Organizations more and more face advanced necessities balancing regional information sovereignty with international analytics wants. Regulatory frameworks like GDPR, HIPAA, and native information safety legal guidelines usually mandate storing information in particular geographic areas, and enterprise operations require international groups to entry and analyze this information effectively.
This publish explores tips on how to successfully architect an answer that addresses this particular problem: enabling complete analytics capabilities for international groups whereas ensuring that your information stays within the AWS Areas required by your compliance framework. We use a wide range of AWS companies, together with Amazon Redshift, Amazon Easy Storage Service (Amazon S3), and Amazon QuickSight.
It’s essential to notice that this answer focuses totally on information residency (the place information is saved) and never on stopping information from being in transit between Areas. Organizations with strict information transit restrictions would possibly want further controls past what’s lined right here. We present how one can configure AWS throughout Areas to assist meet enterprise wants and regulatory necessities concurrently.
Cross-Area structure necessities
Earlier than implementing a cross-Area answer, it’s essential to grasp when this method is definitely obligatory. Though single-Area deployments supply simplicity and value benefits, a number of particular enterprise and regulatory situations warrant a cross-Area method:
Knowledge sovereignty and residency necessities – When laws like GDPR, HIPAA, or native information sovereignty legal guidelines require information to stay in particular geographic boundaries whereas nonetheless enabling international analytics capabilities
World operations with native compliance – When your group operates globally, however wants to stick to regional compliance frameworks whereas sustaining unified analytics
Efficiency optimization for international customers – When your group must optimize analytics efficiency for customers in several geographic areas whereas centralizing information governance
Enhanced enterprise continuity – When your analytics capabilities want increased availability and Regional redundancy to help mission-critical enterprise processes
Use case: Monetary companies analytics with Regional information residency
Think about a monetary companies firm with the next enterprise and regulatory necessities:
Knowledge residency requirement – All buyer monetary information should stay within the Bahrain Area (me-south-1) to adjust to native monetary laws.
World analytics functionality – The group’s information science workforce operates from European workplaces and must entry and analyze the monetary information with out transferring it out of its mandated storage Area.
Superior analytics necessities – Enterprise leaders want interactive information exploration and pure language question capabilities to derive insights from monetary information.
Efficiency requirement – Particular dashboard queries require subsecond response occasions for each native executives and the worldwide administration workforce.
This particular mixture of necessities can’t be met with a single-Area deployment. Let’s discover tips on how to architect an answer.
Answer overview
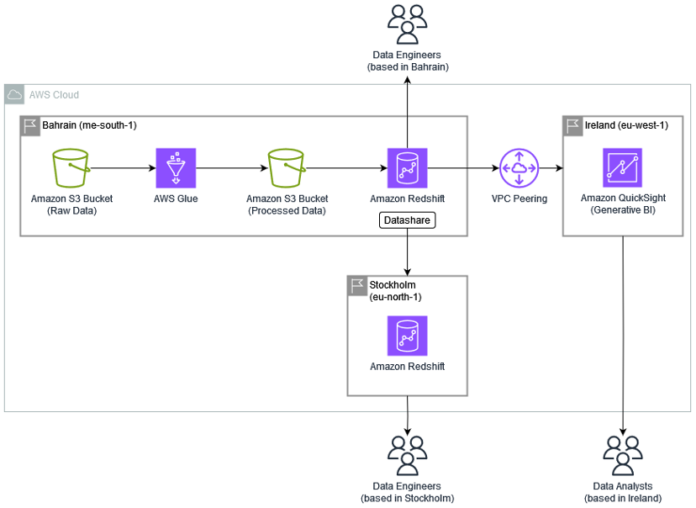
The next structure is designed to deal with the particular problem of utilizing QuickSight in a single Area whereas sustaining information in one other Area.
As proven within the structure diagram, information engineers primarily based in Bahrain (me-south-1) work with native information, whereas information engineers in Stockholm (eu-north-1) and analysts in Eire (eu-west-1) can securely entry the identical information by way of Redshift datashares and digital non-public cloud (VPC) peering connections. This method maintains information residency in me-south-1 whereas enabling international entry.
The answer consists of the next key elements:
Major information Area (me-south-1):
Redshift cluster (major information repository)
S3 buckets for information lake storage
Personal and public subnets with applicable safety controls
Knowledge should stay on this Area for compliance causes
Analytics companies Area (eu-west-1):
QuickSight deployment
Cross-Area VPC peering connection to the first Area
Knowledge entry utilizing Redshift datashares (no information replication)
Knowledge engineering Area (eu-north-1):
Redshift client cluster for information engineering workloads
Knowledge entry utilizing Redshift datashares from me-south-1
Makes it potential for information engineering groups in eu-north-1 to entry and work with information whereas sustaining compliance
Earlier than implementing this structure, consider whether or not:
Your necessities really necessitate a cross-Area method
The efficiency impression is appropriate to your use case
The extra price is justified by your enterprise necessities
For many analytics workloads, a single-Area structure stays the really useful method for simplicity, efficiency, and cost-effectiveness. Think about cross-Area architectures solely when particular enterprise and compliance necessities make them obligatory.
Set up cross-Area community connectivity: Amazon Redshift to QuickSight
The muse of a cross-Area answer is safe, dependable community connectivity. VPC peering gives an easy method for connecting VPCs throughout Areas. To implement VPC peering in Amazon Digital Personal Cloud (Amazon VPC), full the next steps:
Create a brand new VPC within the secondary Area (eu-west-1):
Open the Amazon VPC console within the eu-west-1 Area.
Select Create VPC.
Set IPv4 CIDR block to 172.32.0.0/16 (confirm there isn’t a overlap with the first Area VPC).
Choose Auto-generate to create subnets routinely inside this new VPC.
Go away different settings as default and select Create VPC.

