On this weblog you’ll hear straight from Microsoft’s Deputy Chief Data Safety Officer (CISO) for Azure and working methods, Mark Russinovich, about how Microsoft operationalized safety sturdiness at scale. This weblog is a part of an ongoing collection the place our Deputy CISOs share their ideas on what’s most necessary of their respective domains. On this collection you’re going to get sensible recommendation and forward-looking commentary on the place the trade goes, in addition to ways you need to begin (and cease) deploying, and extra.
In late 2023, Microsoft launched its most bold safety transformation up to now, the Microsoft Safe Future Initiative (SFI). An initiative with the equal of 34,000 engineers working throughout 14 product divisions, supporting greater than 20,000 cloud companies on 1.2 million Azure subscriptions, the scope is huge. These companies function on 21 million compute nodes, protected by 46.7 million certificates, and developed throughout 134,000 code repositories.
At Microsoft’s scale, the true problem isn’t simply delivery safety fixes—it’s guaranteeing they’re routinely enforced by the platform, with no additional carry from engineers. This work aligns on to our Safe by Default precept. Sturdy safety is about constructing methods that apply fixes proactively, uphold requirements over time, and engineering groups can deal with innovation relatively than rework. That is the following frontier in safety resilience.
Why “staying safe” is tougher than getting there
When SFI started, Microsoft made fast progress: groups addressed vulnerabilities, met key efficiency indicators (KPIs), and turned dashboards inexperienced. Over time, sustaining these positive factors proved difficult, as some fixes required reinforcement and recurring patterns like misconfigurations and legacy points started to re-emerge in new initiatives—highlighting the necessity for sturdy, long-term safety practices.
The sample was clear: safety enhancements weren’t sturdy.
Whereas key milestones had been efficiently achieved, there have been cases the place we didn’t have a clearly outlined possession or built-in options to routinely maintain safety baselines. Enforcement mechanisms diversified, resulting in inconsistencies in how safety requirements had been upheld. As assets shifted post-delivery, this created a danger of baseline drift over time.
Transferring ahead, we realized that our groups want to ascertain specific possession, standardize enforcement design, and embed automation on the platform degree as a result of it’s important to make sure long-term resilience, scale back operational burden, and stop regression.
Engineering for endurance: The making of Microsoft’s sturdiness technique
To remodel safety from a reactive effort into a permanent functionality, Microsoft launched a company-wide initiative to operationalize safety sturdiness at scale. The outcome was the creation of the Safety Sturdiness Mannequin, anchored within the precept to “Begin Inexperienced, Get Inexperienced, Keep Inexperienced, and Validate Inexperienced.” This framework will not be a slogan—it’s a foundational shift in how Microsoft engineers construct, implement, and maintain safe methods throughout the enterprise.
On the core of this effort are Sturdiness Architects—devoted Architects embedded inside every division who act as stewards of persistent safety. These people champion a “fix-once, fix-forever” mindset by implementing possession and driving accountability throughout groups. One instance that catalyzed this effort concerned cross-tenant entry dangers by means of Passthrough Authentication. On this case, customers with out presence in a goal tenant might authenticate by means of passthrough mechanisms, unintentionally breaching tenant boundaries. The mitigation initially lacked sturdiness and resurfaced till possession and enforcement had been systemically addressed.
Microsoft additionally applies a lifecycle framework they name “Begin Inexperienced, Get Inexperienced, Keep Inexperienced, Validated Inexperienced.” New options are developed in a secure-by-default posture utilizing hardened templates, guaranteeing they “Begin Inexperienced.” Legacy methods or present options are introduced into compliance by means of focused remediation efforts—that is “Get Inexperienced.” To “Keep Inexperienced,” ongoing monitoring and guardrails stop regression. Lastly, safety is verified by means of automated critiques, and government reporting—guaranteeing enduring resilience.
Automating for scale and embedding safety into engineering tradition
Recognizing that handbook safety checks can not scale throughout an enterprise of this dimension, Microsoft has closely invested in automation to forestall regressions. Instruments comparable to Azure Coverage routinely implement finest practices like encryption-at-rest or multifactor authentication throughout cloud assets. Steady scanners detect expired certificates or recognized weak packages. Self-healing scripts autocorrect deviations, closing the loop between detection and remediation.
To embed sturdiness into the operational material, evaluation cadences and government oversight play a important function. Safety KPIs are reviewed at weekly or biweekly engineering operations conferences, with Microsoft’s high management, together with the Chief Govt Officer (CEO), Govt Vice Presidents (EVPs), and engineering leaders receiving common updates. Notably, government compensation is now straight tied to safety efficiency metrics—an accountability mechanism that has pushed measurable enhancements in areas comparable to secret hygiene throughout code repositories.
Moderately than constructing fragmented options, Microsoft focuses on shared, scalable safety capabilities. For instance, to keep up a clear construct atmosphere, all new construct queues will now default to a virtualized setup. Clients is not going to have the choice to revert to the basic Artifact Processor (AP) on their very own. As soon as a construct is executed within the virtualized CloudBuild atmosphere, any beforehand allotted assets within the basic CloudBuild might be both decommissioned or reassigned.
