiltrating delicate knowledge, we’ve got noticed that Danabot can be used to ship additional malware – together with ransomware – to an already compromised system.
Key factors of the blogpost:
ESET Analysis has been monitoring Danabot’s exercise since 2018 as a part of a worldwide effort that resulted in a significant disruption of the malware’s infrastructure.
Whereas primarily developed as an infostealer and banking trojan, Danabot additionally has been used to distribute extra malware, together with ransomware.
Danabot’s authors promote their toolset via underground boards and supply numerous rental choices to potential associates.
The everyday toolset supplied by Danabot’s authors to their associates consists of an administration panel utility, a backconnect instrument for real-time management of bots, and a proxy server utility that relays the communication between the bots and the precise C&C server.
Associates can select from numerous choices to generate new Danabot builds, and it’s their duty to distribute these builds via their very own campaigns.
Background
Danabot, which belongs to a bunch of infostealer and/or banking malware households coded within the Delphi programming language, gained prominence in 2018 by being utilized in a spam marketing campaign focusing on Australian customers. Since then, Danabot has expanded to different markets via numerous campaigns, undergone a number of main updates of its internals and backend infrastructure, and skilled each peaks and downturns in recognition amongst cybercriminals.
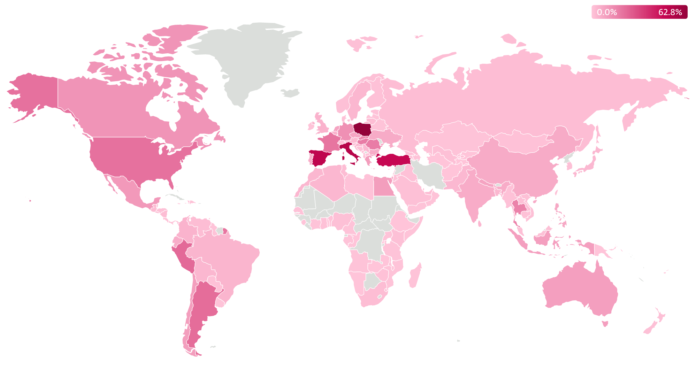
All through our monitoring since 2018, ESET has tracked and analyzed a considerable variety of distinct samples and recognized greater than 1,000 distinctive C&C servers. Throughout that interval, ESET analyzed numerous Danabot campaigns everywhere in the world, with Poland traditionally being some of the focused nations, as seen in Determine 1.
Determine 1. Worldwide Danabot detections as seen in ESET telemetry since 2018
Along with typical cybercrime, Danabot has additionally been utilized in much less typical actions corresponding to using compromised machines for launching DDoS assaults. For instance, a DDoS assault towards Ukraine’s Ministry of Protection was noticed by Zscaler quickly after the Russian invasion of Ukraine. A really comparable DDoS module to the one utilized in that assault was additionally utilized by a Danabot operator to focus on a Russian web site devoted to Arduino growth. These actions had been most likely motivated by the affiliate’s personal ambitions and political motivations.
Danabot group introduction
The authors of Danabot function as a single group, providing their instrument for lease to potential associates, who subsequently make use of it for their very own malicious functions by establishing and managing their very own botnets. The authors have even arrange a help web page on the Tor community with detailed details about the capabilities of their instrument, as depicted in Determine 2.
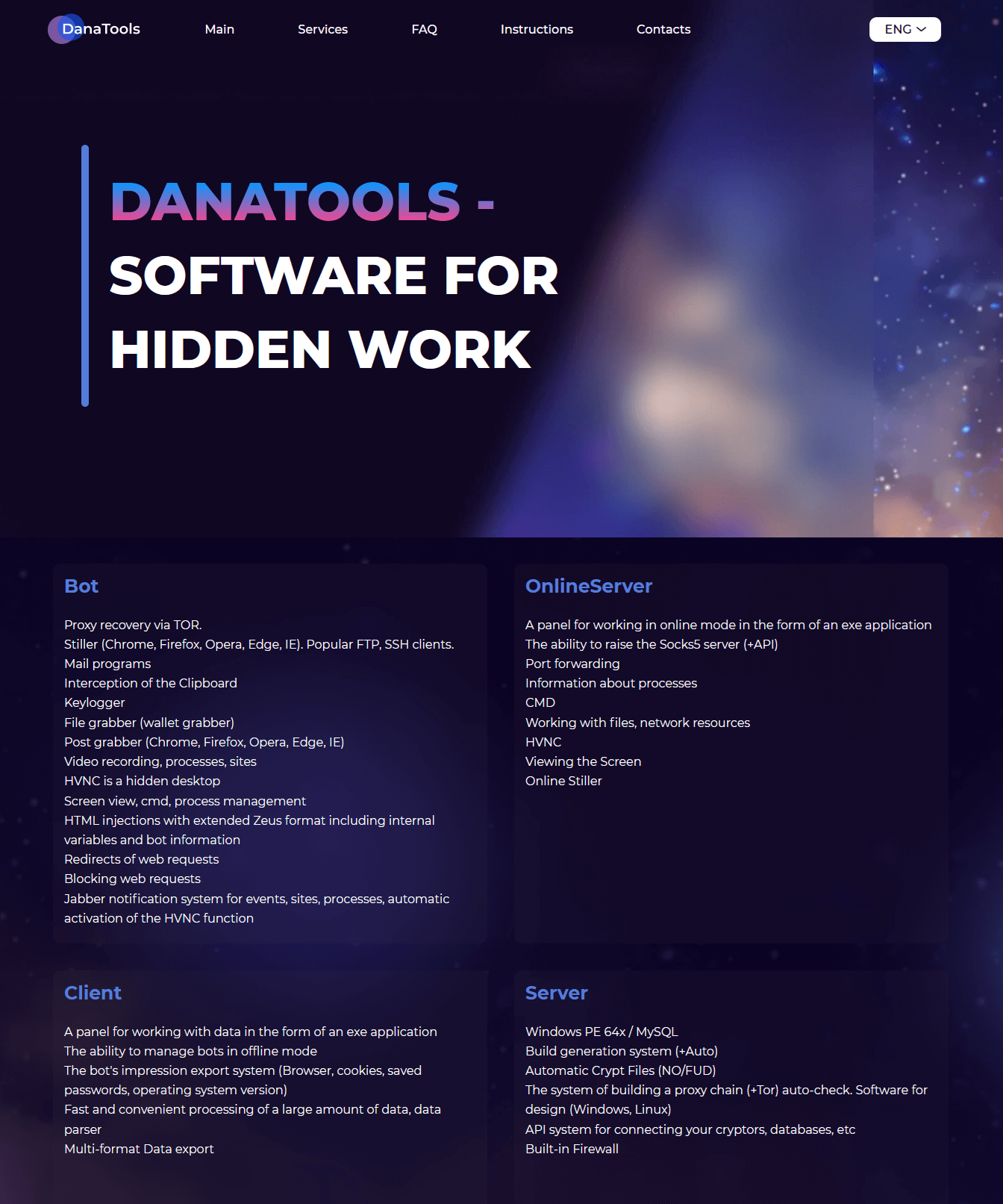
Determine 2. Danabot’s options as promoted on its help web site
To accumulate new clients, Danabot is regularly promoted in underground boards by the consumer JimmBee, who acts as one of many foremost builders and directors of the Danabot malware and its toolset. One other noteworthy particular person from the Danabot group is a consumer recognized in underground boards as Onix, who coadministers the Danabot infrastructure and can be answerable for gross sales operations.
