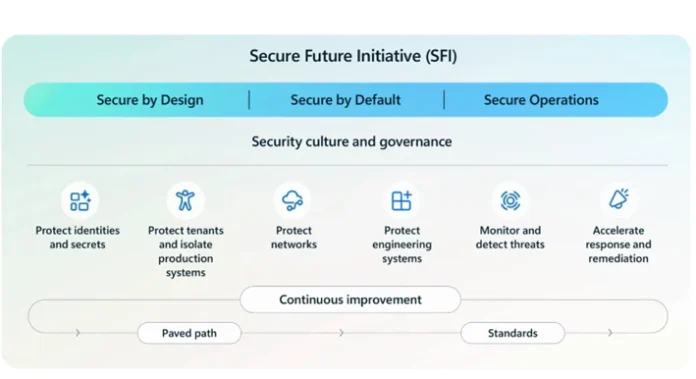
We’re excited to launch Microsoft Safe Future Initiative (SFI) patterns and practices: a brand new library of actionable steering designed to assist organizations implement safety measures at scale.
This launch marks the following step in our journey to make our SFI learnings sensible for our prospects, companions, and broader safety ecosystem. These patterns and practices draw from a variety of confirmed safety architectures and finest practices—together with, however not restricted to, Zero Belief—operationalized to guard Microsoft’s infrastructure and now shared that can assist you do the identical.
Why SFI patterns and practices matter
Moreover, we have now heard suggestions from prospects and companions that need us to share how we’re bettering safety at Microsoft, not simply on the strategic structure degree but additionally on the implementation and sensible degree. That’s the place SFI patterns and practices library comes into play.
What’s within the first wave of SFI patterns and practices?
We’re launching the primary wave of eight sample and apply articles that assist clear up probably the most asked-for, pressing, and sophisticated challenges confronted by safety practitioners at the moment:
Sample nameSFI pillarWhat it helps you doPhishing-resistant multi-factor authentication (MFA)Defending identities and secretsTraditional MFA is now not sufficient. This sample helps organizations shift to cryptographic, phishing-resistant authentication utilizing FIDO2, passkeys, and certificate-based strategies—decreasing publicity to credential-based cyberattacks.
Substitute weak MFA with cryptographic, phishing-resistant strategies.
Remove id lateral motionIsolating tenants and manufacturing systemsCyberattackers typically exploit id pivot paths to escalate privileges. This sample outlines learn how to phase entry, implement Conditional Entry, and block dangerous visitor authentication to forestall silent intrusions.
Forestall cyberattackers from pivoting throughout tenants and roles.
Take away legacy techniques that danger safetyIsolating tenants and manufacturing systemsUnmanaged tenants and legacy infrastructure introduce configuration drift and assault floor. Microsoft eliminated greater than 5.75 million inactive tenants—this sample exhibits how you are able to do the identical.
Decommission unmanaged tenants and legacy infrastructure.
Standardize safe growth pipelinesDefending engineering systemsCI/CD pipelines are sometimes fragmented and inconsistent. This sample helps you implement ruled templates that implement safety gates, encourages creation of Software program Invoice of Supplies (SBOMs) and streamline compliance.
Use ruled CI/CD templates to implement safety and compliance.
Full manufacturing infrastructure stockMonitoring and detecting threatsYou can’t defend what you’ll be able to’t see. This sample guides organizations in constructing real-time asset inventories, centralizing telemetry, and eradicating unused purposes to cut back danger.
Keep real-time visibility into all property and telemetry.
Fast anomaly detection and responseMonitoring and detecting threatsModern cyberattackers transfer quick. This sample exhibits learn how to use AI, consumer entity and habits analytics (UEBA), and centralized logging to detect suspicious habits and automate response—decreasing dwell time and bettering safety operations middle (SOC) effectivity.
Use AI and behavioral analytics to detect and reply to cyberthreats quicker.
Safety log retention requirementsMonitoring and detecting threatsLogs are the spine of detection and forensics. This sample helps you standardize codecs, centralize entry, and prolong retention to help long-term investigations and compliance.
Standardize, centralize, and prolong log retention for higher detection and forensics.
Speed up vulnerability mitigationAccelerating response and remediationEffective vulnerability administration is important to decreasing danger in complicated digital environments by enabling quicker, systematic responses to safety threats. Automation, built-in workflows, and enriched communications can considerably speed up mitigation timelines and enhance organizational resilience.
Automate detection, triage, and patching to cut back time-to-mitigate.
Introducing SFI patterns and practices taxonomy

Simply as software program design patterns present reusable options to frequent engineering issues, SFI patterns and practices supply repeatable, confirmed approaches to fixing complicated cybersecurity challenges. Every sample is crafted to handle a particular safety danger—whether or not it’s id lateral motion, legacy infrastructure, or inconsistent steady integration and steady supply (CI/CD) pipelines—and is grounded in Microsoft’s personal expertise. Like design patterns in software program structure, these safety patterns are modular, extensible, and constructed for reuse throughout various environments.
Moreover, every sample within the SFI patterns and practices library follows a constant and purposeful construction. Each article begins with a sample identify—a concise deal with that captures the essence of the cybersecurity problem. The issue part outlines the safety danger and its real-world context, serving to readers perceive why it issues. The answer describes how Microsoft addressed the difficulty internally. The steering part gives sensible suggestions that prospects can think about making use of in their very own environments. Lastly, the implications part outlines the outcomes and trade-offs of implementing the sample, serving to organizations anticipate each the advantages and the operational issues.
This construction gives a framework for understanding, making use of, and evolving safety practices.
Becoming a member of the SFI patterns and practices journey
SFI patterns and practices is your information to turning structure into motion. By adopting these patterns, organizations can speed up their safety maturity, cut back implementation friction, and construct techniques which might be safer by design, default, and in operation.
What’s coming subsequent?
That is just the start. Within the coming months, we’ll launch extra patterns to share extra steering aligned to SFI pillars. Every new sample can be revealed on the Microsoft Safety weblog and on Microsoft’s Safe Future Initiative homepage.
Get began
Discover the primary set of patterns:
Let’s construct a safe future, collectively
Discuss to your Microsoft account group to combine these practices into your roadmap.
To be taught extra about Microsoft Safety options, go to our web site. Bookmark the Safety weblog to maintain up with our skilled protection on safety issues. Additionally, comply with us on LinkedIn (Microsoft Safety) and X (@MSFTSecurity) for the most recent information and updates on cybersecurity.