Lastly, sturdiness is now a built-in requirement at growth gates. Safety fixes should not solely remediate present points however be designed to endure. Groups should assign homeowners, endure gated critiques or sturdiness, and construct enforcement mechanisms. This philosophy has shifted the mindset from one-time patching to long-term resilience.
The trail to sturdy safety: A maturity framework
Sturdy safety isn’t nearly fixing vulnerabilities—it’s about guaranteeing safety holds over time. As Microsoft discovered throughout the early days of its Safe Future Initiative, lasting safety requires organizations to mature operationally, culturally, and technically. The next framework outlines the best way to evolve towards safety sturdiness at scale:
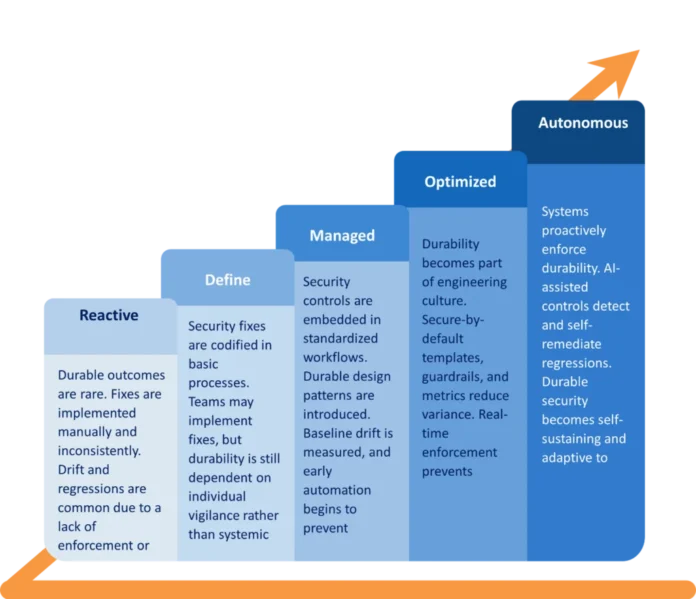
1. Levels of safety sturdiness maturity: Safety sturdiness evolves by means of distinct operational phases that replicate a company’s means to maintain and scale safe outcomes, not simply obtain them quickly.
Reactive: Sturdy outcomes are uncommon. Fixes are carried out manually and inconsistently. Drift and regressions are frequent as a result of a scarcity of enforcement or oversight.
Outline: Safety fixes are codified in fundamental processes. Groups could implement fixes, however sturdiness continues to be depending on particular person vigilance relatively than systemic assist.
Managed: Safety controls are embedded in standardized workflows. Sturdy design patterns are launched. Baseline drift is measured, and early automation begins to forestall regression.
Optimized: Sturdiness turns into a part of engineering tradition. Safe-by-default templates, guardrails, and metrics scale back variance. Actual-time enforcement prevents safety drift.
Autonomous and predictive: Techniques proactively implement sturdiness. AI-assisted controls detect and self-remediate regressions. Sturdy safety turns into self-sustaining and adaptive to alter.
2. Dimensions of safety sturdiness: To embed sturdiness throughout the enterprise, organizations should mature alongside 5 built-in dimensions:
Resilience to alter: Safety controls should stay secure whilst infrastructure, instruments, and organizational constructions evolve. This requires decoupling controls from fragile, handbook methods.
Scalability: Sturdy safety should scale effortlessly throughout increasing environments, together with new areas, companies, and group constructions—with out introducing regressions.
Automation and AI readiness: Sturdiness is dependent upon machine-powered enforcement. Handbook critiques alone can not assure persistence. AI and automation present pace, consistency, and fail-safes.
Governance integration: Sturdiness should be wired into governance platforms to supply traceability, accountability, and danger closure throughout the management lifecycle.
Sustainability: Sturdy safety options should be light-weight and operationally viable. If controls are too burdensome, groups will circumvent them, undermining long-term resilience.
3. Key milestones in safety sturdiness evolution: Microsoft’s implementation of sturdy safety revealed important transformation factors that sign organizational maturity:
Set up sturdy safety baselines (identification hygiene, patching, config hardening).
Implement controls by means of automated coverage and self-healing.
Construct durability-aware platforms like Govern Threat Clever Platform (GRIP) to trace regressions and closure loops.
Embed sturdiness critiques into engineering checkpoints and danger possession cycles.
Drive a sturdiness mindset throughout groups—from growth to operations.
Create suggestions loops to guage what holds and what regresses over time.
Deploy AI-powered brokers to detect drift and provoke remediation.

Every milestone builds a stronger basis for sturdiness and aligns incentives with sustained safety excellence.
4. Measuring safety sturdiness: Monitoring the stickiness of safety work requires a shift from conventional danger metrics to durability-focused indicators. Microsoft makes use of the next to watch progress:
Share of controls enforced routinely versus manually
Baseline drift charge (how usually known-good states erode)
Imply time to regress (how shortly fixes unravel)
Quantity of self-healing actions triggered and resolved
Share of fixes that meet “by no means regress” standards
Sturdiness metadata protection in methods like GRIP (possession, standing, and closure)
Share of engineering groups built-in into sturdiness reporting cadences
Outcomes: From short-term wins to sustained positive factors
By February 2025, the sturdiness push resulted in:
100% multi-factor authentication (MFA) enforcement or legacy protocol removing remained secure for months.