Function overview
Danabot’s authors have developed an unlimited number of options to help clients with their malevolent goals. Essentially the most outstanding options supplied by Danabot embody:
the flexibility to steal numerous knowledge from browsers, mail purchasers, FTP purchasers, and different fashionable software program,
keylogging and display recording,
real-time distant management of the victims’ methods,
a FileGrabber command, generally used for stealing cryptocurrency wallets,
help for Zeus-like webinjects and kind grabbing, and
arbitrary payload add and execution.
Moreover using its stealing capabilities, we’ve got noticed a wide range of payloads being distributed via Danabot over time, corresponding to:
SystemBC,
Rescoms,
Ursnif,
Smokeloader,
Zloader,
Lumma Stealer,
RecordBreaker,
Latrodectus, and
NetSupportManager distant administration instrument.
Moreover, we’ve got encountered cases of Danabot getting used to obtain ransomware onto already compromised methods. We are able to title LockBit, Buran, Disaster, and a NonRansomware variant being pushed on a number of events.
Danabot’s capability to obtain and execute arbitrary payloads isn’t the one function used to distribute extra malware. Danabot was additionally noticed getting used as a instrument at hand off management of the botnet to a ransomware operator, as reported by Microsoft Menace Intelligence in late 2023.
Distribution strategies
All through its existence, in accordance with our monitoring, Danabot has been a instrument of alternative for a lot of cybercriminals and every of them has used totally different technique of distribution. Danabot’s builders even partnered with the authors of a number of malware cryptors and loaders, and supplied particular pricing for a distribution bundle to their clients, serving to them with the method. Matanbuchus is an instance of such a promoted loader.
Through the years, we’ve got seen all kinds of distribution strategies being utilized by Danabot associates, together with:
quite a few variants of electronic mail spam campaigns,
different malware corresponding to Smokeloader, DarkGate, and Matanbuchus, and
misuse of Google Advertisements.
Not too long ago, out of all distribution mechanisms we noticed, the misuse of Google Advertisements to show seemingly related, however truly malicious, web sites among the many sponsored hyperlinks in Google search outcomes stands out as some of the outstanding strategies to lure victims into downloading Danabot. The preferred ploy is packing the malware with authentic software program and providing such a package deal via bogus software program websites (Determine 3) or web sites falsely promising customers to assist them discover unclaimed funds (Determine 4).
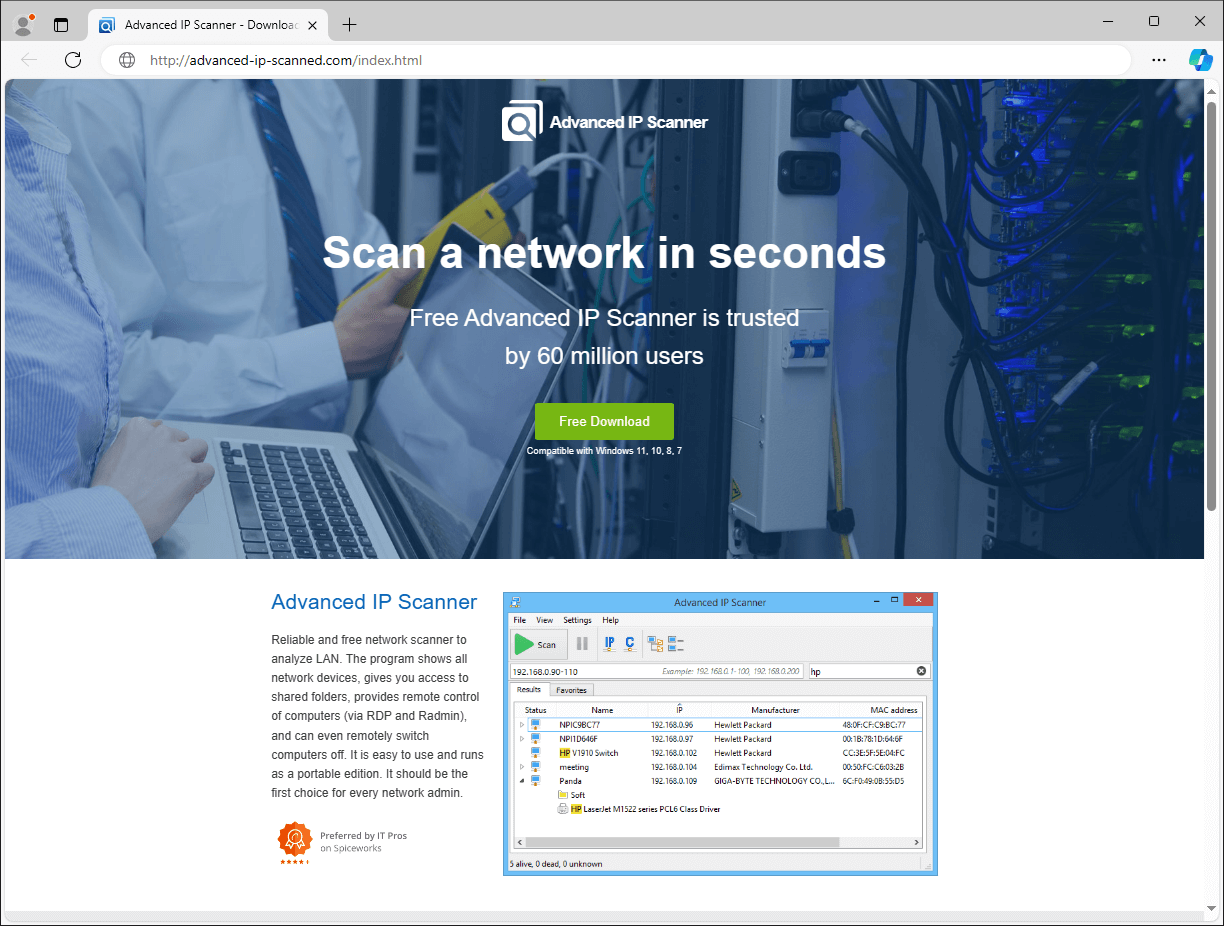
Determine 3. Faux Superior IP Scanner web site resulting in Danabot compromise

Determine 4. Faux unclaimed cash search web site
The most recent addition to those social engineering methods: misleading web sites providing options for fabricated pc points, whose solely objective is to lure the sufferer into execution of a malicious command secretly inserted into the consumer’s clipboard. An instance of such a web site resulting in downloading of Danabot in Determine 5.
