Fortinet warns that risk actors use a post-exploitation method that helps them preserve read-only entry to beforehand compromised FortiGate VPN units even after the unique assault vector was patched.
Earlier this week, Fortinet started sending emails to clients warning that their FortiGate/FortiOS units have been compromised primarily based on telemetry acquired from FortiGuard units.
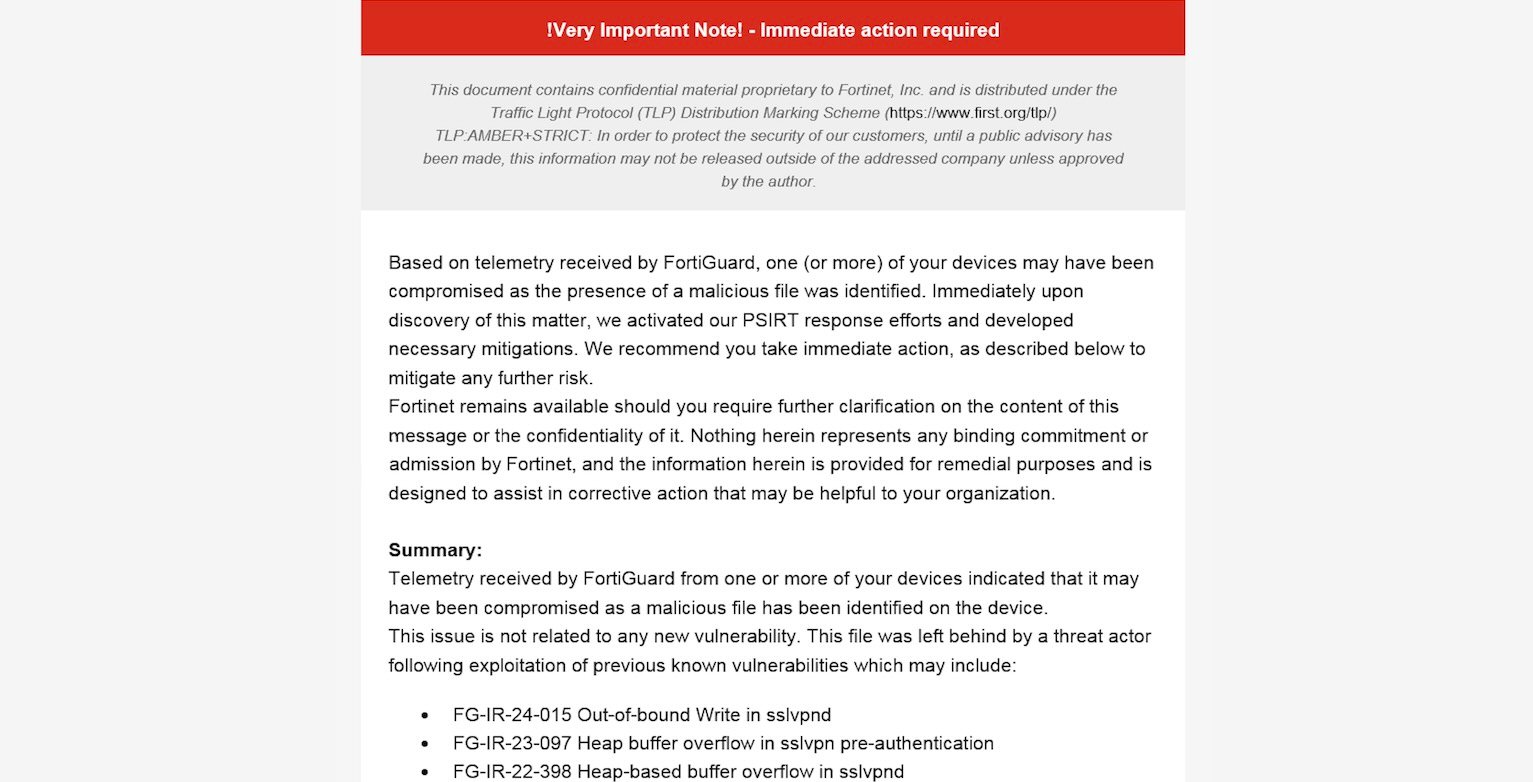
These emails have been titled “Notification of system compromise – FortiGate / FortiOS – ** Pressing motion required **,” given a TLP:AMBER+STRICT designation.
“This subject just isn’t associated to any new vulnerability. This file was left behind by a risk actor following exploitation of earlier identified vulnerabilities,” the emails stated, together with however not restricted to CVE-2022-42475, CVE-2023-27997, and CVE-2024-21762.
After BleepingComputer contacted Fortinet with questions on these emails, the corporate launched an advisory on Thursday warning about this new exploitation method. The advisory says that when the risk actors beforehand breached servers utilizing older vulnerabilities, they created symbolic hyperlinks within the language information folder to the basis file system on units with SSL-VPN enabled.
This permits them to take care of read-only entry to the basis filesystem by the publicly accessible SSL-VPN net panel even after they’re found and evicted.
“A risk actor used a identified vulnerability to implement read-only entry to susceptible FortiGate units. This was achieved through making a symbolic hyperlink connecting the person filesystem and the basis filesystem in a folder used to serve language information for the SSL-VPN. This modification occurred within the person filesystem and averted detection,” Fortinet says.
“Due to this fact, even when the client system was up to date with FortiOS variations that addressed the unique vulnerabilities, this symbolic hyperlink might have been left behind, permitting the risk actor to take care of read-only entry to information on the system’s file system, which can embody configurations.”
 Emails despatched to house owners of compromised units (BleepingComputer)
Emails despatched to house owners of compromised units (BleepingComputer)
Assaults return to early 2023
Whereas Fortinet did not reveal the precise timeframe of those assaults, the Pc Emergency Response Group of France (CERT-FR), a part of the nation’s Nationwide Company for the Safety of Data Methods (ANSSI), revealed on Thursday that this system has been utilized in an enormous wave of assaults going again to early 2023.
“CERT-FR is conscious of an enormous marketing campaign involving quite a few compromised units in France. Throughout incident response operations, CERT-FR has discovered of compromises occurring since early 2023,” CERT-FR stated.
Right now, CISA additionally suggested community defenders to report any incidents and anomalous exercise associated to Fortinet’s report back to its 24/7 Operations Middle at Report@cisa.gov or (888) 282-0870.
Within the emails despatched earlier this week, Fortinet suggested clients to right away improve their FortiGuard firewalls to the newest model of FortiOS (7.6.2, 7.4.7, 7.2.11, 7.0.17, 6.4.16) to take away the malicious information used for persistence.
Admins have been additionally urged to evaluation system configurations instantly and concentrate on discovering any sudden adjustments. This assist doc supplies additional steering on resetting probably uncovered credentials on compromised units.
CERT-FR additionally beneficial isolating compromised VPN units from the community, resetting all secrets and techniques (credentials, certificates, id tokens, cryptographic keys, and so forth), and looking for proof of lateral community motion.
Based mostly on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and the right way to defend towards them.





