Hackers began exploiting a high-severity flaw that permits bypassing authentication within the OttoKit (previously SureTriggers) plugin for WordPress simply hours after public disclosure.
Customers are strongly really useful to improve to the newest model of OttoKit/SureTriggers, at present 1.0.79, launched at the start of the month.
The OttoKit WordPress plugin permits customers to attach plugins and exterior instruments like WooCommerce, Mailchimp, and Google Sheets, automate duties like sending emails and including customers, or updating CRMs with out code. Statistics present that the product is lively on 100,000 web sites.
Yesterday, Wordfence disclosed an authentication bypass vulnerability in OttoKit, recognized as CVE-2025-3102. The flaw impacts all variations of SureTriggers/OttoKit as much as 1.0.78.
The flaw stems from a lacking empty worth test within the authenticate_user() perform, which handles REST API authentication. Exploitation to be doable if the plugin will not be configured with an API key, which causes the saved secret_key to stay empty.
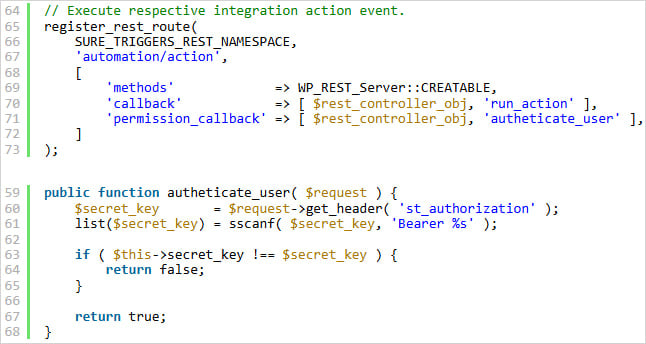 The weak code
The weak code
Supply: Wordfence
An attacker may exploit this by sending an empty st_authorization header to cross the test and grant unauthorized entry to protected API endpoints.
Basically, CVE-2025-3102 permits attackers to create new administrator accounts with out authentication, posing a excessive danger of full website takeover.
Wordfence acquired a report concerning the flaw from safety researcher ‘mikemyers’, who earned a bounty of $1,024 for the invention in mid-March.
The plugin vendor was contacted on April 3 with the total exploitation particulars, they usually launched a repair by way of model 1.0.79 on the identical day.
Nonetheless, hackers shortly jumped on the alternative to use the difficulty, benefiting from directors’ delay in updating the plugin to handle the safety drawback.
Researchers at WordPress safety platform Patchstack are warning that the primary exploitation makes an attempt within the wild have been logged only some hours after the disclosure of the flaw.
“Attackers have been fast to use this vulnerability, with the primary recorded try occurring simply 4 hours after it was added as a vPatch to our database,” experiences Patchstack.
“This swift exploitation highlights the essential want to use patches or mitigations instantly upon the general public disclosure of such vulnerabilities,” the researchers say.
The risk actors try to create new administrator accounts utilizing randomized username/password and e mail handle mixture, an indication of process automation.
If you happen to’re utilizing OttoKit/SureTriggers, improve to model 1.0.79 as quickly as doable and test logs for sudden admin accounts or different person roles, set up of plugins/themes, database entry occasions, and modification of safety settings.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and the way to defend in opposition to them.