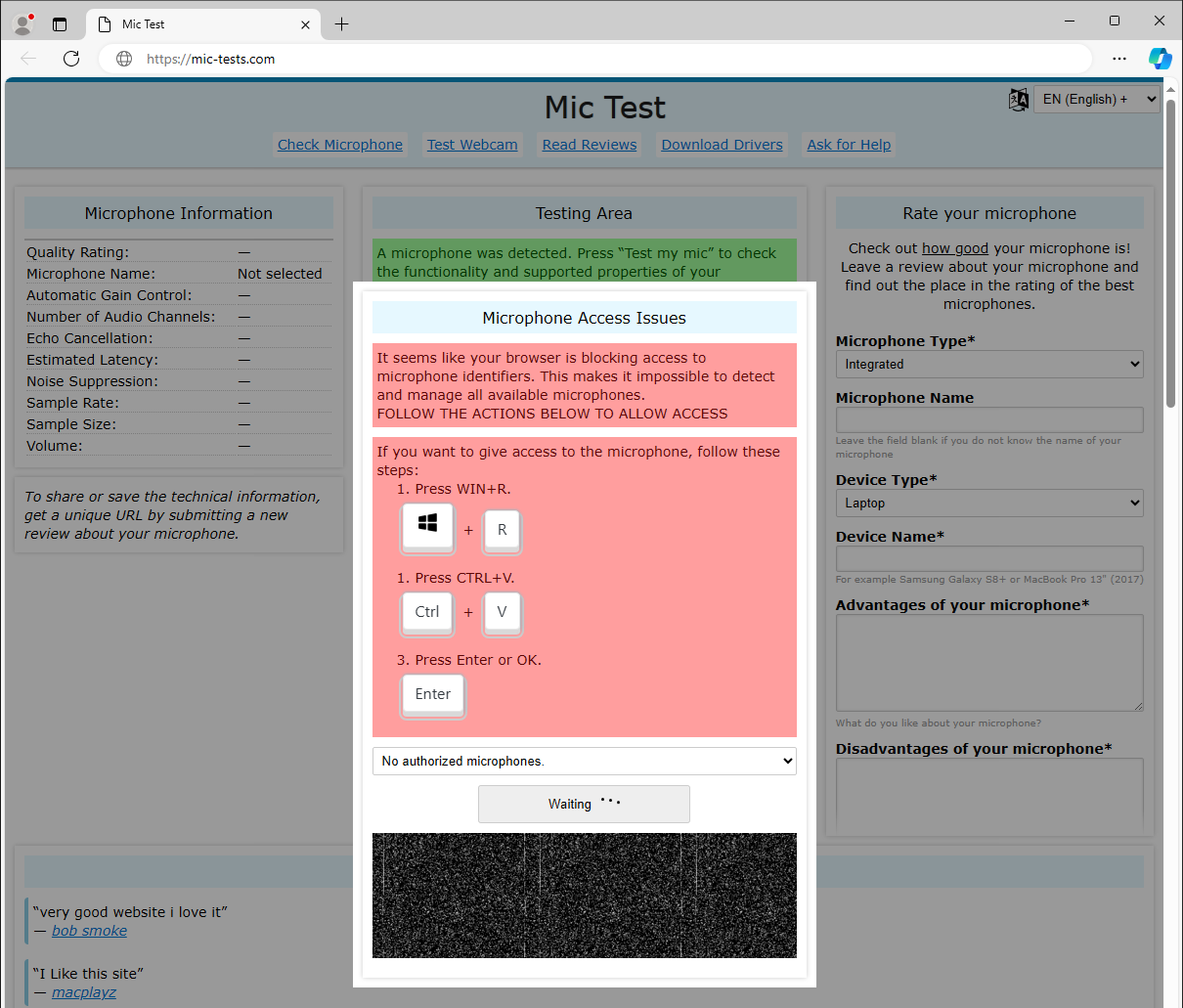
Determine 5. Web site luring the sufferer into execution of malicious command saved within the consumer’s clipboard
Infrastructure
Overview
Initially, Danabot’s authors relied on a single centralized server to handle all bots’ connections and all associates’ knowledge, corresponding to command configurations and knowledge collected from their victims. This centralized method actually had a destructive influence on that server’s efficiency and was extra vulnerable to doable disruptions. That is most likely one of many the explanation why we noticed a shift within the enterprise and infrastructure fashions in newer variations. Along with renting locations on their very own infrastructure, Danabot’s authors now supply set up of a non-public server, as marketed on their help web site, to be operated by the affiliate (Determine 6).
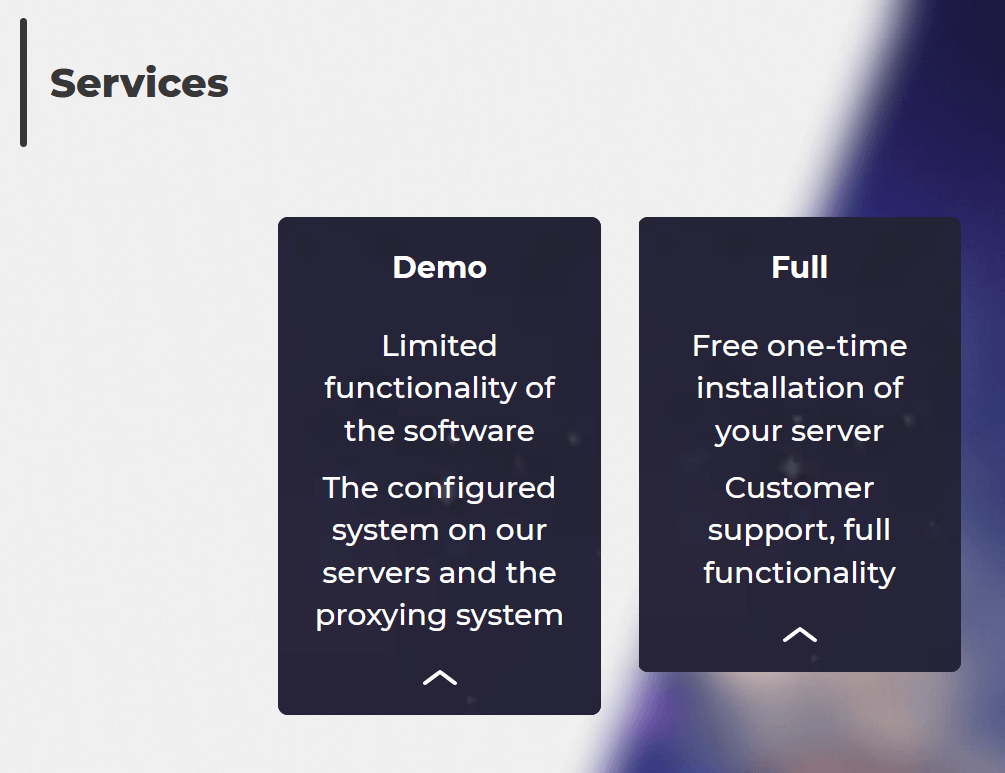
Determine 6. Fundamental providing on Danabot’s help web site
The rental choices, as supplied via an underground discussion board in July 2023, are illustrated in Determine 7.
