A major provide chain assault hit NPM after 16 in style Gluestack ‘react-native-aria’ packages with over 950,000 weekly downloads had been compromised to incorporate malicious code that acts as a distant entry trojan (RAT).
BleepingComputer decided that the compromise started on June 6 at 4:33 PM EST, when a brand new model of the react-native-aria/focus package deal was printed to NPM. Since then, 16 of the 20 Gluestack react-native-aria packages have been compromised on NPM, with the risk actors publishing a brand new model as just lately as two hours in the past.
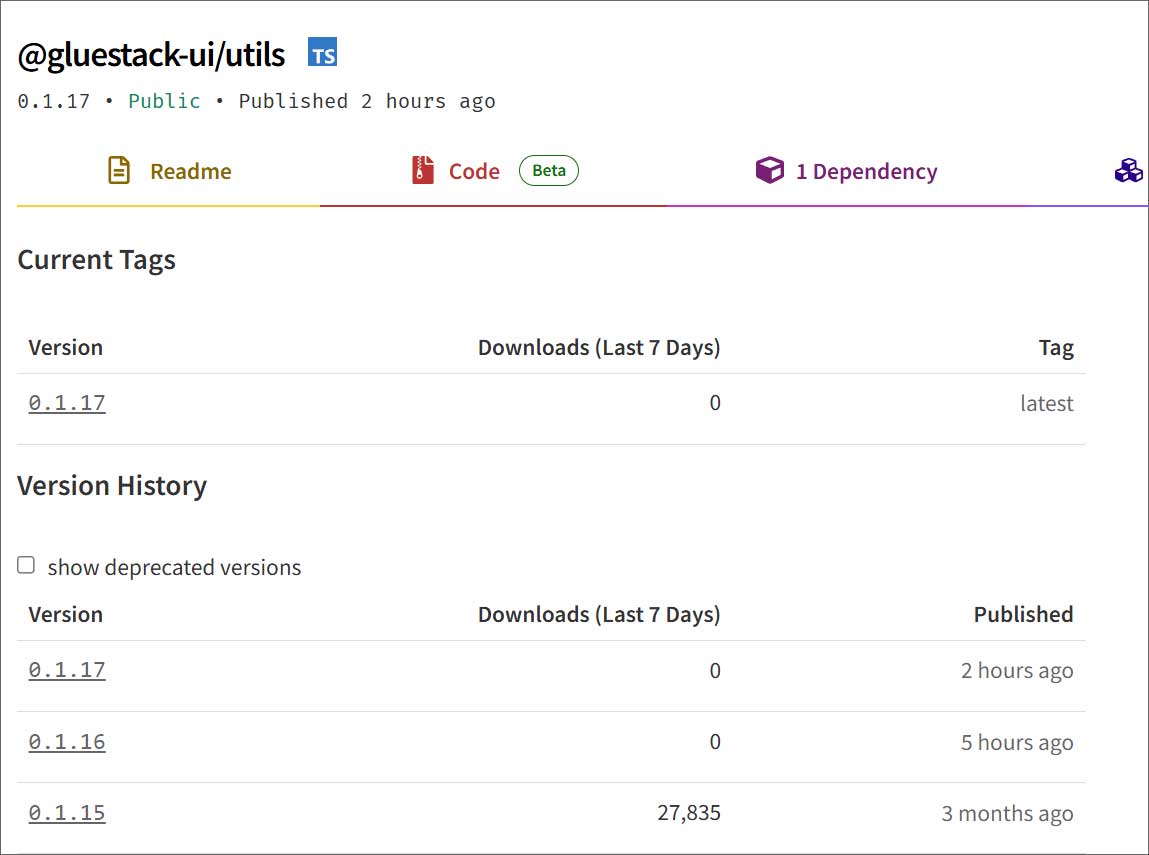 Ongoing compromise of NPM packages
Ongoing compromise of NPM packages
Supply: BleepingComputer
The provision chain assault was found by cybersecurity agency Aikido Safety, who found obfuscated code injected into the lib/index.js file for the next packages:
Package deal Identify
Model
Weekly Downloads
react-native-aria/button
0.2.11
51,000
react-native-aria/checkbox
0.2.11
81,000
react-native-aria/combobox
0.2.10
51,000
react-native-aria/disclosure
0.2.9
3
react-native-aria/focus
0.2.10
100,000
react-native-aria/interactions
0.2.17
125,000
react-native-aria/listbox
0.2.10
51,000
react-native-aria/menu
0.2.16
22,000
react-native-aria/overlays
0.3.16
96,000
react-native-aria/radio
0.2.14
78,000
react-native-aria/change
0.2.5
477
react-native-aria/toggle
0.2.12
81,000
react-native-aria/utils
0.2.13
120,000
gluestack-ui/utils
0.1.17
55,000
react-native-aria/separator
0.2.7
65
react-native-aria/slider
0.2.13
51,000
These packages are very fashionable, with roughly 960,000 weekly downloads, making this a provide chain assault that would have widespread penalties.
The malicious code is closely obfuscated and is appended to the final line of supply code within the file, padded with many areas, so it isn’t simply noticed when utilizing the code viewer on the NPM web site.
