Amazon SageMaker Lakehouse now helps attribute-based entry management (ABAC) with AWS Lake Formation, utilizing AWS Identification and Entry Administration (IAM) principals and session tags to simplify knowledge entry, grant creation, and upkeep. With ABAC, you possibly can handle enterprise attributes related to consumer identities and allow organizations to create dynamic entry management insurance policies that adapt to the precise context.
SageMaker Lakehouse is a unified, open, and safe knowledge lakehouse that now helps ABAC to supply unified entry to basic function Amazon S3 buckets, Amazon S3 Tables, Amazon Redshift knowledge warehouses, and knowledge sources equivalent to Amazon DynamoDB or PostgreSQL. You may then question, analyze, and be part of the information utilizing Redshift, Amazon Athena, Amazon EMR, and AWS Glue. You may safe and centrally handle your knowledge within the lakehouse by defining fine-grained permissions with Lake Formation which might be persistently utilized throughout all analytics and machine studying(ML) instruments and engines. Along with its help for role-based and tag-based entry management, Lake Formation extends help to attribute-based entry to simplify knowledge entry administration for SageMaker Lakehouse, with the next advantages:
Flexibility – ABAC insurance policies are versatile and could be up to date to satisfy altering enterprise wants. As a substitute of making new inflexible roles, ABAC techniques enable entry guidelines to be modified by merely altering consumer or useful resource attributes.
Effectivity – Managing a smaller variety of roles and insurance policies is extra simple than managing numerous roles, lowering administrative overhead.
Scalability – ABAC techniques are extra scalable for bigger enterprises as a result of they will deal with numerous customers and assets with out requiring numerous roles.
Attribute-based entry management overview
Beforehand, inside SageMaker Lakehouse, Lake Formation granted entry to assets primarily based on the id of a requesting consumer. Our clients had been requesting the aptitude to specific the complete complexity required for entry management guidelines in organizations. ABAC permits for extra versatile and nuanced entry insurance policies that may higher mirror real-world wants. Organizations can now grant permissions on a useful resource primarily based on consumer attribute and is context-driven. This enables directors to grant permissions on a useful resource with situations that specify consumer attribute keys and values. IAM principals with matching IAM or session tag key-value pairs will acquire entry to the useful resource.
As a substitute of making a separate position for every workforce member’s entry to a particular challenge, you possibly can arrange ABAC insurance policies to grant entry primarily based on attributes like membership and consumer position, lowering the variety of roles required. For example, with out ABAC, an organization with an account supervisor position that covers 5 completely different geographical territories must create 5 completely different IAM roles and grant knowledge entry for under the precise territory for which the IAM position is supposed. With ABAC, they will merely add these territory attributes as keys/values to the principal tag and supply knowledge entry grants primarily based on these attributes. If the worth of the attribute for a consumer adjustments, entry to the dataset will robotically be invalidated.
With ABAC, you should utilize attributes equivalent to division or nation and use IAM or periods tags to find out entry to knowledge, making it extra simple to create and preserve knowledge entry grants. Directors can outline fine-grained entry permissions with ABAC to restrict entry to databases, tables, rows, columns, or desk cells.
On this put up, we reveal how one can get began with ABAC in SageMaker Lakehouse and use with varied analytics companies.
Resolution overview
As an example the answer, we’re going to take into account a fictional firm known as Instance Retail Corp. Instance Retail’s management is interested by analyzing gross sales knowledge in Amazon S3 to find out in-demand merchandise, perceive buyer conduct, and establish developments, for higher decision-making and elevated profitability. The gross sales division units up a workforce for gross sales evaluation with the next knowledge entry necessities:
All knowledge analysts within the Gross sales division within the US get entry to solely sales-specific knowledge in solely US areas
All BI analysts within the Gross sales division have full entry to knowledge in solely US areas
All scientists within the Gross sales division get entry to solely sales-specific knowledge throughout all areas
Anybody outdoors of Gross sales division haven’t any entry to gross sales knowledge
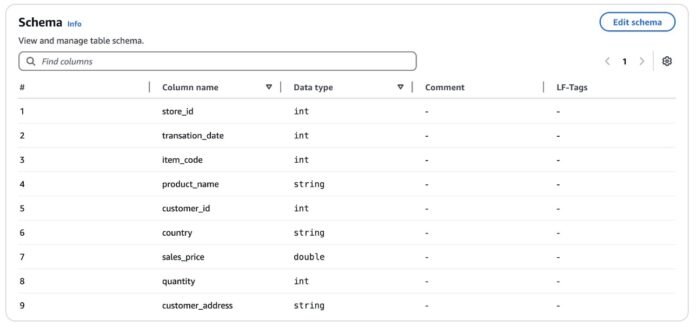
For this put up, we take into account the database salesdb, which accommodates the store_sales desk that has retailer gross sales particulars. The desk store_sales has the next schema.
To reveal the product gross sales evaluation use case, we’ll take into account the next personas from the Instance Retail Corp:
Ava is an information administrator in Instance Retail Corp who’s accountable for supporting workforce members with particular knowledge permission insurance policies
Alice is an information analyst who ought to be capable to entry gross sales particular US retailer knowledge to carry out product gross sales evaluation
Bob is a BI analyst who ought to be capable to entry all knowledge from US retailer gross sales to generate reviews
Charlie is an information scientist who ought to be capable to entry gross sales particular throughout all areas to discover and discover patterns for development evaluation
Ava decides to make use of SageMaker Lakehouse to unify knowledge throughout varied knowledge sources whereas establishing fine-grained entry management utilizing ABAC. Alice is happy about this choice as she will be able to now construct every day reviews utilizing her experience with Athena. Bob now is aware of that he can rapidly construct Amazon QuickSight dashboards with queries which might be optimized utilizing Redshift’s cost-based optimizer. Charlie, being an open supply Apache Spark contributor, is happy that he can construct Spark primarily based processing with Amazon EMR to construct ML forecasting fashions.
Ava defines the consumer attributes as static IAM tags that might additionally embody attributes saved within the id supplier (IdP) or as session tags dynamically to symbolize the consumer metadata. These tags are assigned to IAM customers or roles and can be utilized to outline or prohibit entry to particular assets or knowledge. For extra particulars, seek advice from Tags for AWS Identification and Entry Administration assets and Move session tags in AWS STS.
For this put up, Ava assigns customers with static IAM tags to symbolize the consumer attributes, together with their division membership, Area project, and present position relationship. The next desk summarizes the tags that symbolize consumer attributes and consumer project.
Person
Persona
Attributes
Entry
Alice
Knowledge Analyst
Division=gross sales
Area=US
Function=Analyst
Gross sales particular knowledge in US and no entry to buyer knowledge
Bob
BI Analyst
Division=gross sales
Area=US
Function=BIAnalyst
All knowledge in US
Charlie
Knowledge Scientist
Division=gross sales
Area=ALL
Function=Scientist
Gross sales particular knowledge in All areas and no entry to buyer knowledge
Ava then defines entry management insurance policies in Lake Formation that grant or prohibit entry to sure assets primarily based on predefined standards (consumer attributes outlined utilizing IAM tags) being happy. This enables for versatile and context-aware safety insurance policies the place entry privileges could be adjusted dynamically by modifying the consumer attribute project with out altering the coverage guidelines. The next desk summarizes the insurance policies within the Gross sales division.
Entry
Person Attributes
Coverage
All analysts (together with Alice) in US get entry to gross sales particular knowledge in US areas
Division=gross sales
Area=US
Function=Analyst
Desk: store_sales (store_id, transaction_date, product_name, nation, sales_price, amount columns)
Row filter: nation=’US’
All BI analysts (together with Bob) in US get entry to all knowledge in US areas
Division=gross sales
Area=US
Function=BIAnalyst
Desk: store_sales (all columns)
Row filter: nation=’US’
All scientists (together with Charlie) get entry to sales-specific knowledge from all areas
Division=gross sales
Area=ALL
Function=Scientist
Desk: store_sales (all rows)
Column filter: store_id, transaction_date, product_name, nation, sales_price,amount
The next diagram illustrates the answer structure.