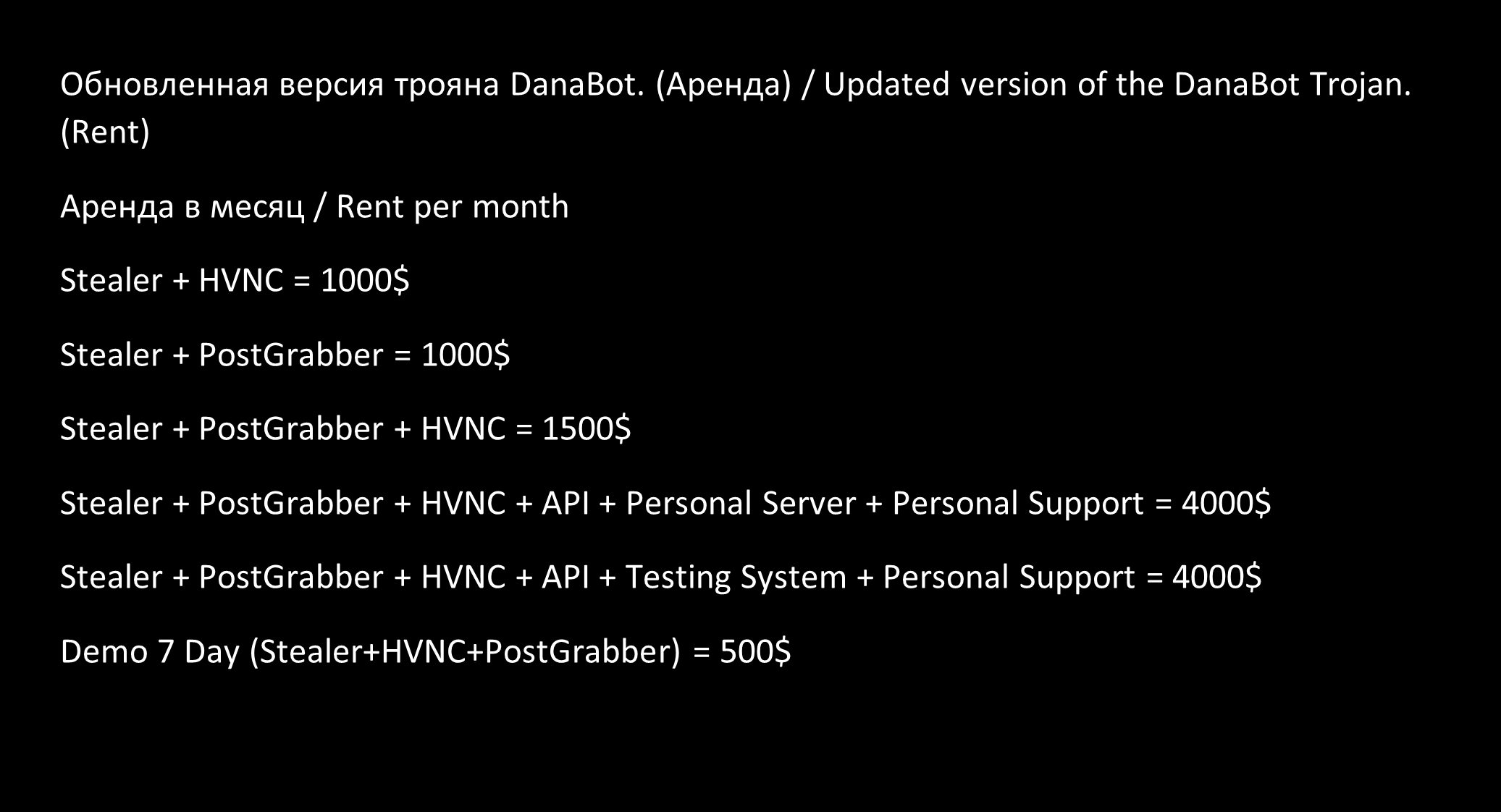
Determine 7. Worth listing for potential Danabot clients
It’s price mentioning that, primarily based on our monitoring, the rental of an account on the shared infrastructure managed by Danabot’s authors appears to be the preferred alternative for risk actors.
When associates buy a rental of one of many choices, they’re given instruments and credentials to connect with the C&C server and handle their very own botnet via an administration panel. Within the following sections, we cowl the totally different components of the everyday toolset.
C&C server utility
The standalone server utility comes within the type of a DLL file and acts because the mind of the botnet. It’s put in on a Home windows server and makes use of a MySQL database for knowledge administration. Bots connect with this server to transmit stolen knowledge and obtain instructions issued by associates. Associates connect with this server by way of the administration panel utility to handle their botnet. This C&C server utility is offered for native set up just for associates paying for the upper tier private server choice. Associates who select to function their botnets on Danabot’s infrastructure as an alternative are given connection particulars to the C&C server already arrange there, and don’t have to host their very own C&C server.
Administration panel
The administration panel, displayed in Determine 8, is within the type of a GUI utility, and represents an important instrument from the botnet operator’s perspective. It permits the affiliate to connect with the C&C server and carry out duties corresponding to:
handle bots and retrieve statistics of the botnet,
problem numerous instructions and superior configuration for bots,
conveniently view and export knowledge gathered from victims,
handle the notification system and arrange alerts on occasions triggered by bots,
generate new Danabot builds, and
arrange a sequence of proxy servers for communication between the bots and the C&C server.
We offer extra particulars and examples of probably the most fascinating capabilities of the administration panel within the upcoming sections.
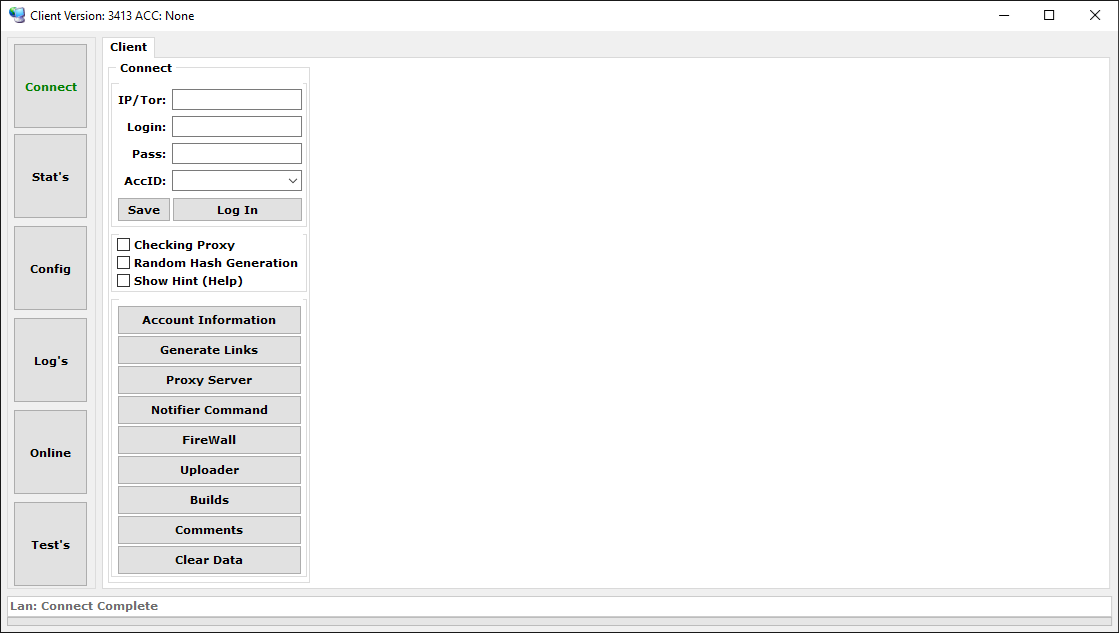
Determine 8. Administration panel overview
Backconnect instrument
One other essential instrument for administration is the standalone utility that permits botnet operators to remotely connect with and management their on-line bots. Obtainable actions for distant management, as seen within the instrument, are illustrated in Determine 9. Most likely probably the most fascinating options for cybercriminals are the flexibility to see and management the sufferer’s pc by way of a distant desktop connection and to carry out reconnaissance of the file system utilizing the built-in file supervisor.
