A novel tapjacking approach can exploit person interface animations to bypass Android’s permission system and permit entry to delicate knowledge or trick customers into performing damaging actions, equivalent to wiping the machine.
In contrast to conventional, overlay-based tapjacking, TapTrap assaults work even with zero-permission apps to launch a innocent clear exercise on high of a malicious one, a habits that is still unmitigated in Android 15 and 16.
TapTrap was developed by a workforce of safety researchers at TU Wien and the College of Bayreuth (Philipp Beer, Marco Squarcina, Sebastian Roth, Martina Lindorfer), and might be offered subsequent month at the USENIX Safety Symposium.
Nevertheless, the workforce has already revealed a technical paper that outlines the assault and a web site that summarizes a lot of the particulars.
How TapTrap works
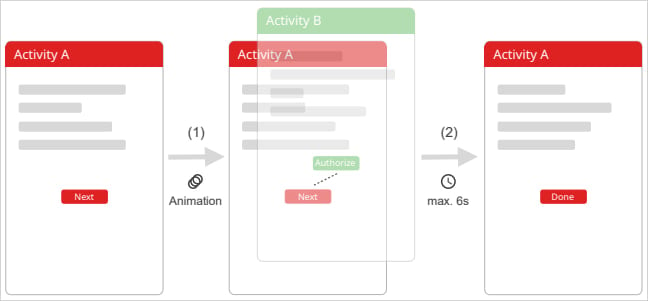
TapTrap abuses the way in which Android handles exercise transitions with customized animations to create a visible mismatch between what the person sees and what the machine truly registers.
A malicious app put in on the goal machine launches a delicate system display screen (permission immediate, system setting, and many others.) from one other app utilizing ‘startActivity()’ with a customized low-opacity animation.
“The important thing to TapTrap is utilizing an animation that renders the goal exercise practically invisible,” the researchers say on a web site that explains the assault.
“This may be achieved by defining a customized animation with each the beginning and ending opacity (alpha) set to a low worth, equivalent to 0.01,” thus making the malicious or dangerous exercise virtually utterly clear.
“Optionally, a scale animation might be utilized to zoom into a particular UI component (e.g., a permission button), making it occupy the total display screen and rising the prospect the person will faucet it.”
 TapTrap overview
TapTrap overview
Supply: taptrap.click on
Though the launched immediate receives all contact occasions, all of the person sees is the underlying app that shows its personal UI parts, as on high of it’s the clear display screen the person truly engages with.
Pondering they work together with the bening app, a person could faucet on particular display screen positions that correspond to dangerous actions, equivalent to an “Permit” or “Authorize” buttons on practically invisible prompts.
A video launched by the researchers demonstrates how a sport app might leverage TapTrap to allow digital camera entry for a web site through Chrome browser.
Threat publicity
To examine if TapTrap might work with functions in Play Retailer, the official Android repository, the researchers analyzed near 100,000. They discovered that 76% of them are susceptible to TapTrap as they embody a display screen (“exercise”) that meets the next situations:
might be launched by one other app
runs in the identical activity because the calling app
doesn’t override the transition animation
doesn’t anticipate the animation to complete earlier than reacting to person enter
The researchers say that animations are enabled on the newest Android model until the person disables them from the developer choices or accessibility settings, exposing the gadgets to TapTrap assaults.
Whereas growing the assault, the researchers used Android 15, the newest model on the time, however after Android 16 got here out in addition they ran some assessments on it.
Marco Squarcina instructed BleepingComputer that they tried TapTrap on a Google Pixel 8a operating Android 16 and so they can affirm that the problem stays unmitigated.
GrapheneOS, the cell working system centered on privateness and safety, additionally confirmed to BleepingComputer that the newest Android 16 is susceptible to the TapTrap approach, and introduced that the their subsequent launch will embody a repair.
BleepingComputer has contacted Google about TapTrap, and a spokesperson mentioned that the TapTrap drawback might be mitigated in a future replace:
“Android is consistently enhancing its present mitigations in opposition to tapjacking assaults. We’re conscious of this analysis and we might be addressing this difficulty in a future replace. Google Play has insurance policies in place to maintain customers protected that each one builders should adhere to, and if we discover that an app has violated our insurance policies, we take acceptable motion.”- a Google consultant instructed BleepingComputer.
Whereas cloud assaults could also be rising extra refined, attackers nonetheless succeed with surprisingly easy methods.
Drawing from Wiz’s detections throughout hundreds of organizations, this report reveals 8 key methods utilized by cloud-fluent risk actors.