Arrange VPC peering:
On the Amazon VPC console, select Peering connections within the navigation pane and select Create peering connection.
Choose the brand new eu-west-1 VPC because the requester.
For Choose one other VPC to see with, choose My account and One other Area.
Select the first Area (me-south-1) and enter the VPC ID.
Select Create peering connection.

Settle for the VPC peering connection:
Change to the first Area on the Amazon VPC console.
Select Peering connections within the navigation pane and choose the pending connection.
On the Actions dropdown menu, select Settle for request.

Replace the route tables:
On the secondary Area Amazon VPC console, select Route tables within the navigation pane.
Select the route desk for the brand new VPC.
Select Edit routes and add a brand new route:
Vacation spot: Major Area VPC CIDR (e.g., 172.31.0.0/16).
Goal: Select the peering connection.
On the first Area Amazon VPC console, repeat the method, including a path to the secondary Area VPC CIDR (172.32.0.0/16) utilizing the peering connection.

Configure safety teams:
On the secondary Area Amazon VPC console, select Safety teams within the navigation pane and create a brand new safety group.
Add an outbound rule:
Sort: Customized TCP
Port vary: 5439
Vacation spot: Major Area VPC CIDR

On the first Area Amazon VPC console, find the Redshift cluster’s safety group.
Add an inbound rule:
Sort: Customized TCP
Port vary: 5439
Supply: Secondary Area VPC CIDR

Configure DNS settings:
On the Amazon VPC console for each Areas, select Your VPCs within the navigation pane.
Choose every VPC, and on the Actions dropdown menu, select Edit DNS hostnames.
Choose Allow DNS decision and Allow DNS hostnames.

