Over 16,000 internet-exposed Fortinet units have been detected as compromised with a brand new symlink backdoor that enables read-only entry to delicate recordsdata on beforehand compromised units.
This publicity is being reported by risk monitoring platform The Shadowserver Basis, which initially reported 14,000 units have been uncovered.
At the moment, Shadowserver’s Piotr Kijewski instructed BleepingComputer that the cybersecurity group now detects 16,620 units impacted by the lately revealed persistence mechanism.
Final week, Fortinet warned prospects that that they had found a brand new persistence mechanism utilized by a risk actor to retain read-only distant entry to recordsdata within the root filesystem of beforehand compromised however now patched FortiGate units.
Fortinet mentioned that this was not by means of the exploitation of latest vulnerabilities however is as an alternative linked to assaults beginning in 2023 and persevering with into 2024, the place a risk actor utilized zero days to compromise FortiOS units.
As soon as they gained entry to the units, they created symbolic hyperlinks within the language recordsdata folder to the basis file system on units with SSL-VPN enabled. Because the language recordsdata are publicly accessible on FortiGate units with SSL-VPN enabled, the risk actor may browse to that folder and achieve persistent learn entry to the basis file system, even after the preliminary vulnerabilities have been patched.
“A risk actor used a recognized vulnerability to implement read-only entry to susceptible FortiGate units. This was achieved by way of making a symbolic hyperlink connecting the consumer filesystem and the basis filesystem in a folder used to serve language recordsdata for the SSL-VPN. This modification passed off within the consumer filesystem and averted detection,” Fortinet mentioned.
“Subsequently, even when the client gadget was up to date with FortiOS variations that addressed the unique vulnerabilities, this symbolic hyperlink might have been left behind, permitting the risk actor to take care of read-only entry to recordsdata on the gadget’s file system, which can embrace configurations.”
This month, Fortinet started notifying prospects privately by e mail about FortiGate units detected by FortiGuard as being compromised with this symlink backdoor.
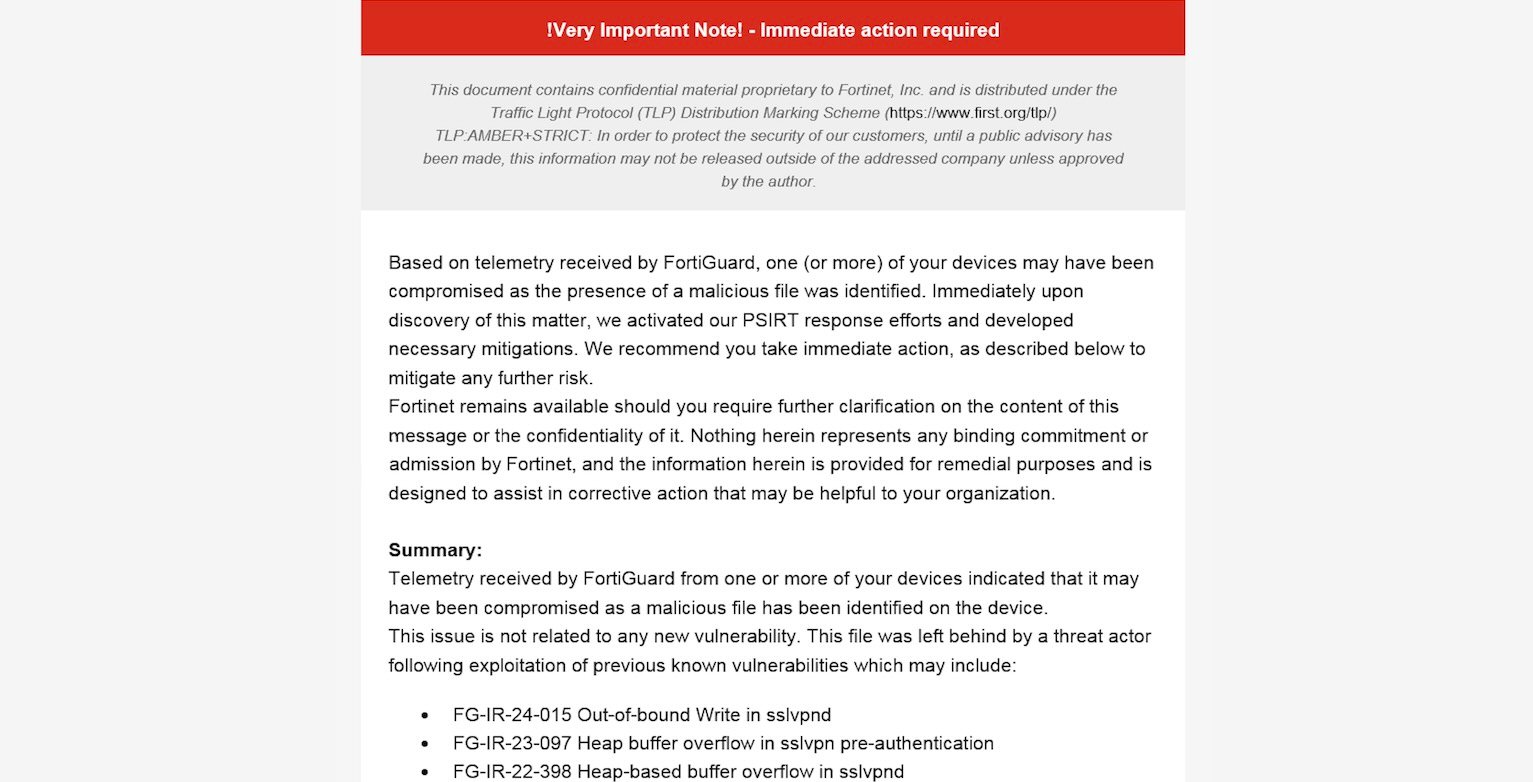 Emails despatched to house owners of compromised units
Emails despatched to house owners of compromised units
Supply: BleepingComputer
Fortinet has launched an up to date AV/IPS signature that may detect and take away this malicious symbolic hyperlink from compromised units. The most recent model of the firmware has additionally been up to date to detect and take away the hyperlink. The replace additionally prevents unknown recordsdata and folders from being served by the built-in webserver.
Lastly, if a tool was detected as compromised, it’s doable that the risk actors had entry to the newest configuration recordsdata, together with credentials.
Subsequently, all credentials ought to be reset, and admins ought to comply with the opposite steps in this information.