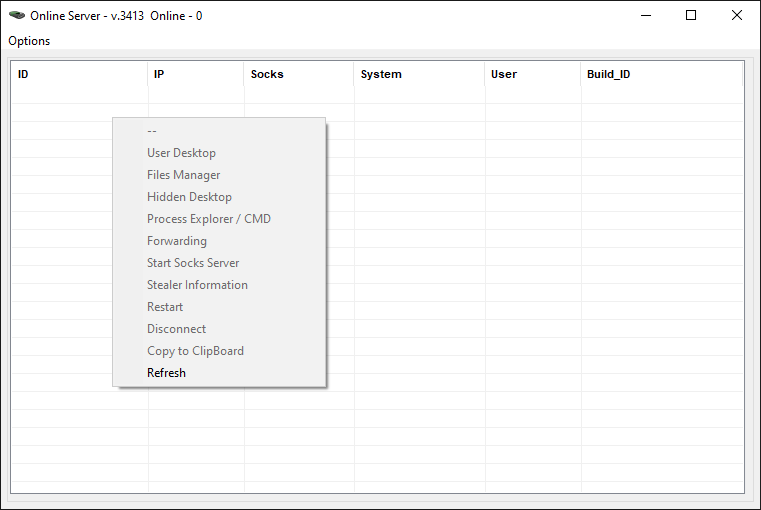
Determine 9. Options of the backconnect utility
Proxy server utility
Bots sometimes don’t connect with the principle C&C server straight, however moderately use a sequence of proxies to relay the visitors and conceal the situation of the true backend C&C. To facilitate this technique, Danabot’s authors present a proxy server utility, out there for each Home windows and Linux methods. Determine 10 exhibits the utilization message from the Linux model of this easy proxy server utility. Moreover utilizing proxies, bots may be configured to speak with the server via the Tor community in case all proxy chains turn into unavailable. An non-compulsory downloadable Tor module is then used for such communication.
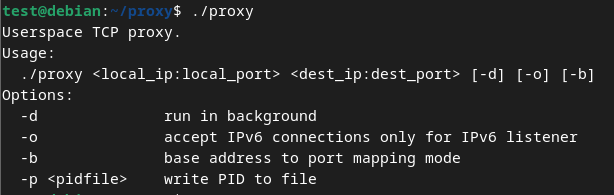
Determine 10. Utilization message from the Linux model of the proxy server utility
Associates additionally regularly make the most of this proxy server utility as an middleman between their administration panel and the C&C server to additional improve their anonymity. When every part is put collectively, the everyday infrastructure could look as proven in Determine 11.
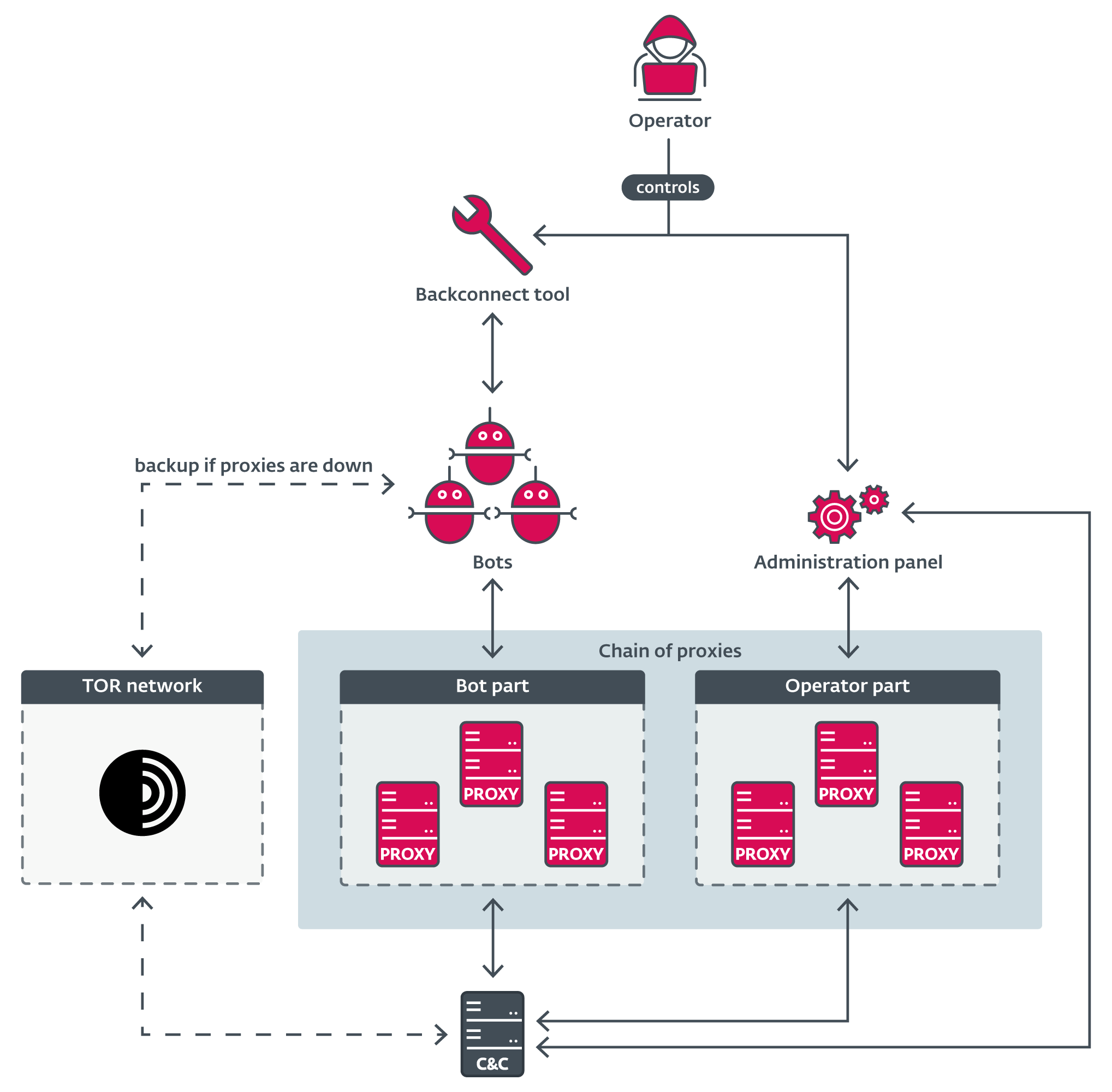
Determine 11. Instance of typical Danabot infrastructure
Internals
Communication
Danabot employs its personal proprietary C&C communication protocol with its knowledge encrypted utilizing AES-256. Generated AES session keys, distinctive for each message, are then additional encrypted utilizing RSA key pairs, securing the entire communication. It’s price mentioning that there have been a number of updates to the communication protocol and the packet construction over time.
