Lately, hackers do not break in — they log in. Utilizing legitimate credentials, cybercriminals bypass safety techniques whereas showing professional to monitoring instruments.
And the issue is widespread; Google Cloud reviews that weak or nonexistent credential safety facilitates 47% of cloud breaches, whereas IBM X-Drive attributes practically one-third of world cyberattacks to account compromises.
So what does this imply on your group’s defenses?
Right here’s what that you must learn about the way to shield your techniques from credential-based assaults, what to do when prevention fails, and why scanning your Energetic Listing for compromised passwords ought to be part of your safety technique.
Why credential-based assaults are hackers’ most well-liked methodology
Cybercriminals favor credential-based assaults for a number of causes:
They’re straightforward to execute: Credential-based assaults are comparatively easy to deploy in comparison with extra complicated zero-day exploits.
They’re extremely profitable: With customers recycling the identical password throughout a number of accounts, it’s simpler for attackers to realize widespread entry; one set of keys can unlock many doorways.
They’ve a low detection danger: As a result of they use legitimate credentials for his or her exploits, hackers can mix in with regular visitors, permitting them to keep away from safety alerts.
They’re low-cost: Credential-based assaults require minimal sources however can yield substantial rewards. Hackers can simply (and inexpensively) purchase a set of stolen credentials on the darkish net, then use free automated instruments to check the credentials throughout a number of techniques.
They’re versatile: Credential-based assaults can be utilized wherever credentials are wanted, which means hackers have a number of potential entry factors — from net purposes to cloud companies.
Why organizations develop into targets
May your group be a sexy goal for credential-based hackers? In case you have any of those safety gaps, your techniques could also be extra weak than you suppose. Right here’s what makes organizations prime targets:
Weak password insurance policies create an open invitation for attackers to simply guess or crack credentials by automated instruments and customary password lists
Failure to implement multi-factor authentication leaves even the strongest passwords weak to theft
Insufficient safety coaching makes staff extra weak to phishing emails, social engineering techniques, and different assaults
Poor community segmentation provides hackers open entry as soon as they breach a single endpoint
Inadequate monitoring lets attackers function undetected for days, weeks, and even months inside your important techniques
Worker password reuse amplifies the influence of any breach, as a single stolen credential can unlock a number of techniques throughout private and company environments.
Verizon’s Information Breach Investigation Report discovered stolen credentials are concerned in 44.7% of breaches.
Effortlessly safe Energetic Listing with compliant password insurance policies, blocking 4+ billion compromised passwords, boosting safety, and slashing help hassles!
Strive it without spending a dime
When credentials are compromised: A response state of affairs
In case your group has been the goal of a credential-based assault, you know the way devastating the aftermath may be. However for those who’re one of many fortunate few that has thus far escaped the sights of hackers, this is what it is like:
It is 2:37 AM when your cellphone rings. Your safety group has detected uncommon login patterns from IP addresses in Japanese Europe — throughout your organization’s off-hours. By the point you’ve got logged in remotely, the attacker has accessed a number of delicate buyer information and moved laterally by your community, compromising further techniques.
The sinking feeling hits: your group is experiencing a credential-based assault in real-time. What do you do now?
Instant response steps
When credentials fall into the flawed palms and hackers breach your techniques, each minute counts — however having a well-rehearsed incident response plan will will let you decrease harm and restoration time.
Listed here are the standard steps organizations comply with when responding to an assault:
Preliminary detection and alerting. The clock begins ticking as quickly as your monitoring instruments detect the anomaly and alert your safety group — you have to transfer rapidly to restrict harm.
Evaluation and triage. Confirm that the alert is professional. Then, determine which techniques and accounts are impacted, assessing the potential influence in your group.
Isolation and containment. Reduce off the hackers’ entry factors by disconnecting compromised gadgets from the community. Revoke entry to compromised accounts, and section the community to include the menace.
Detailed investigation. Hint the attacker’s actions by analyzing logs and forensic knowledge. Determine how hackers compromised credentials, and assess what hackers did whereas they’d entry.
Communication and notification. Bear in mind, transparency breeds belief, whereas secrecy breeds suspicion. With this in thoughts, give all related stakeholders clear, factual updates, together with senior administration, authorized groups, and affected customers.
Eradication and restoration. Begin rebuilding your safety techniques, making them stronger. Reset passwords for all compromised accountspatch exploited vulnerabilities, restore techniques from clear backups, and implement multi-factor authentication.
Submit-incident overview. The perfect protection in opposition to a future assault is studying from a present breach. After a breach, analyze your incident response course of, replace your response plan, and implement further safety measures based mostly on classes realized.
Scan your Energetic Listing to stop future assaults
Whereas it’s vital to rapidly reply to credential-based assaults, it’s much more vital (and cost-effective) to stop them altogether. By implementing multi-factor authenticationimplementing sturdy password insurance policies, coaching your employees usually, auditing you Energetic Listing often and correctly segmenting your community, you’ll scale back your group’s vulnerability.
