A coordinated marketing campaign of brute-force assaults utilizing a whole bunch of distinctive IP addresses targets Apache Tomcat Supervisor interfaces uncovered on-line.
Tomcat is a well-liked open-source internet server broadly utilized by giant enterprises and SaaS suppliers, whereas Tomcat Supervisor is a web-based administration device that comes bundled with the Tomcat server and helps admins handle deployed internet apps by way of a graphical interface.
Tomcat Supervisor is configured by default to solely permit entry from localhost (127.0.0.1), with no pre-configured credentials and distant entry blocked. Nevertheless, when uncovered on-line, the net app may be focused by attackers, as cybersecurity firm GreyNoise noticed just lately.
Beginning June fifth, GreyNoise analysts found two coordinated campaigns concentrating on Apache Tomcat Supervisor interfaces and attempting to achieve entry to Tomcat companies over the Web.
The primary used practically 300 distinctive IP addressesmost tagged as malicious, which had been making an attempt to log into uncovered on-line, and the second employed 250 malicious IPs to focus on Tomcat Supervisor internet apps in brute pressure assaults, the place risk actors use automated instruments to check hundreds and even hundreds of thousands of doable credentials.
“Roughly 400 distinctive IPs had been concerned within the exercise noticed throughout each tags throughout this era of elevated exercise. Many of the exercise originating from these IPs exhibited a slim give attention to Tomcat companies. A good portion of this exercise originated from infrastructure hosted by DigitalOcean (ASN 14061),” GreyNoise mentioned.
“Whereas not tied to a selected vulnerability, this conduct highlights ongoing curiosity in uncovered Tomcat companies. Broad, opportunistic exercise like this usually serves as an early warning of future exploitation.”
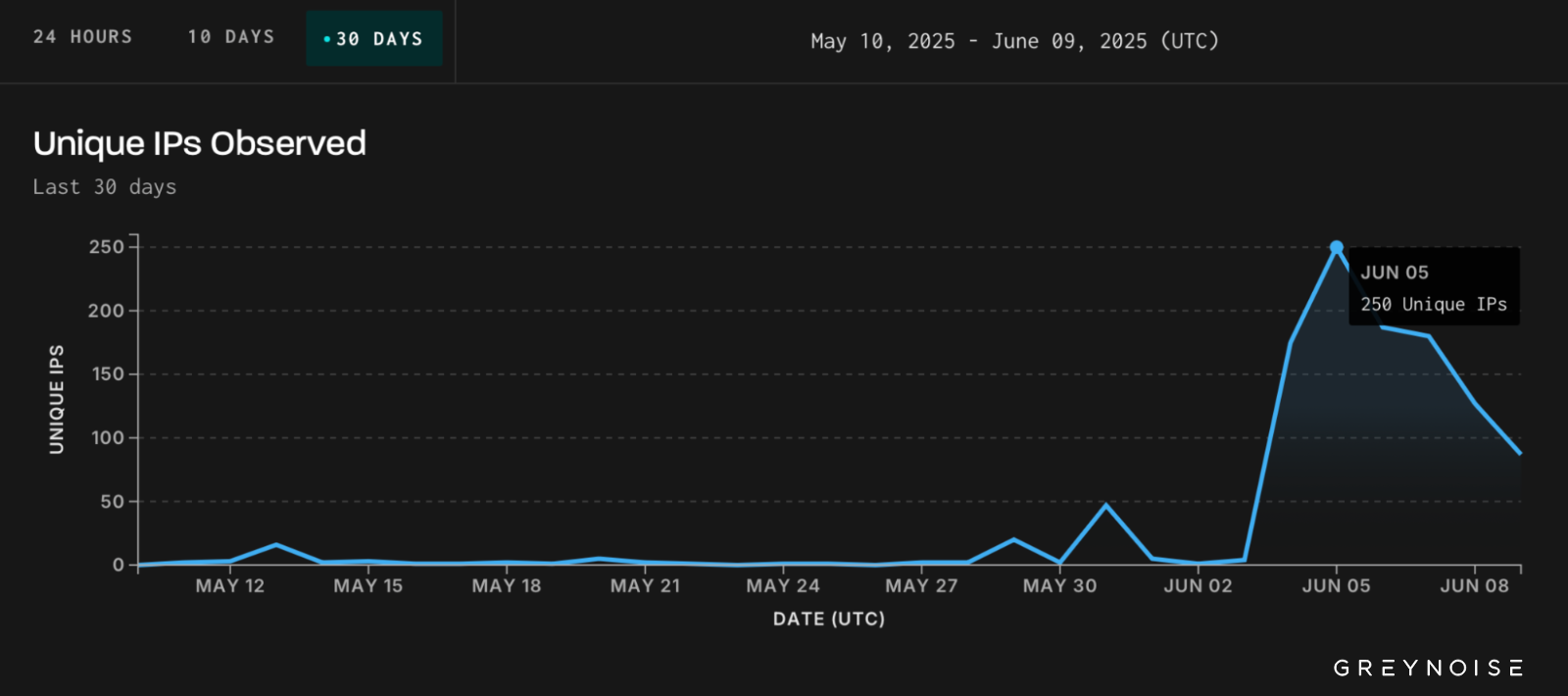 Tomcat brute pressure assaults (GreyNoise)
Tomcat brute pressure assaults (GreyNoise)
The cybersecurity firm suggested organizations with Tomcat Supervisor interfaces uncovered on-line to guarantee they’ve robust authentication and entry restrictions.
Customers ought to test safety logs for any suspicious login exercise and promptly block any IP addresses that could possibly be behind a breach try.
Whereas no particular safety vulnerability was exploited in these assaults, Apache launched safety fixes in March to patch a distant code execution (RCE) vulnerability in Apache Tomcat (CVE-2025-24813) actively exploited within the wild to take over susceptible servers with a easy PUT request.
The risk actors behind the assaults reportedly used proof-of-concept (PoC) exploits launched on GitHub simply 30 hours after the flaw was disclosed and patched.
In December, Apache additionally fastened one other Tomcat RCE flaw (CVE-2024-56337) that could possibly be used to bypass the patch for a second vital RCE vulnerability (CVE-2024-50379) mitigated days earlier.
Patching used to imply complicated scripts, lengthy hours, and countless fireplace drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch quicker, scale back overhead, and give attention to strategic work — no complicated scripts required.





