The Russian state-sponsored menace group APT28 is utilizing Sign chats to focus on authorities targets in Ukraine with two beforehand undocumented malware households named BeardShell and SlimAgent.
To be clear, this isn’t a safety situation in Sign. As a substitute, menace actors are extra generally using the messaging platform as a part of their phishing assaults resulting from its elevated utilization by governments worldwide.
The assaults have been first found by Ukraine’s Laptop and Emergency Response (Cert-doing) in March 2024, although restricted particulars in regards to the an infection vector have been uncovered on the time.
Over a yr later, in Could 2025, ESET notified CERT-UA of unauthorized entry to a gov.ua e mail account, prompting a brand new incident response.
Throughout this new investigation, CERT-UA found that messages despatched through the encrypted messenger app Sign have been used to ship a malicious doc to targets (Акт.doc), which makes use of macros to load a memory-resident backdoor referred to as Covenant.
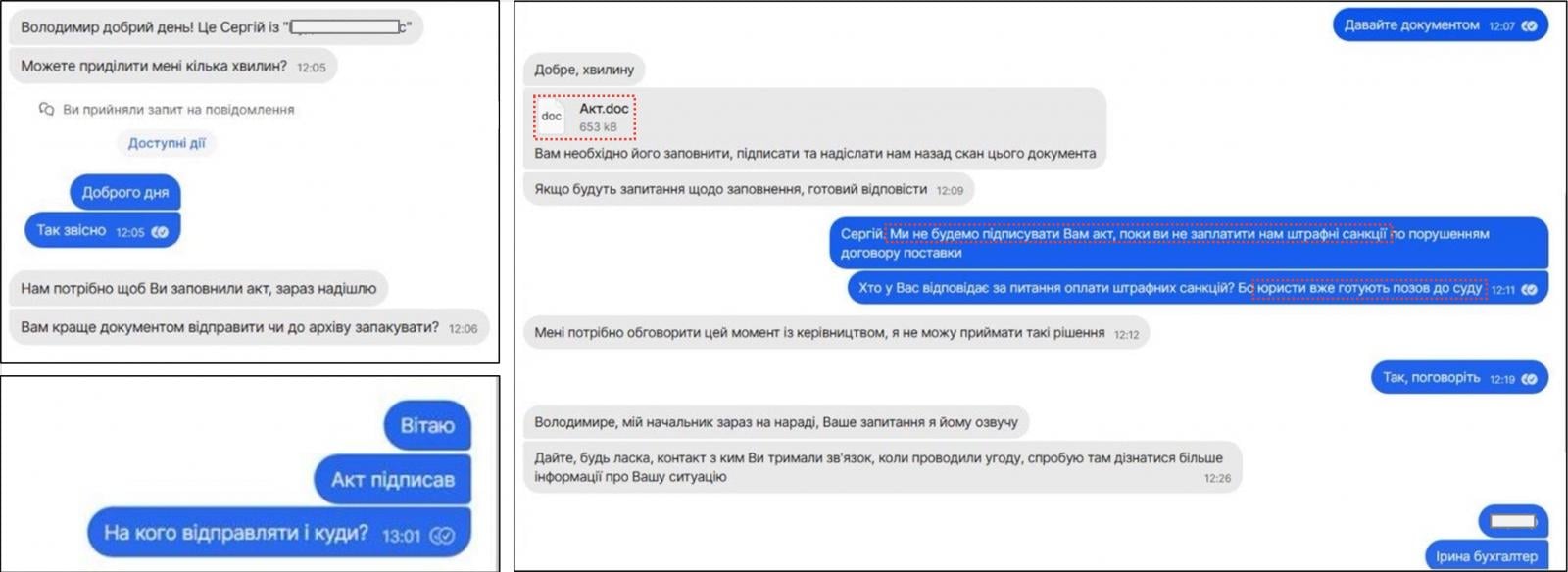 APT28 assault through Sign
APT28 assault through Sign
Supply: CERT-UA
Covenant acts as a malware loader, downloading a DLL (PlaySndSrv.dll) and a shellcode-ridden WAV file (sample-03.wav) that hundreds BeardShell, a beforehand undocumented C++ malware.
For each the loader and the first malware payload, persistence is secured through COM-hijacking within the Home windows registry.