Implementing this resolution consists of the next high-level steps. For Instance Retail, Ava as an information Administrator performs these steps:
Outline the consumer attributes and assign them to the principal.
Grant permission on the assets (database and desk) to the principal primarily based on consumer attributes.
Confirm the permissions by querying the information utilizing varied analytics companies.
Stipulations
To comply with the steps on this put up, you will need to full the next conditions:
AWS account with entry to the next AWS companies:
Amazon S3
AWS Lake Formation and AWS Glue Knowledge Catalog
Amazon Redshift
Amazon Athena
Amazon EMR
AWS Identification and Entry Administration (IAM)
Arrange an admin consumer for Ava. For directions, see Create a consumer with administrative entry.
Setup S3 bucket for importing script.
Arrange an information lake admin. For directions, see Create an information lake administrator.
Create IAM consumer named Alice and connect permissions for Athena entry. For directions, seek advice from Knowledge analyst permissions.
Create IAM consumer Bob and connect permissions for Redshift entry.
Create IAM consumer Charlie and connect permissions for EMR Serverless entry.
Create job runtime position: scientist_role and that will likely be utilized by Charlie. For instruction seek advice from: Job runtime roles for Amazon EMR Serverless
Setup EMR Serverless utility with Lake Formation enabled. For instruction seek advice from: Utilizing EMR Serverless with AWS Lake Formation for fine-grained entry management
Have an present AWS Glue database or desk and Amazon Easy Storage Service (Amazon) S3 bucket that holds the desk knowledge. For this put up, we use salesdb as our database, store_sales as our desk, and knowledge is saved in an S3 bucket.
Outline attributes for the IAM principals Alice, Bob, Charlie
Ava completes the next steps to outline the attributes for the IAM principal:
Log in as an admin consumer and navigate to the IAM console.
Select Customers beneath Entry administration within the navigation pane and seek for the consumer Alice.
Select the consumer and select the Tags tab.
Select Add new tag and supply the next key pairs:
Key: Division and worth: gross sales
Key: Area and worth: US
Key: Function and worth: Analyst
Select Save adjustments.
Repeat the method for the consumer Bob and supply the next key pairs:
Key: Division and worth: gross sales
Key: Area and worth: US
Key: Function and worth: BIAnalyst
Repeat the method for the consumer Charlie and IAM position scientist_role and supply the next key pairs:
Key: Division and worth: gross sales
Key: Area and worth: ALL
Key: Function and worth: Scientist
Grant permissions to Alice, Bob, Charlie utilizing ABAC
Ava now grants database and desk permissions to customers with ABAC.
Grant database permissions
Full the next steps:
Ava logs in as knowledge lake admin and navigate to the Lake Formation console.
Within the navigation pane, beneath Permissions, select Knowledge lake permissions.
Select Grant.
On the Grant permissions web page, select Principals by attribute.
Specify the next attributes:
Key: Division and worth: gross sales
Key: Function and worth: Analyst,Scientist
Evaluate the ensuing coverage expression.
For Permission scope, choose This account.
Subsequent, select the catalog assets to grant entry:
For Catalogs, enter the account ID.
For Databases, enter salesdb.
For Database permissions, choose Describe.
Select Grant.
Ava now verifies the database permission by navigating to the Databases tab beneath the Knowledge Catalog and trying to find salesdb. Choose salesdb and select View beneath Actions.

