A big safety hole in Linux runtime safety attributable to the ‘io_uring’ interface permits rootkits to function undetected on techniques whereas bypassing superior Enterprise safety software program.
The flaw was found by ARMO safety researchers who developed a proof-of-concept rootkit referred to as “Curing” to reveal the practicality and feasibility of assaults leveraging io_uring for evasion.
io_uring is a Linux kernel interface for environment friendly, asynchronous I/O operations. It was launched in 2019 with Linux 5.1 to deal with efficiency and scalability points with the standard I/O system.
As an alternative of counting on system calls that trigger plenty of overhead and course of hangs, io_uring makes use of ring buffers shared between applications and the system kernel to queue up I/O requests that might be processed asynchronously, permitting this system to maintain working.
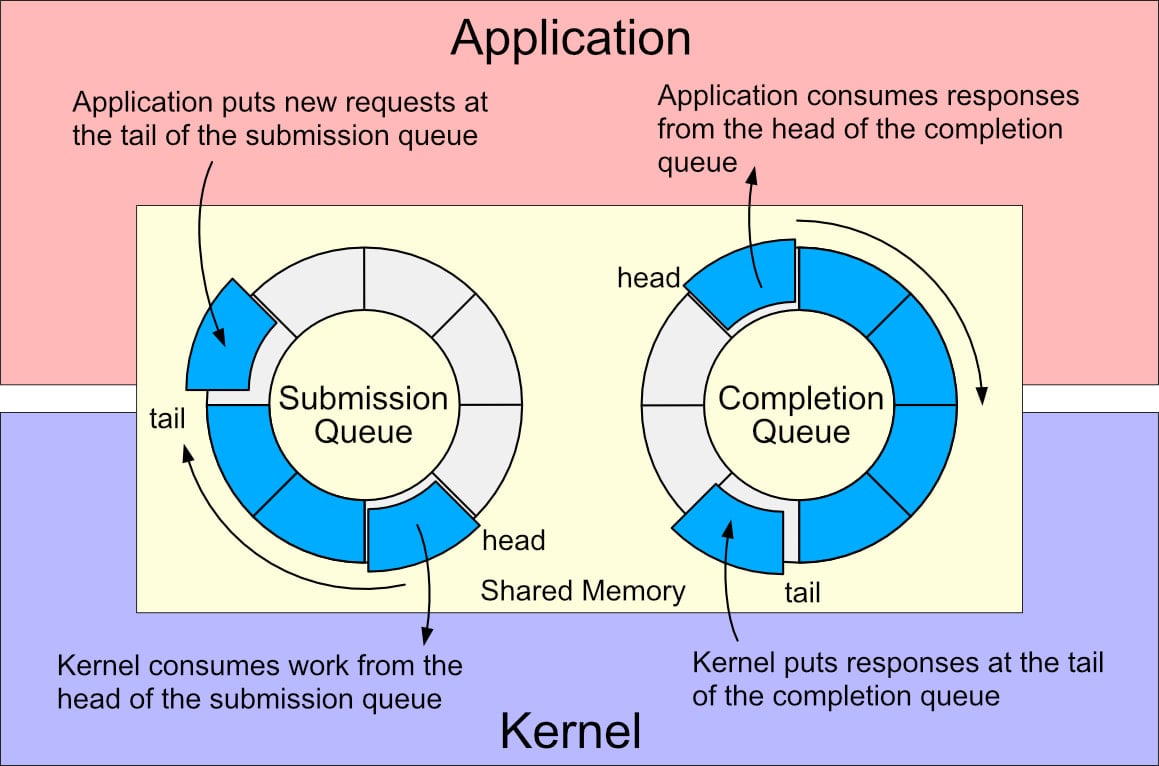 io_uring process submission and completion rings
io_uring process submission and completion rings
Supply: Donald Hunter
The issue, in line with ARMO, arises from the truth that most safety instruments monitor for suspicious syscalls and hooking (like ‘ptrace’ or ‘seccomp’), utterly ignoring something that entails the io_ring, creating a really harmful blindspot.
The researchers clarify that io_uring helps a big selection of operations via 61 ops varieties, together with file learn/writes, creating and accepting community connections, spawning processes, modifying file permissions, and studying listing contents, making it a robust rootkit vector.
Such is the chance that Google determined to flip it off by default on Android and ChromeOS, which use the Linux kernel and inherit a lot of its underlying vulnerabilities.
To place concept into testing, ARMO created Curing, a special-purpose rootkit that abuses io_uring to drag instructions from a distant server and execute arbitrary operations with out triggering syscall hooks.
Testing Curing towards a number of well-known runtime safety instruments demonstrated that almost all could not detect its exercise.
Particularly, Falco was discovered to be fully blind even when customized detection guidelines have been used, whereas Tetragon confirmed an lack of ability to flag malicious exercise underneath the default configuration.
Tetragon, although, doesn’t think about its platform weak as monitoring will be enabled to detect this rootkit.
“We reported this to the Tetragon group and their response was that from their perspective Tetragon shouldn’t be “weak” as they supply the flexibleness to hook principally wherever,” explains the researchers.
“They identified an excellent weblog submit they wrote concerning the topic.”
Testing towards industrial instruments, ARMO additional confirmed the lack to detect io_uring-based malware and kernel interactions that do not contain syscalls. Nevertheless, ARMO didn’t share what industrial applications they examined once more.
For many who need to take a look at their environments towards this risk, ARMO has made Curing accessible free of charge on GitHub.
ARMO means that the issue will be solved with the adoption of Kernel Runtime Safety Instrumentation (KRSI), which permits eBPF applications to be hooked up to security-relevant kernel occasions.





I love how you write—it’s like having a conversation with a good friend. Can’t wait to read more!This post pulled me in from the very first sentence. You have such a unique voice!Seriously, every time I think I’ll just skim through, I end up reading every word. Keep it up!Your posts always leave me thinking… and wanting more. This one was no exception!Such a smooth and engaging read—your writing flows effortlessly. Big fan here!Every time I read your work, I feel like I’m right there with you. Beautifully written!You have a real talent for storytelling. I couldn’t stop reading once I started.The way you express your thoughts is so natural and compelling. I’ll definitely be back for more!Wow—your writing is so vivid and alive. It’s hard not to get hooked!You really know how to connect with your readers. Your words resonate long after I finish reading.