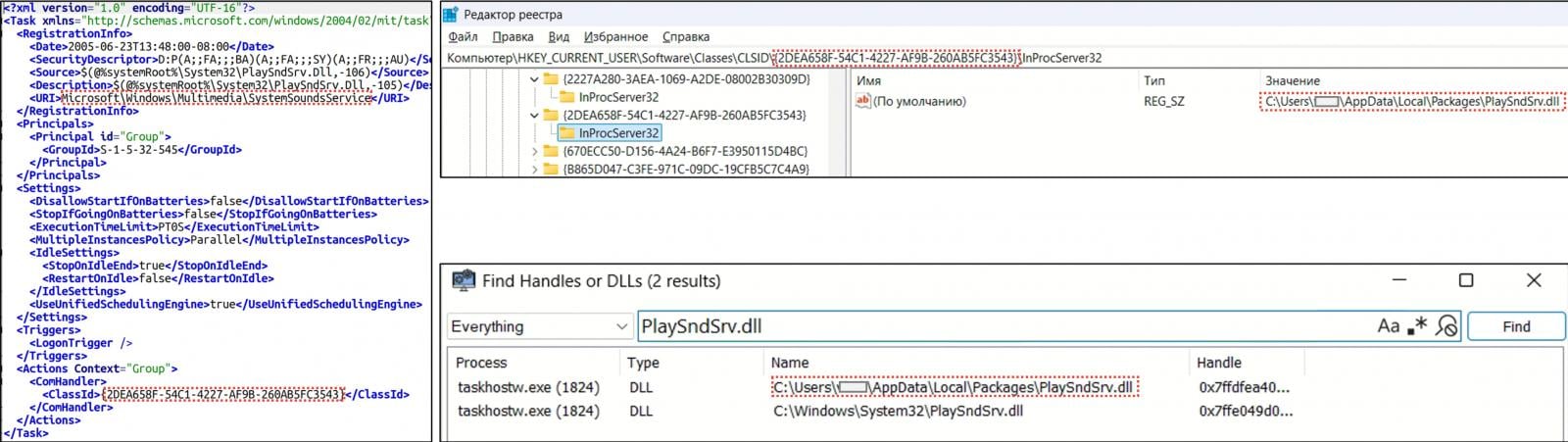 Establishing persistence for BeardShell
Establishing persistence for BeardShell
Supply: CERT-UA
BeardShell’s important performance is to obtain PowerShell scripts, decrypt them utilizing ‘chacha20-poly1305’, and execute them. The execution outcomes are exfiltrated to the command-and-control (C2) server, the communication with which is facilitated by Icedrive API.
Within the 2024 assaults, CERT-UA additionally noticed a screenshot grabber named SlimAgent, which captures screenshots utilizing an array of Home windows API capabilities (EnumDisplayMonitors, CreateCompatibleDC, CreateCompatibleBitmap, BitBlt, GdipSaveImageToStream).
These pictures are encrypted utilizing AES and RSA, and saved domestically, presumably to be exfiltrated by a separate payload/device to APT28’s C2 server.
CERT-UA attributes this exercise to APT28, which they observe as UAC-0001, and recommends that potential targets monitor community interactions with app.koofr.web and api.icedrive.web.
APT28 has a protracted historical past of focusing on Ukraine in addition to different key organizations within the U.S. and Europe, primarily for cyberespionage.
They’re one among Russia’s most superior menace teams, uncovered by Volexity in November 2024 for utilizing a novel “nearest neighbor” approach, which remotely breached targets by exploiting close by Wi-Fi networks.
In 2025, Sign unexpectedly grew to become central to cyberattacks linked to Russia and Ukraine.
The favored communications platform has been abused in spear-phishing assaults that abused the platform’s device-linking characteristic to hijack accounts and in Darkish Crystal RAT distribution in opposition to key targets in Ukraine.
Sooner or later, representatives of Ukraine’s authorities expressed disappointment that Sign allegedly stopped collaborating with them of their effort to dam Russian assaults. Ukrainian officers later voiced frustration over Sign’s lack of cooperation in blocking Russian operations.
Nonetheless, Sign president Meredith Whittaker met that declare with shocksaying the platform has by no means shared communication knowledge with Ukraine or some other authorities.
Patching used to imply complicated scripts, lengthy hours, and infinite fireplace drills. Not anymore.
On this new information, Tines breaks down how trendy IT orgs are leveling up with automation. Patch quicker, scale back overhead, and give attention to strategic work — no complicated scripts required.