Grant desk permissions to Alice
Full the next steps to create an information filter to view gross sales particular columns in store_sales information whose nation=US:
On the Lake Formation console, select Knowledge filters beneath Knowledge Catalog within the navigation pane.
Select Create new filter.
Present the information filter title as us_sales_salesonlydata.
For Goal catalog, enter the account ID.
For Goal database, select salesdb.
For Goal desk, select store_sales.
For column-level entry, select Embody columns: store_id, item_code, transaction_date, product_name, nation, sales_price, and amount.
For Row-level entry, select Filter rows and enter the row filter nation=’US’.
Select Create knowledge filter.
On the Grant permissions web page, select Principals by attribute.
Specify the attributes:
Key: Division and worth: gross sales
Key: Function as worth: Analyst
Key: Area and worth: US
Evaluate the ensuing coverage expression.
For Permission scope, choose This account.
Select the catalog assets to grant entry:
Catalogs: Account ID
Databases: salesdb
Desk: store_sales
Knowledge filters: us_sales
For Knowledge filter permissions, choose Choose.
Select Grant.
Grant desk permissions to Bob
Full the next steps to create an information filter to view solely store_sales information whose nation=US:
On the Lake Formation console, select Knowledge filters beneath Knowledge Catalog within the navigation pane.
Select Create new filter.
Present the information filter title as us_sales.
For Goal catalog, enter the account ID.
For Goal database, select salesdb.
For Goal desk, select store_sales.
Depart Column-level entry as Entry to all columns.
For Row-level entry, enter the row filter nation=’US’.
Select Create knowledge filter.
Full the next steps to grant desk permissions to Bob:
On the Grant permissions web page, select Principals by attribute.
Specify the attributes:
Key: Division and worth: gross sales
Key: Function as worth: BIAnalyst
Key: Area and worth: US
Evaluate the ensuing coverage expression.
For Permission scope, choose This account.
Select the catalog assets to grant entry:
Catalogs: Account ID
Databases: salesdb
Desk: store_sales
For Knowledge filter permissions, choose Choose.
Select Grant.
Grant desk permissions to Charlie
Full the next steps to grant desk permissions to Charlie:
On the Grant permissions web page, select Principals by attribute.
Specify the attributes:
Key: Division and worth: gross sales
Key: Function as worth: Scientist
Key: Area and worth: ALL
Evaluate the ensuing coverage expression.
For Permission scope, choose This account
Select the catalog assets to grant entry:
Catalogs: Account ID
Databases: salesdb
Desk: store_sales
For Desk permissions, choose Choose.
For Knowledge permissions, specify the next columns: store_id, transaction_date, product_name, nation, sales_price, and amount.
Select Grant.
Alice now verifies the desk permission by navigating to the Tables tab beneath the Knowledge Catalog and trying to find store_sales. Choose store_sales and select View beneath Actions. The next screenshots present the main points for each units of permissions.



