Microsoft’s Digital Crimes Unit (DCU) and worldwide companions are disrupting the main instrument used to indiscriminately steal delicate private and organizational data to facilitate cybercrime. On Tuesday, Could 13, Microsoft’s DCU filed a authorized motion in opposition to Stealer lum (“Lumma”), which is the favored info-stealing malware utilized by tons of of cyber menace actors. Lumma steals passwords, bank cards, financial institution accounts, and cryptocurrency wallets and has enabled criminals to carry colleges for ransom, empty financial institution accounts, and disrupt crucial companies.
Through a court docket order granted in the USA District Court docket of the Northern District of Georgia, Microsoft’s DCU seized and facilitated the takedown, suspension, and blocking of roughly 2,300 malicious domains that fashioned the spine of Lumma’s infrastructure. The Division of Justice (DOJ) concurrently seized the central command construction for Lumma and disrupted the marketplaces the place the instrument was bought to different cybercriminals. Europol’s European Cybercrime Middle (EC3) and Japan’s Cybercrime Management Middle (JC3) facilitated the suspension of regionally based mostly Lumma infrastructure.
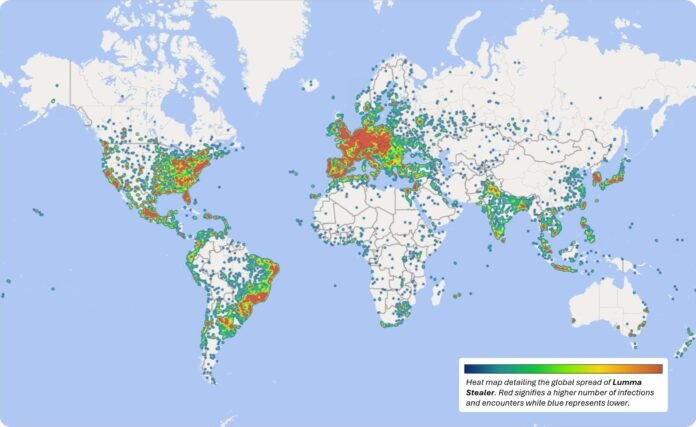
Between March 16, 2025, and Could 16, 2025, Microsoft recognized over 394,000 Home windows computer systems globally contaminated by the Luma malware. Working with regulation enforcement and trade companions, we’ve got severed communications between the malicious instrument and victims. Furthermore, greater than 1,300 domains seized by or transferred to Microsoft, together with 300 domains actioned by regulation enforcement with the assist of Europol, will probably be redirected to Microsoft sinkholes. It will enable Microsoft’s DCU to supply actionable intelligence to proceed to harden the safety of the corporate’s companies and assist defend on-line customers. These insights will even help public- and private-sector companions as they proceed to trace, examine, and remediate this menace. This joint motion is designed to gradual the velocity at which these actors can launch their assaults, decrease the effectiveness of their campaigns, and hinder their illicit earnings by reducing a significant income stream.
Warmth map detailing international unfold of Lumma Stealer malware infections and encounters throughout Home windows gadgets.
 Splash web page displayed on 900+ domains seized by Microsoft.
Splash web page displayed on 900+ domains seized by Microsoft.
What’s Lumma?
Lumma is a Malware-as-a-Service (MaaS), marketed and bought by underground boards since a minimum of 2022. Through the years, the builders launched a number of variations to repeatedly enhance its capabilities. Microsoft Risk Intelligence shares extra particulars across the supply strategies and capabilities of Lumma in a current weblog.
Sometimes, the aim of Lumma operators is to monetize stolen data or conduct additional exploitation for varied functions. Lumma is straightforward to distribute, tough to detect, and could be programmed to bypass sure safety defenses, making it a go-to instrument for cybercriminals and on-line menace actors, together with prolific ransomware actors corresponding to Octo Tempest (Scattered Spider). The malware impersonates trusted manufacturers, together with Microsoft, and is deployed by way of spear-phishing emails and malvertisingamongst different vectors.