The present packet knowledge construction of the everyday command, earlier than it’s encrypted, appears as proven in Desk 1 . We wish to level out that a lot of the fields are solely used in the course of the first request within the communication loop to authenticate the bot, and are left unset within the subsequent instructions.
Desk 1. Packet construction utilized in Danabot communication
Offset
Measurement (bytes)
Description
0x00
0x04
Measurement of the packet.
0x04
0x08
Random worth.
0x0C
0x08
Sum of the 2 values above.
0x14
0x04
Account ID used to distinguish associates within the earlier variations. This subject accommodates a random worth in newer variations.
0x18
0x04
Command.
0x1C
0x04
Subcommand.
0x20
0x04
Danabot model.
0x24
0x04
IsUserAdmin flag.
0x28
0x04
Course of integrity stage.
0x2C
0x04
OS structure x86/x64.
0x30
0x04
Encoded Home windows model.
0x34
0x04
Time zone bias as a DWORD worth.
0x38
0x04
Unknown bytes; set to 0 within the present variations.
0x3C
0x04
Tor lively flag.
0x40
0x04
Unknown bytes; set to 0 within the present variations.
0x44
0x18
Padding null bytes.
0x5C
0x21
Bot ID Delphi string (a string preceded by a size byte).
0x7D
0x21
Construct ID hardcoded Delphi string.
0x9E
0x21
MD5 checksum of concatenated Account ID, Bot ID, and Construct ID strings.
0xBF
0x29
Command dependent string utilized in some instructions complemented by its CRC-32 and a string dimension.
0xE8
0xDF
Padding null bytes.
The latest variations of Danabot additionally add, to additional disguise its communication, a random quantity of seemingly junk bytes to the top of the packet construction earlier than it’s encrypted. It’s price mentioning that Danabot authors don’t all the time observe one of the best coding practices and the addition of this random variety of bytes was accomplished by resizing of the unique reminiscence buffer allotted to carry the packet construction as an alternative of clearing or initializing this newly acquired area. This led to unintentionally together with surrounding reminiscence areas of the method into the information packet being despatched from the bot to the server and, extra importantly, vice versa. These appended reminiscence areas captured and decrypted from the server-to-bot communication typically contained fascinating info from the server’s course of reminiscence and gave researchers priceless perception into Danabot’s infrastructure and its customers. This bug was launched in 2022 and was fastened within the newest variations of Danabot in February 2025.
Additional particulars concerning the communication and its encryption had been already coated by numerous researchers, and we received’t dive into it extra on this blogpost.
Builds
Botnet operators have a number of choices for producing new Danabot builds to distribute to their victims. To one of the best of our information, whereas the operator could configure the construct course of and desired output via the administration panel utility, the construct course of itself is carried out on the Danabot authors’ servers. After producing the chosen construct, the operator receives obtain hyperlinks for the builds and turns into answerable for their distribution in a marketing campaign.
Determine 12 exhibits an instance of a construct configuration window and out there choices, such because the C&C server listing to be configured within the last binary file, numerous obfuscation strategies, construct bitness, and so forth.
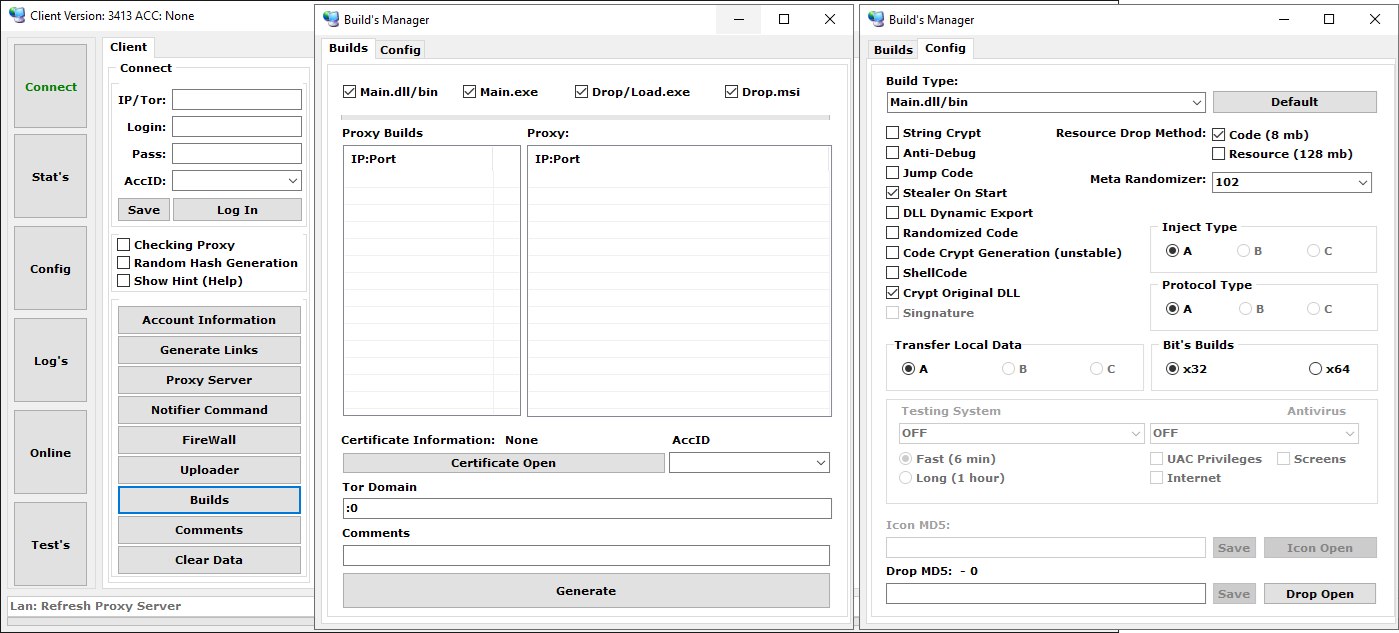
Determine 12. Construct choices menu from the Administration panel utility
Danabot at the moment presents 4 primary payload varieties, described in Desk 2.
Desk 2. Variants of accessible builds
Payload sort
Description
Important.dll
Generates a sole foremost part within the type of a DLL to be distributed and loaded by way of rundll32.exe or regsvr32.exe.
Important.exe
Generates a loader within the type of an EXE which will include the abovementioned foremost part DLL or obtain it from one of many configured C&C servers.
Drop.exe
Generates a dropper with an embedded foremost part DLL to be dropped to disk.