Implement cross-Area information sharing
Quite than replicating information, which may create compliance points, you need to use Redshift datashares to offer safe, read-only entry to information throughout Areas. Full the next steps to arrange your datashares:
Create producer datashares within the major Area:
On the Amazon Redshift console, select Question editor v2 within the navigation pane to hook up with your major Area Redshift cluster (me-south-1).
Run the next instructions: — In Major Area Redshift
CREATE DATASHARE datashare_1;
ALTER DATASHARE datashare_1 ADD SCHEMA analytics;
ALTER DATASHARE datashare_1 ADD TABLE analytics.prospects;
ALTER DATASHARE datashare_1 ADD TABLE analytics.transactions;
— Grant utilization permissions
GRANT USAGE ON DATASHARE datashare_1 TO ACCOUNT ‘123456789012’;

Create a client database within the secondary Area:
Connect with your secondary Area Redshift cluster (eu-west-1) utilizing the question editor and run the next instructions: — In Secondary Area Redshift
CREATE DATABASE consumer_db FROM DATASHARE datashare_1 OF ACCOUNT ‘123456789012’REGION ‘me-south-1’;
Confirm the datashare configuration with the next code: — In Secondary Area Redshift
SELECT * FROM SVV_DATASHARE_CONSUMERS;
SELECT * FROM SVV_DATASHARE_OBJECTS;
This method maintains information residency within the major Area whereas enabling analytics entry from one other Area, addressing the core problem of Regional service limitations. For our monetary companies firm instance, this makes positive that buyer monetary information stays in Bahrain (me-south-1) whereas making it securely accessible to the information science workforce in Europe (eu-west-1).
Configure QuickSight within the analytics Area
With community connectivity and information sharing established, full the next steps to configure QuickSight to securely entry the Redshift information:
Arrange a QuickSight VPC connection:
Open the QuickSight console within the secondary Area.
Select Handle QuickSight, VPC connections, and Add VPC connection.
Configure the connection:
Identify: Enter a reputation (for instance, Cross-Area-Connection).
VPC: Select the secondary Area VPC.
Subnet: Select the routinely created subnets.
Safety group: Select the safety group created for cross-Area entry.

Add a QuickSight IP vary to the information supply safety group:
Open the Amazon Elastic Compute Cloud (Amazon EC2) console within the major Area.
Select Safety teams within the navigation pane and discover the safety group to your information supply.
Edit the inbound guidelines.
Add a brand new rule:
Sort: HTTPS (443)
Protocol: TCP
Port vary: 443
Supply: QuickSight IP vary for the secondary Area (for instance, 52.210.255.224/27 for eu-west-1).
QuickSight IP ranges can change over time. Seek advice from AWS Areas, web sites, IP deal with ranges, and endpoints for present IP ranges.
Create a QuickSight information supply:
On the QuickSight console, select Datasets within the navigation pane.
Select New dataset, then select Redshift.
Configure the connection:
Knowledge supply identify: Enter a descriptive identify.
Connection sort: Select the VPC connection.
Database server: Enter the Redshift cluster endpoint from the first Area.
Port: 5439
Database identify: Enter the buyer database identify.
Username and Password: Enter credentials (think about using AWS Secrets and techniques Supervisor).
Select Validate connection to check.
Select Create information supply.

