A risk actor tracked as ‘Hazy Hawk’ is hijacking forgotten DNS CNAME data pointing to deserted cloud providers, taking on trusted subdomains of governments, universities, and Fortune 500 firms to distribute scams, pretend apps, and malicious advertisements.
Based on Infoblox researchers, Hazy Hawk first scans for domains with CNAME data pointing to deserted cloud endpoints, which they decide through passive DNS knowledge validation.
Subsequent, they register a brand new cloud useful resource with the identical title because the one within the deserted CNAME, inflicting the unique area’s subdomain to resolve to the risk actor’s new cloud-hosted web site.
Utilizing this system, the risk actors hijacked a number of domains to cloak malicious actions, host rip-off content material, or use them as redirection hubs for rip-off operations.
Some notable examples of the hijacked domains embrace:
cdc.gov – U.S. Facilities for Illness Management and Prevention
honeywell.com – Multinational conglomerate
berkeley.edu – College of California, Berkeley
michelin.co.uk – Michelin Tires UK
ey.com, pwc.com, deloitte.com – International “Massive 4” consulting corporations
ted.com – Well-known nonprofit media group (TED Talks)
well being.gov.au – Australian Division of Well being
unicef.org – United Nations Youngsters’s Fund
nyu.edu – New York College
unilever.com – International Shopper Items Firm
ca.gov – California State Authorities
The entire checklist of compromised domains will be discovered within the Infoblox report.
As soon as the risk actor positive aspects management of a subdomain, they generate tons of of malicious URLs underneath it, which seem reliable in engines like google as a result of mum or dad area’s excessive belief rating.
Victims clicking on the URLs are redirected by means of layers of domains and TDS infrastructure that profile them based mostly on their machine kind, IP tackle, VPN use, and so forth., to qualify victims.
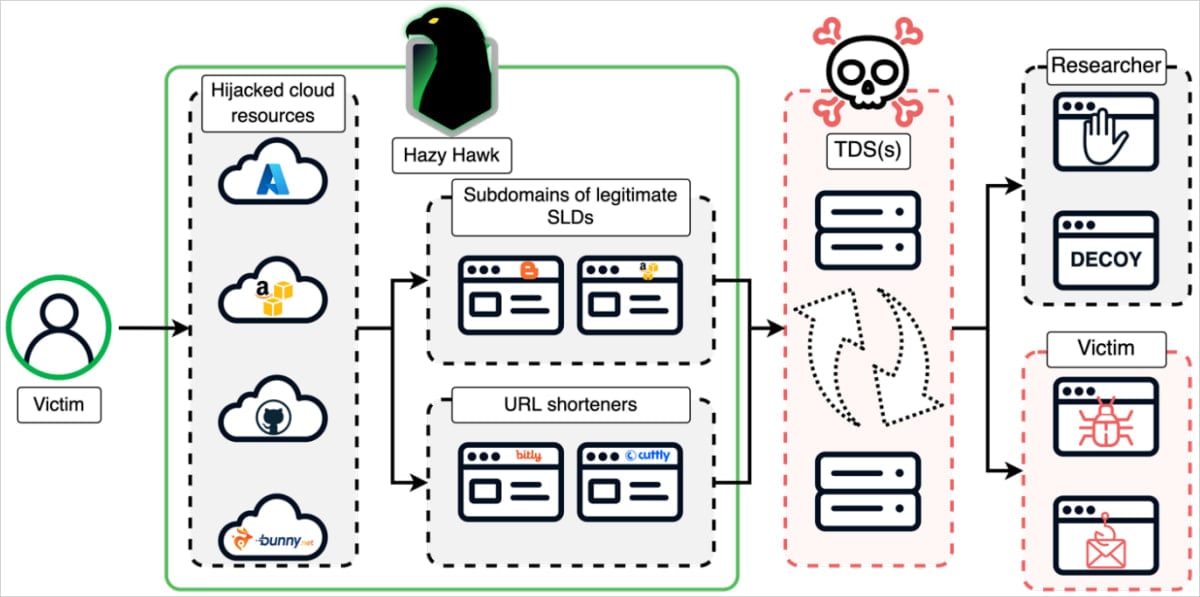 Overview of the Hazy Hawk assault
Overview of the Hazy Hawk assault
Supply: Infoblox
Infoblox’s report says the websites are used for tech assist scams, bogus antivirus alerts, pretend streaming/porn websites, and phishing pages.
Customers tricked into permitting browser push notifications get persistent alerts even after they go away the rip-off websites, which might generate important income for Hazy Hawk.
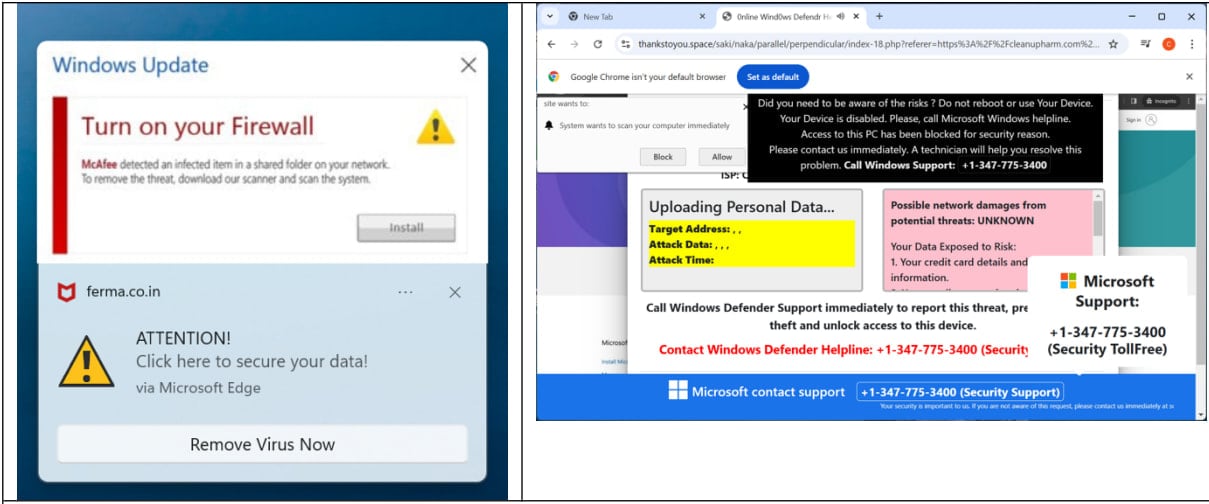 Push notification examples from the marketing campaign
Push notification examples from the marketing campaign
Supply: Infoblox
The identical researchers reported beforehand about one other risk actor, ‘Savvy Seahorse,’ who additionally abused CNAME data to construct an atypical TDS that redirected customers to pretend funding platforms.
It is simple to miss CNAME data, so they’re susceptible to stealthy abuse, and it seems that an growing variety of risk actors notice this and try and take benefit.
Within the case of Hazy Hawk, the operation’s success additionally depends on organizations failing to delete DNS data after cloud providers are decommissioned, which allows attackers to copy the unique useful resource title with out authentication.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and easy methods to defend towards them.