Drop.msi
Generates an MSI package deal with an embedded foremost part DLL to be loaded.
Instructions configuration
A botnet operator can problem a sophisticated configuration to the bots via the administration panel. Bots are then ordered to carry out numerous instructions in accordance with the directions acquired. Determine 13 exhibits an instance of such a command configuration.
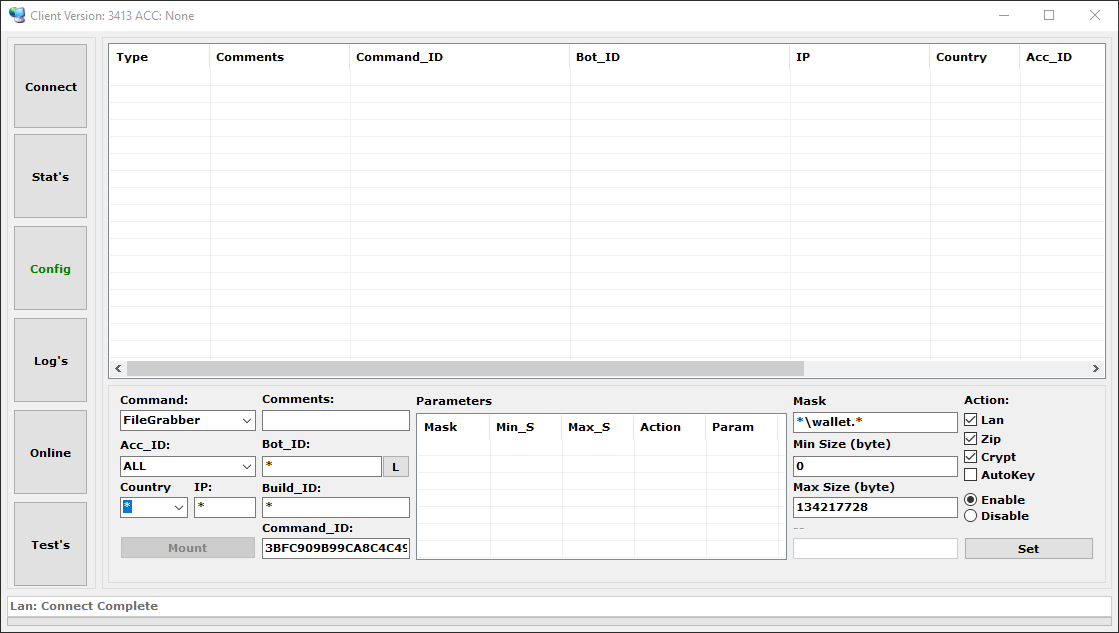
Determine 13. Dynamic configuration choices for the FileGrabber command
Desk 3 lists the out there instructions that may be issued. Every process has its personal particular choices to additional accommodate the operator’s wants.
Desk 3. Obtainable instructions
Command
Description
Video
Report a video of the chosen utility or web site.
KeyLogger
Seize keystrokes from the chosen utility.
PostFilter
Seize info from sure web sites’ types.
WebInject
Enable Zeus-like webinjects on sure loaded web sites to change their operate.
Redirect
Enable redirection of sure URLs.
Block
Block entry to configured URLs.
Screens
Take screenshots of a specific utility or web site at sure intervals.
Alerts
Enable notifications to be despatched to a specific Jabber account on a configurable occasion.
Uninstall
Uninstall the bot from the system.
UAC
Present help for privilege escalation.
FileGrabber
Enable sure recordsdata to be uploaded to the C&C if discovered on the sufferer’s arduous disk.
TorActive
Allow loading of a Tor module and permit connection by way of the Tor community if all C&C servers are inaccessible.
Stealer
Allow/disable the stealer performance and set its replace interval.
TimeOut
Set interval for the bot to contact its C&C server.
Set up
Configure the bot’s set up on the system and its persistence.
Exclusion
Set exclusions in Home windows Defender or Home windows Firewall for a specific course of.
ConfigSave
Save the bot’s configuration earlier than its termination.
HideProcess
Cover the bot’s course of.
CoreProtect
Enable the principle part to be injected into an extra course of.
Extra payloads
Danabot additionally offers the potential to obtain and execute additional executable recordsdata. This function permits the botnet operator to configure the set up of extra malware to the compromised system, as talked about earlier. Determine 14 exhibits out there choices for this function within the administration panel utility.
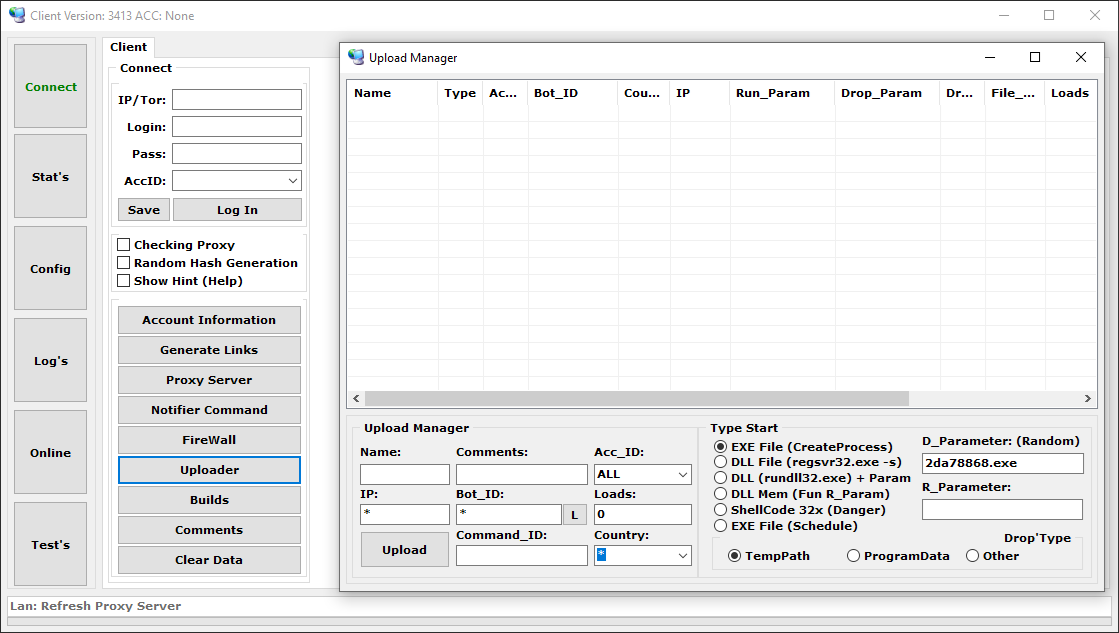
Determine 14. Choices for an extra payload configuration
Conclusion
Danabot is a large-scale MaaS operation distributing a big selection of instruments for the malware associates’ disposal. Our investigation of this infostealer, which began in 2018, resulted within the evaluation of Danabot’s toolset supplied on this blogpost. The efforts of the authorities and a number of other cybersecurity firms, ESET included, led to the disruption of the malware’s infrastructure. It stays to be seen whether or not Danabot can recuperate from the takedown. The blow will, nonetheless, certainly be felt, since legislation enforcement managed to unmask a number of people concerned within the malware’s operations.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis presents non-public APT intelligence experiences and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
Recordsdata
SHA-1
Filename
Detection
Description
6D361CD9ADBF1630AF7B323584168E0CBD9315FB
N/A
Win32/Spy.Danabot.X
Loader of the principle part (model 4006).