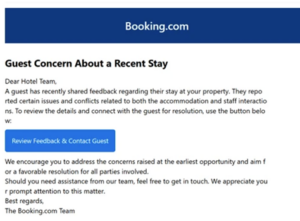
For instance, in March 2025, Microsoft Risk Intelligence recognized a phishing marketing campaign impersonating on-line journey company Reserving.com. The marketing campaign used a number of credential-stealing malware, together with Lumma, to conduct monetary fraud and theft. Lumma has additionally been used to focus on gaming communities and training programs and poses an ongoing danger to international safety, with stories from a number of cybersecurity corporations outlining its use in assaults in opposition to crucial infrastructure, such because the manufacturing, telecommunications, logistics, finance, and healthcare sectors.
Instance of phishing electronic mail impersonating Reserving.com and faux CAPTCHA verification immediate. (Supply:Microsoft – Phishing marketing campaign impersonates Reserving .com, delivers a set of credential-stealing malware)
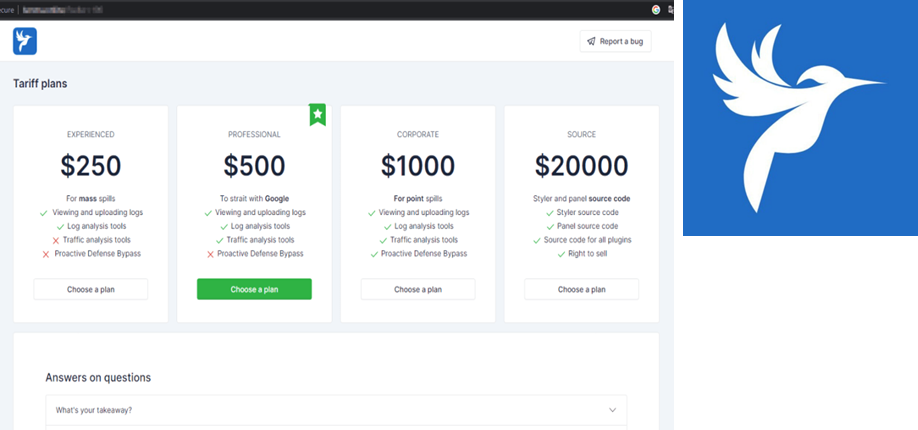
The first developer of Lumma is predicated in Russia and goes by the web alias “Shamel.” Shamel markets totally different tiers of service for Lumma by way of Telegram and different Russian-language chat boards. Relying on what service a cybercriminal purchases, they’ll create their very own variations of the malware, add instruments to hide and distribute it, and observe stolen data by a web based portal.
Totally different tiers of service for Lumma, in addition to Lumma’s brand used on advertising materials. (Supply: Darkrace – The Rise of MAAS & LUMMA INFO Stealer)
In an interview with cybersecurity researcher “g0njxa” in November 2023, Shamel shared that he had “about 400 energetic shoppers.” Demonstrating the evolution of cybercrime to include established enterprise practices, he successfully created a Lumma model, utilizing a particular brand of a hen to market his product, calling it an emblem of “peace, lightness, and tranquility,” and including the slogan “earning money with us is simply as simple.”
Shamel’s means to function overtly underscores the significance for international locations worldwide to deal with the problem of secure havens and to advocate for the rigorous enforcement of due diligence obligations underneath worldwide regulation.
Persevering with to work collectively to disrupt prolific cybercrime instruments
Disrupting the instruments cybercriminals incessantly use can create a big and lasting influence on cybercrime, as rebuilding malicious infrastructure and sourcing new exploit instruments takes time and prices cash. By severing entry to mechanisms cybercriminals use, corresponding to Lumma, we will considerably disrupt the operations of numerous malicious actors by a single motion.
Continued collaboration throughout trade and authorities stays crucial. We’re grateful for the partnership with others throughout authorities and trade, together with cybersecurity corporations ESET, Bitsight, Lumen, Cloudflare, CleanDNSand GMO Registry. Every firm supplied useful help by shortly taking down on-line infrastructure.
Lastly, we all know cybercriminals are persistent and artistic. We, too, should evolve to establish new methods to disrupt malicious actions. Microsoft’s DCU will proceed to adapt and innovate to counteract cybercrime and assist guarantee the security of crucial infrastructure, clients, and on-line customers.
Organizations and people can defend themselves from malware like Lumma through the use of multi-factor authentication, working the most recent anti-malware software program, and being cautious with attachments and electronic mail hyperlinks. Extra data for safety professionals could be discovered right here.