The sheer quantity of cyberattacks continues to extend at a panoramic scale worldwide, with clients going through greater than 600 million cybercriminal and nation-state assaults daily.1 To stem the rising tide of malicious cyber exercise takes a dedication from all of us—people from operations to the manager degree, safety groups, organizations, trade leaders, and governments. It additionally requires a shift from conventional safety approaches to a defense-in-depth technique that deploys safety instruments that natively work collectively to coordinate protection throughout safety layers.
Organizations additionally have to embrace AI and automation, shifting away from handbook, reactive safety to an automatic, proactive protection. However the transition is less complicated stated than performed. For many organizations, this transition would require vital effort that spans not simply know-how, however individuals and processes too. To assist organizations make the transfer past silos to an built-in, defense-in-depth method, we’re sharing a brand new e-book—our introduction to constructing a coordinated protection. On this submit, we stroll by way of the important thing content material yow will discover within the e-book and share extra sources on built-in cyberthreat safety.
Suggestions constructed on real-world classes
Unhealthy actors are more and more adept at discovering and exploiting weaknesses, particularly in legacy infrastructure. The Coordinated Protection e-book was crafted by way of our personal classes discovered in real-world situations, in addition to our work to assist clients defend their very own organizations. The e-book can assist safety groups higher perceive how a unified answer can enhance their capacity to defend their more and more complicated and various digital environments and:
Cease combating fires and turn into extra proactive by way of streamlined menace looking, triage, and investigation.
Undertake a steady menace publicity administration method that addresses probably the most vital safety domains, together with endpoints, identities, and cloud-native purposes.
Speed up safety operations (SecOps) to decrease imply time to decision (MTTR).
Unified safety operations
Within the e-book, we develop on a brand new pre-breach/post-breach paradigm that helps organizations shift from reactive and handbook processes to an AI-powered, steady, and autonomous safety posture as they stop, detect, and reply to cyberthreats—unified safety operations.
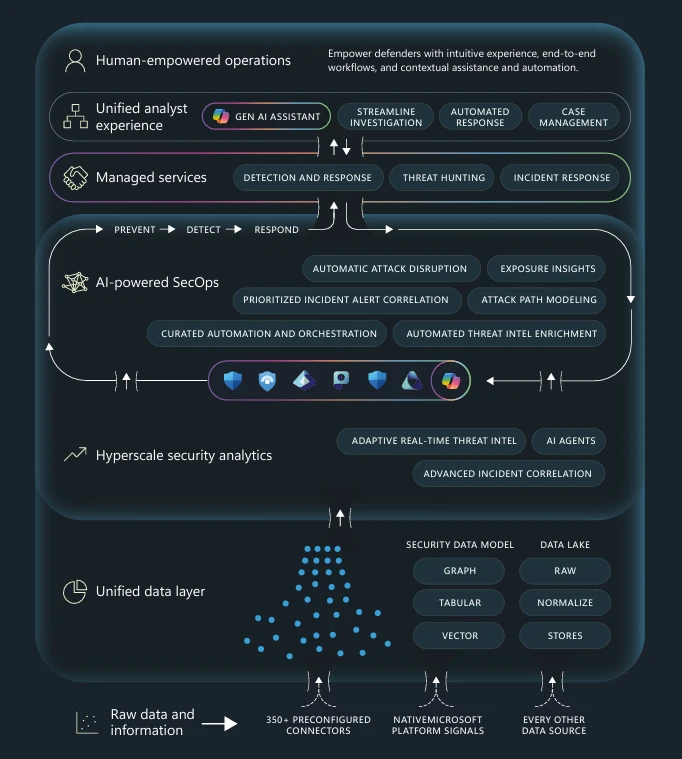
By integrating endpoints, identities, e-mail, apps, information, and cloud environments with the vital safety operations features, together with posture administration, detection and response, and menace intelligence, safety groups can shift from reactive to proactive safety. The e-book outlines the unified structure that may remodel safety operations by centralizing information and leveraging AI to reinforce current human experience.
Determine 1. Diagram of unified safety operations heart (SOC) structure that integrates information, AI, and human experience to empower safety groups to forestall, detect, and reply to threats seamlessly throughout your entire lifecycle.
Addressing the whole menace lifecycle
From stopping preliminary compromise, to detecting and disrupting lively cyberattacks, to investigating and responding to incidents, the e-book explains how unifying safety operations permits groups to construct a closed-loop method that improves enterprise resiliency and repeatedly lowers the danger of a breach. The advantages span the lifecycle and embody:
Stop—Prioritized threat mitigation, lowered assault floor, proactive hole identification, and enhanced resilience.
Detect—Speedy ransomware response, real-time menace isolation, predictive menace intelligence, and extra.
Reply—A single, prioritized incident queue, mechanically correlated alerts, and related menace intelligence that helps prioritize cyberthreats based mostly on severity.
Learn the e-book to be taught extra about how AI assistants like Microsoft Safety Copilot can improve unified safety by offering precious insights, automating routine duties, and correlating alerts into complete incidents.
Tackling your most crucial safety domains
Unifying safety throughout all areas of your surroundings can strengthen defenses in every space. To create a really efficient safety posture, organizations want to guard endpoints and identities, safe cloud-native purposes, defend your entire group with each safety data and occasion administration (SIEM) and prolonged detection and response (XDR), and defend the information. Within the e-book, every area is mentioned intimately with a state of affairs that fashions cyberattacker actions, the response of a unified safety method, and the improved outcomes. The e-book additionally consists of data on:
Endpoint safety—Important developments shaping endpoint safety and methods to counter ransomware and malware threats.
Id safety—Rising identity-based cyberthreats and the way united defenses can stop account takeovers.
Securing cloud-native purposes—Insights into cloud vulnerabilities and finest practices for securing trendy utility environments.
Integrating SIEM and XDR—Built-in instruments that assist handle superior, persistent threats and scale back false positives.
Defending your information—Key challenges in safeguarding delicate information and mitigating insider dangers successfully.
Getting began
A unified SOC structure is crucial to assist organizations face the present and future safety challenges. Shifting to a proactive, built-in protection means breaking down the limitations between safety features and dealing throughout silos. It means embracing and enabling AI-powered automation throughout your surroundings. And it permits for a steady loop of safety and enchancment that safety groups have to function quicker, smarter, and extra resiliently. To get began on a extra built-in, defense-in-depth method to safety, learn the Coordinated Protection: Constructing an AI-powered, unified SOC e-book now.
Study extra about AI-powered, unified SecOps from Microsoft to enhance your safety posture throughout hybrid environments with unified publicity administration and built-in, natively built-in safety controls.
Uncover much more sources: Built-in Cyberthreat Safety Assets.
To be taught extra about Microsoft Safety options, go to our web site. Bookmark the Safety weblog to maintain up with our skilled protection on safety issues. Additionally, observe us on LinkedIn (Microsoft Safety) and X (@MSFTSecurity) for the most recent information and updates on cybersecurity.
(1) Microsoft Digital Protection Report 2024