Groups use real-time dashboards to catch any KPI dips—addressing them earlier than they spiral.
The place earlier enhancements pale, new ones held agency—validating the sturdiness mannequin.
Classes for any enterprise
Microsoft’s journey affords beneficial takeaways for organizations of all sizes.
Sturdiness requires programmatic assist
Safety doesn’t persist accidentally. It wants:
Roles for sturdiness and accountability.
Sturdy design patterns.
Empowering applied sciences (automation and coverage enforcement).
Common management and architect critiques.
Standardized workflows.
Groups throughout safety, growth, and operations should be aligned and coordinated—utilizing the identical metrics, instruments, and gates.
Tradition and management matter
Safety should be everybody’s job—and management should reinforce that relentlessly. At Microsoft, safety grew to become a part of efficiency critiques, government dashboards, and on a regular basis dialog.
As EVP Charlie Bell put it: “Safety is not only a function, it’s the muse.”
That mindset—mixed with constant management strain—is what transforms short-lived safety into long-term resilience.
Safety that endures
The Safe Future Initiative proves that sturdy safety is achievable—even at hyperscale.
Microsoft is exhibiting that lasting safety could be achieved by investing in:
Individuals (clear possession and champions).
Processes (repeatable metrics and critiques).
Platforms (shared tooling and automation).
The playbook isn’t only for tech giants. Any group—whether or not you’re securing 20 cloud companies or 20,000—can undertake the ideas of safety sturdiness
As a result of in immediately’s cyberthreat panorama, fixing isn’t sufficient.
Study extra with Microsoft Safety
To see an instance of the Microsoft Sturdiness Technique in motion, learn this case examine within the appendix under. Study extra in regards to the Microsoft Safety Future Initiative and our Safe by Default precept.
To be taught extra about Microsoft Safety options, go to our web site. Bookmark the Safety weblog to maintain up with our professional protection on safety issues. Additionally, comply with us on LinkedIn (Microsoft Safety) and X (@MSFTSecurity) for the most recent information and updates on cybersecurity.
Appendix:
Safety Sturdiness Case Examine
Eliminating pinned certificates: A sturdy repair for secret hygiene in MSA apps
SFI Reference: (SFI-ID4.1.3)
Initiative Proprietor: Microsoft Account (MSA) Engineering Workforce
Overview
As a part of the Safe Future Initiative (SFI), the Microsoft Account (MSA) group addressed a important weak spot recognized by means of Software program Safety Incident Response Plans (SSIRPs): the unsafe use of pinned certificates. By eliminating this legacy sample and embedding preventive guardrails, the MSA group set a brand new bar for sturdy secrets and techniques administration and safe companion onboarding.
The problem: Pinned certificates and hidden fragility
Pinned certificates had been as soon as seen as a powerful belief enforcement mechanism, guaranteeing that solely particular certificates may very well be used to ascertain connections. Nevertheless, they grew to become a safety and operational legal responsibility:
Tough to rotate: If a pinned certificates expired or was compromised, coordinating a quick and seamless substitute throughout companies was difficult.
Onboarding danger: New companies had no protected, scalable path to onboard with out replicating this fragile sample.
Lack of sturdiness: With out controls, the danger of regression and repeated misuse remained excessive.
The sturdy repair: Safe by default and enforced by design
The MSA group carried out a durability-first answer grounded in engineering enforcement and operational pragmatism:
Technique Motion Code-Stage Blocking All code paths accepting pinned certificates had been hardened to forestall adoption. Short-term Enable Lists Current apps utilizing pinned certificates had been allow-listed to forestall rapid outages. Default Deny Posture New apps are routinely blocked from utilizing pinned certificates, implementing safe defaults.
This “fix-once, fix-forever” strategy ensures the difficulty doesn’t resurface—whilst new companions onboard or methods evolve.
Sustained influence and lifecycle integration
To keep up progress and guarantee no regression, the MSA group aligned remediation with every companion’s SFI KPI milestones. Companies had been faraway from the permit checklist solely after finishing their transition, closing the loop with full compliance and operational readiness.
This work strengthened a number of Safety Sturdiness pillars:
Proprietor-enforced controls
Safety constructed into the engineering lifecycle
Classes and mannequin for the longer term
This case is a mannequin for a way Microsoft is shifting from reactive safety work to systemic, enforceable, and scalable sturdiness fashions. Moderately than patching the identical situation repeatedly, the MSA group eradicated the foundation trigger, protected the ecosystem, and created a repeatable blueprint for different dangerous cryptographic practices.
Key takeaways
Eliminating pinned certificates lowered fragility and boosted long-term resilience.
Sturdy controls had been enforced by way of code, not simply course of.
Gradual deprecation by means of companion alignment ensured no disruption.
This units a precedent for eliminating insecure patterns throughout Microsoft platforms.