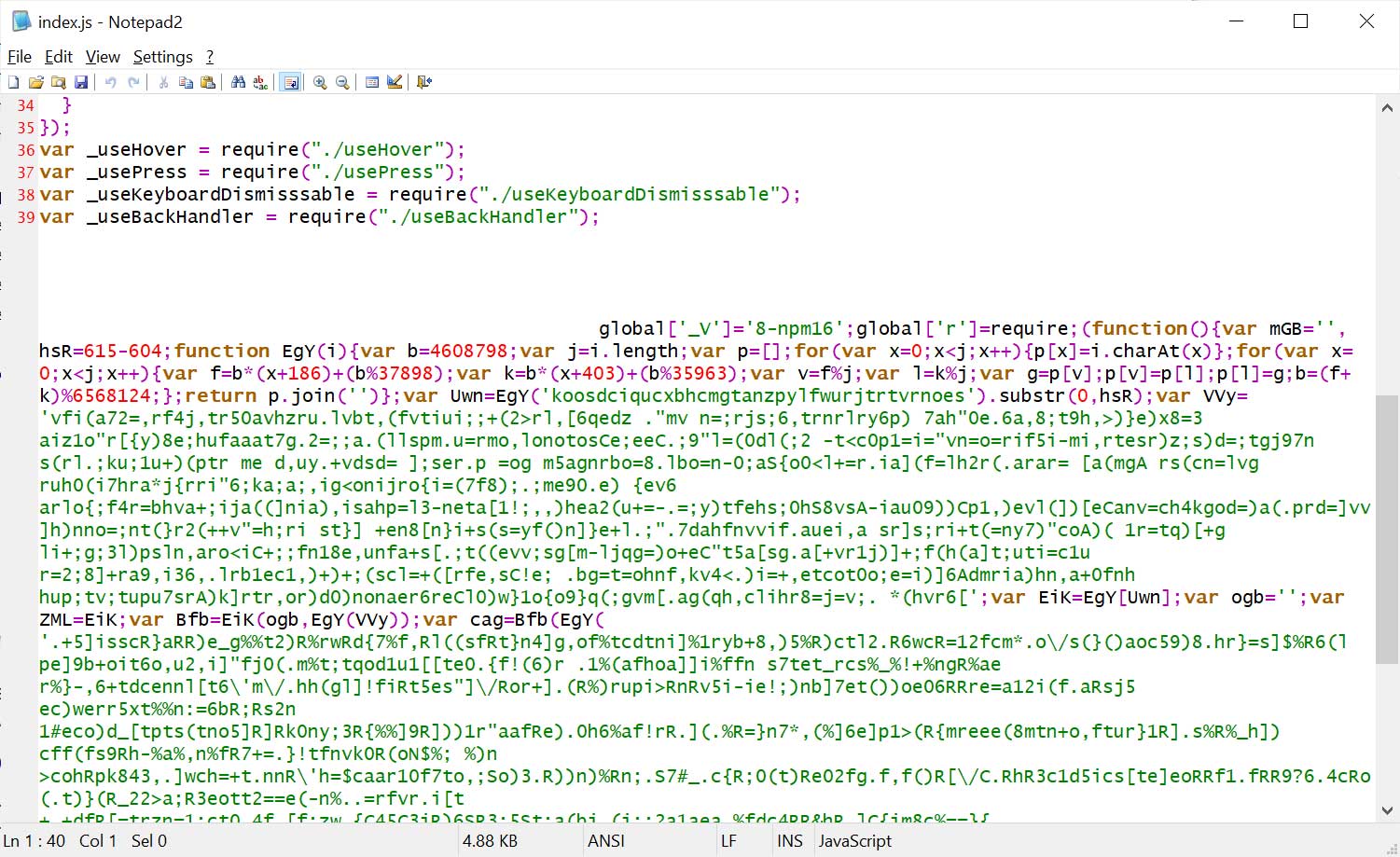 Malicious code added to finish of index.js file
Malicious code added to finish of index.js file
Supply: BleepingComputer
Aikido advised BleepingComputer that the malicious code is almost an identical to a distant entry trojan in one other NPM compromise they found final month.
The researcher’s evaluation of the earlier marketing campaign explains that the distant entry trojan will connect with the attackers’ command and management server and obtain instructions to execute.
These instructions embrace:
cd – Change present working listing
ss_dir – Reset listing to script’s path
ss_fcd: – Pressure change listing to
ss_upf:f,d – Add single file f to vacation spot d
ss_upd:d,dest – Add all recordsdata beneath listing d to vacation spot dest
ss_stop – Units a cease flag to interrupt present add course of
Some other enter – Handled as a shell command, executed by way of child_process.exec()
The trojan additionally performs Home windows PATH hijacking by prepending a pretend Python path (%LOCALAPPDATApercentProgramsPythonPython3127) to the PATH setting variable, permitting the malware to silently override reliable python or pip instructions to execute malicious binaries.
Aikido sercurity researcher Charlie Eriksen has tried to contact Gluestack in regards to the compromise by creating GitHub points on every of the mission’s repositories, however there has not been any response right now.
“No response from package deal maintainers (it is morning on a saturday within the US which is prob precisely why its taking place now),” Arkido advised BleepingComputer.
“NPM we have now contacted and reported every package deal, it is a course of that normally takes a number of days for NPM to handle although.”
Aikido additionally attributes this assault to the identical risk actors who compromised 4 different NPM packages earlier this week named biatec-avm-gas-station, cputil-node, lfwfinance/sdk, and lfwfinance/sdk-dev.
BleepingComputer reached out to Gluestack in regards to the compromised packages however has not obtained a reply right now.
Patching used to imply advanced scripts, lengthy hours, and countless fireplace drills. Not anymore.
On this new information, Tines breaks down how trendy IT orgs are leveling up with automation. Patch quicker, scale back overhead, and concentrate on strategic work — no advanced scripts required.