A7475753CB865AEC8DC4A6CEA27F2AA594EE25E8
N/A
Win32/Spy.Danabot.O
Important part (model 4006).
787EAB54714F76099EC350E029154ADFD5EDF079
N/A
Win32/Spy.Danabot.AC
Dropper part (model 3272).
17B78AD12B1AE1C037C5D39DBE7AA0E7DE4EC809
1c0e7316.exe
MSIL/Kryptik.AMBV
Lockbit payload (variant Black) distributed by Danabot.
Community
IP
Area
Internet hosting supplier
First seen
Particulars
212.18.104(.)245
N/A
GLOBAL CONNECTIVITY SOLUTIONS LLP
2025‑03‑25
Danabot proxy C&C server
212.18.104(.)246
N/A
GLOBAL CONNECTIVITY SOLUTIONS LLP
2025‑03‑25
Danabot proxy C&C server
34.16.215(.)110
N/A
Google LLC
2024‑10‑10
Danabot proxy C&C server
34.65.116(.)208
N/A
Google LLC
2024‑10‑10
Danabot proxy C&C server
34.168.100(.)35
N/A
Google LLC
2024‑11‑27
Danabot proxy C&C server
N/A
advanced-ip-scanned.com
N/A
2023‑08‑21
Misleading web site utilized in Danabot distribution
N/A
gfind.org
N/A
2022‑06‑15
Misleading web site utilized in Danabot distribution
N/A
mic-tests.com
N/A
2024‑12‑07
Misleading web site utilized in Danabot distribution
MITRE ATT&CK methods
This desk was constructed utilizing model 17 of the MITRE ATT&CK framework.
Tactic
ID
Identify
Description
Useful resource Improvement
T1583.003
Purchase Infrastructure: Digital Personal Server
Danabot operators use VPS of their infrastructure.
T1583.004
Purchase Infrastructure: Server
Danabot operators purchase a number of servers for C&C communication.
T1587.001
Develop Capabilities: Malware
Danabot authors have developed customized malware instruments.
T1608.001
Stage Capabilities: Add Malware
Danabot operators add different malware to their infrastructure for additional spreading.
T1583.008
Purchase Infrastructure: Malvertising
Malvertising is a well-liked technique of Danabot distribution.
Preliminary Entry
T1566.001
Phishing: Spearphishing Attachment
Phishing is a standard technique used for distribution.
Execution
T1106
Native API
Dynamic Home windows API decision is utilized by Danabot.
T1204.001
Consumer Execution: Malicious Hyperlink
Luring customers into downloading Danabot by way of a malicious hyperlink is a well-liked distribution alternative.
T1204.002
Consumer Execution: Malicious File
Danabot is commonly distributed as a file to be opened by the consumer.
Privilege Escalation
T1548.002
Abuse Elevation Management Mechanism: Bypass Consumer Account Management
A number of strategies are utilized by Danabot to bypass Consumer Account Management.
Protection Evasion
T1027.007
Obfuscated Recordsdata or Data: Dynamic API Decision
Danabot makes use of hashing for dynamic API decision.
T1055.001
Course of Injection: Dynamic-link Library Injection
Danabot has the flexibility to inject itself into different processes.
T1218.007
System Binary Proxy Execution: Msiexec
An MSI package deal is likely one of the doable distribution strategies.
T1218.010
System Binary Proxy Execution: Regsvr32
regsvr32.exe can be utilized to execute the principle Danabot module.
T1218.011
System Binary Proxy Execution: Rundll32
rundll32.exe can be utilized to execute the principle Danabot module.
T1656
Impersonation
Danabot makes use of impersonation in its phishing campaigns.
Credential Entry
T1555.003
Credentials from Password Shops: Credentials from Net Browsers
Danabot has the flexibility to steal numerous knowledge from browsers.
T1539
Steal Net Session Cookie
Danabot can steal cookies.
Discovery
T1010
Utility Window Discovery
Danabot may be configured to steal knowledge primarily based on the lively window.
T1217
Browser Data Discovery
Information, corresponding to searching historical past, may be gathered by Danabot.
T1083
File and Listing Discovery
Danabot may be configured to collect sure recordsdata from the compromised file system.
T1057
Course of Discovery
Danabot can enumerate working processes on a compromised system.
Lateral Motion
T1021.001
Distant Companies: Distant Desktop Protocol
Danabot operators can use the distant desktop module to entry compromised methods.
T1021.005
Distant Companies: VNC
VNC is likely one of the supported options for controlling a compromised system.
Assortment
T1056.001
Enter Seize: Keylogging
Keylogging is one in all Danabot’s options.
T1560.002
Archive Collected Information: Archive by way of Library
Danabot can use zlib and ZIP to compress collected knowledge.
T1560.003
Archive Collected Information: Archive by way of Customized Technique
Collected knowledge is additional encrypted utilizing AES and RSA cyphers.
T1119
Automated Assortment
Danabot may be configured to gather numerous knowledge robotically.
T1185
Browser Session Hijacking
Danabot can carry out AitB assaults by way of webinjects.
T1115
Clipboard Information
Danabot can acquire info saved within the clipboard.
T1005
Information from Native System
Danabot may be configured to seek for delicate knowledge on a neighborhood file system.
T1113
Display screen Seize
Danabot may be configured to seize screenshots of functions and internet pages.
T1125
Video Seize
Danabot can seize video from the compromised system.
Command and Management
T1132.001
Information Encoding: Customary Encoding
Visitors between bot and C&C server is compressed utilizing ZIP and zlib.
T1001.001
Information Obfuscation: Junk Information
Junk bytes are added to knowledge to be despatched between bot and C&C server.
T1573.001
Encrypted Channel: Symmetric Cryptography
AES-256 is used as one of many encryption strategies of C&C communication.
T1573.002
Encrypted Channel: Uneven Cryptography
RSA is used as one of many encryption strategies of C&C communication.
T1008
Fallback Channels
The Tor module can be utilized as a fallback channel in case all common C&C servers should not responding.
T1095
Non-Utility Layer Protocol
Danabot makes use of its personal customized TCP protocol for communication.
T1571
Non-Customary Port
Danabot can talk on any port.
T1090.003
Proxy: Multi-hop Proxy
A series of proxy servers is used to cover the situation of the true C&C server.
T1219
Distant Entry Software program
Danabot has help for distant entry.
Exfiltration
T1020
Automated Exfiltration
Danabot may be configured to collect numerous knowledge from a compromised system.
T1030
Information Switch Measurement Limits
Danabot may be configured to keep away from sending giant recordsdata from a compromised system.
T1041
Exfiltration Over C2 Channel
Gathered knowledge is exfiltrated via normal C&C communication.
Influence
T1498
Community Denial of Service
Danabot employed a module to carry out numerous DDoS assaults.