However these measures aren’t sufficient if credentials have been compromised in earlier breaches. That’s why it’s vital to incorporate scanning your Energetic Listing for compromised passwords in your prevention technique.
Specops Password Coverage constantly scans your Energetic Listing in opposition to a database of over 4 billion distinctive compromised passwords. When it identifies staff with breached passwords, the platform instantly prompts them to create new, safe credentials — eliminating a serious vulnerability earlier than attackers can exploit it.
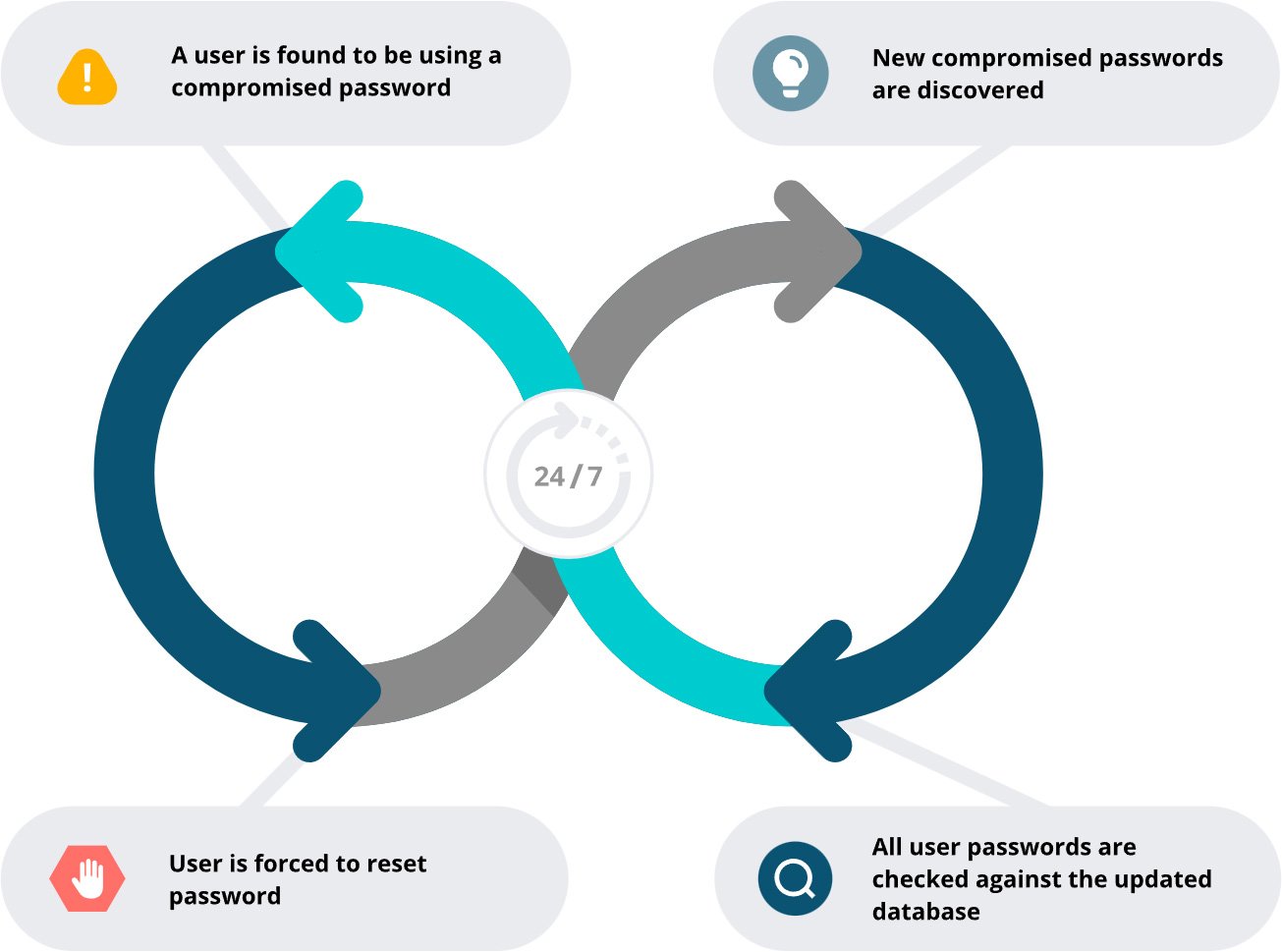
By combining conventional safety measures with lively credential monitoring, your group can defend itself from credential-based assaults. Do not wait till after a breach to safe your techniques — determine and remediate password vulnerabilities earlier than attackers exploit them.
Strive Specops Password Coverage without spending a dime.
Sponsored and written by Specops Software program.