Confirm the connection and create datasets:
Select the schema and tables from the buyer database.
Configure applicable refresh schedules.
Create calculations and visualizations as wanted.
Efficiency concerns for cross-Area analytics
When implementing a cross-Area analytics structure, pay attention to the next efficiency implications:
Question efficiency impression – Cross-Area queries can expertise increased latency than single-Area queries. To mitigate this, think about the next:
Use SPICE for QuickSight – Import frequently-used datasets into SPICE (Tremendous-fast, Parallel, In-memory Calculation Engine) to assist keep away from repeated cross-Area queries. SPICE is the QuickSight in-memory engine that allows quick, interactive visualizations by precomputing and storing datasets regionally within the QuickSight Area.
Implement environment friendly question patterns – Decrease the quantity of information transferred between Areas.
Use applicable caching – Allow outcome caching the place potential.
Monitoring cross-Area efficiency – Implement monitoring to establish and deal with efficiency points:
Arrange Amazon CloudWatch metrics to trace cross-Area question efficiency
Create dashboards to visualise latency developments
Set up efficiency baselines and alerts for degradation
Safety concerns
Sustaining safety in a cross-Area structure requires further consideration:
Community safety:
Restrict VPC peering connections to solely obligatory VPCs
Implement restrictive safety teams that permit solely required visitors
Think about using VPC endpoints for service entry when potential
Knowledge entry controls:
Use AWS Identification and Entry Administration (IAM) insurance policies persistently throughout Areas
Implement fine-grained entry controls in Redshift datashares
Allow audit logging in related Areas
Compliance monitoring:
Implement AWS CloudTrail in all Areas
Create centralized logging for cross-Area actions
Commonly overview cross-Area entry patterns
Price implications
Earlier than implementing a cross-Area structure, think about these price components:
Knowledge switch prices – Knowledge switch between Areas incurs costs
Further infrastructure – You would possibly want Redshift clusters in a number of Areas
VPC peering prices – Knowledge switch prices are related to VPC peering
Operational overhead – Managing multi-Area deployments requires further assets
Workload-based sizing – You need to measurement every Regional Redshift cluster in response to the particular workloads it would deal with
Conclusion
The cross-Area structure described on this publish addresses particular challenges associated to Regional compliance necessities and international analytics wants, significantly within the following situations:
Your information should stay in a selected Area for compliance causes
You’ve groups in several Areas who have to entry and analyze this information
Completely different consumer teams have distinct workload necessities
The datasharing capabilities of Amazon Redshift and Regional storage choices in Amazon S3 are key enablers of this answer, permitting information to stay within the required Area whereas nonetheless being accessible for analytics throughout Areas. Nonetheless, it’s value emphasizing that this structure helps information storage in particular Areas however doesn’t forestall information from touring between Areas throughout processing. Organizations involved about information transit restrictions ought to consider further controls to deal with these particular necessities. Mixed with safe VPC peering connections and QuickSight visualizations, this structure creates an entire answer that satisfies each compliance necessities and enterprise wants.
For our monetary companies instance, this structure efficiently allows the corporate to maintain its buyer monetary information in Bahrain whereas offering seamless analytics capabilities to the European information science workforce and delivering interactive dashboards to international enterprise leaders.
For extra data, consult with Constructing a Cloud Safety Posture Dashboard with Amazon QuickSight. For hands-on expertise, discover the Amazon QuickSight Workshops. Go to the Amazon Redshift console or Amazon QuickSight console to start out constructing your first dashboard, and discover our AWS Massive Knowledge Weblog for extra buyer success tales and implementation patterns
Check out this answer to your personal use case, and share your ideas within the feedback.
In regards to the Authors
 Donatas Kuchalskis is a Cloud Operations Architect at AWS, primarily based in London, specializing in Monetary Companies prospects within the UK. He helps prospects optimize their AWS environments for price, safety, and resiliency whereas offering strategic cloud steering. Previous to this function, he served as a Prototyping Architect specializing in Massive Knowledge and as a Specialist Options Architect for Retail. Earlier than becoming a member of AWS, Donatas spent 6 years as a technical guide within the retail sector.
Donatas Kuchalskis is a Cloud Operations Architect at AWS, primarily based in London, specializing in Monetary Companies prospects within the UK. He helps prospects optimize their AWS environments for price, safety, and resiliency whereas offering strategic cloud steering. Previous to this function, he served as a Prototyping Architect specializing in Massive Knowledge and as a Specialist Options Architect for Retail. Earlier than becoming a member of AWS, Donatas spent 6 years as a technical guide within the retail sector.
 Jumana Nagaria is a Prototyping Architect at AWS. She builds modern prototypes with prospects to resolve their enterprise challenges. She is enthusiastic about cloud computing and information analytics. Exterior of labor, Jumana enjoys travelling, studying, portray, and spending high quality time with family and friends.
Jumana Nagaria is a Prototyping Architect at AWS. She builds modern prototypes with prospects to resolve their enterprise challenges. She is enthusiastic about cloud computing and information analytics. Exterior of labor, Jumana enjoys travelling, studying, portray, and spending high quality time with family and friends.