Knowledge Analyst makes use of Athena for constructing every day gross sales reviews
Alice, the information analyst logs in to the Athena console and run the next question:
choose * from “salesdb”.”store_sales” restrict 5
Alice has the consumer attributes as Division=gross sales, Function=Analyst, Area=US, and this attribute mixture permits her entry to US gross sales knowledge to particular gross sales solely column, with out entry to buyer knowledge as proven within the following screenshot.

BI Analyst makes use of Redshift for constructing gross sales dashboards
Bob, the BI Analyst, logs in to the Redshift console and run the next question:
choose * from “salesdb”.”store_sales” restrict 10
Bob has the consumer attributes Division=gross sales, Function=BIAnalyst, Area=US, and this attribute mixture permits him entry to all columns together with buyer knowledge for US gross sales knowledge.

Knowledge Scientist makes use of Amazon EMR to course of gross sales knowledge
Lastly, Charlie logs in to the EMR console and submit the EMR job with runtime position as scientist_role. Charlie makes use of the script sales_analysis.py that’s uploaded to s3 bucket created for the script. He chooses the EMR Serverless utility created with Lake Formation enabled.
Charlie submits batch job runs by selecting the next values:
Title: sales_analysis_Charlie
Runtime_role: scientist_role
Script location: /sales_analysis.py
For spark properties, present key as spark.emr-serverless.lakeformation.enabled and worth as true.
Further configurations: Below Metastore configuration choose Use AWS Glue Knowledge Catalog as metastore. Charlie retains remainder of the configuration as default.
As soon as the job run is accomplished, Charlie can view the output by choosing stdout beneath Driver log information.

Charlie makes use of scientist_role as job runtime position with the attributes Division=gross sales, Function=Scientist, Area=ALL, and this attribute mixture permits him entry to pick columns of all gross sales knowledge.

Clear up
Full the next steps to delete the assets you created to keep away from surprising prices:
Delete the IAM customers created.
Delete the AWS Glue database and desk assets created for the put up, if any.
Delete the Athena, Redshift and EMR assets created for the put up.
Conclusion
On this put up, we showcased how you should utilize SageMaker Lakehouse attribute-based entry management, utilizing IAM principals and session tags to simplify knowledge entry, grant creation, and upkeep. With attribute-based entry management, you possibly can handle permissions utilizing dynamic enterprise attributes related to consumer identities and safe your knowledge within the lakehouse by defining fine-grained permissions within the Lake Formation which might be enforced throughout analytics and ML instruments and engines.
For extra data, seek advice from documentation. We encourage you to check out the SageMaker Lakehouse with ABAC and share your suggestions with us.
In regards to the authors
 Sandeep Adwankar is a Senior Product Supervisor at AWS. Primarily based within the California Bay Space, he works with clients across the globe to translate enterprise and technical necessities into merchandise that allow clients to enhance how they handle, safe, and entry knowledge.
Sandeep Adwankar is a Senior Product Supervisor at AWS. Primarily based within the California Bay Space, he works with clients across the globe to translate enterprise and technical necessities into merchandise that allow clients to enhance how they handle, safe, and entry knowledge.
 Srividya Parthasarathy is a Senior Massive Knowledge Architect on the AWS Lake Formation workforce. She enjoys constructing knowledge mesh options and sharing them with the neighborhood.
Srividya Parthasarathy is a Senior Massive Knowledge Architect on the AWS Lake Formation workforce. She enjoys constructing knowledge mesh options and sharing them with the neighborhood.