A brand new post-exploitation command-and-control (C2) evasion technique known as ‘Ghost Calls’ abuses TURN servers utilized by conferencing apps like Zoom and Microsoft Groups to tunnel site visitors by means of trusted infrastructure.
Ghost Calls makes use of official credentials, WebRTC, and customized tooling to bypass most present defenses and anti-abuse measures, with out counting on an exploit.
This new tactic was offered by Praetorian‘s safety researcher Adam Crosser at BlackHat USA, the place it was highlighted that the brand new method can be utilized by Crimson Groups when performing penetration emulation workouts.
“We leverage net conferencing protocols, that are designed for real-time, low-latency communication and function by means of globally distributed media servers that perform as pure site visitors relays,” reads the presentation’s briefing.
“This method permits operators to mix interactive C2 periods into regular enterprise site visitors patterns, showing as nothing greater than a quickly joined on-line assembly.”
How Ghost Calls works
TURN (Traversal Utilizing Relays round NAT) is a networking protocol generally utilized by video name, VoIP, and WebRTC companies that helps units behind NAT firewalls talk with one another when a direct connection is just not attainable.
When a Zoom or Groups shopper joins a gathering, it receives momentary TURN credentials that the Ghost Calls can hijack to arrange a TURN-based WebRTC tunnel between the attacker and the sufferer.
This tunnel can then be used to proxy arbitrary information or disguise C2 site visitors as common video conferencing site visitors by means of trusted infrastructure utilized by Zoom or Groups.
Because the site visitors is routed by means of official domains and IPs which might be extensively used within the enterprise, malicious site visitors can bypass firewalls, proxies, and TLS inspection. Moreover, WebRTC site visitors is encrypted, so it is effectively hidden.
By abusing these instruments, attackers additionally keep away from exposing their very own domains and infrastructure whereas having fun with high-performance, dependable connectivity, and the adaptability of utilizing each UDP and TCP over port 443.
Compared, conventional C2 mechanisms are gradual, conspicuous, and sometimes lack the real-time change capabilities required to facilitate VNC operations.
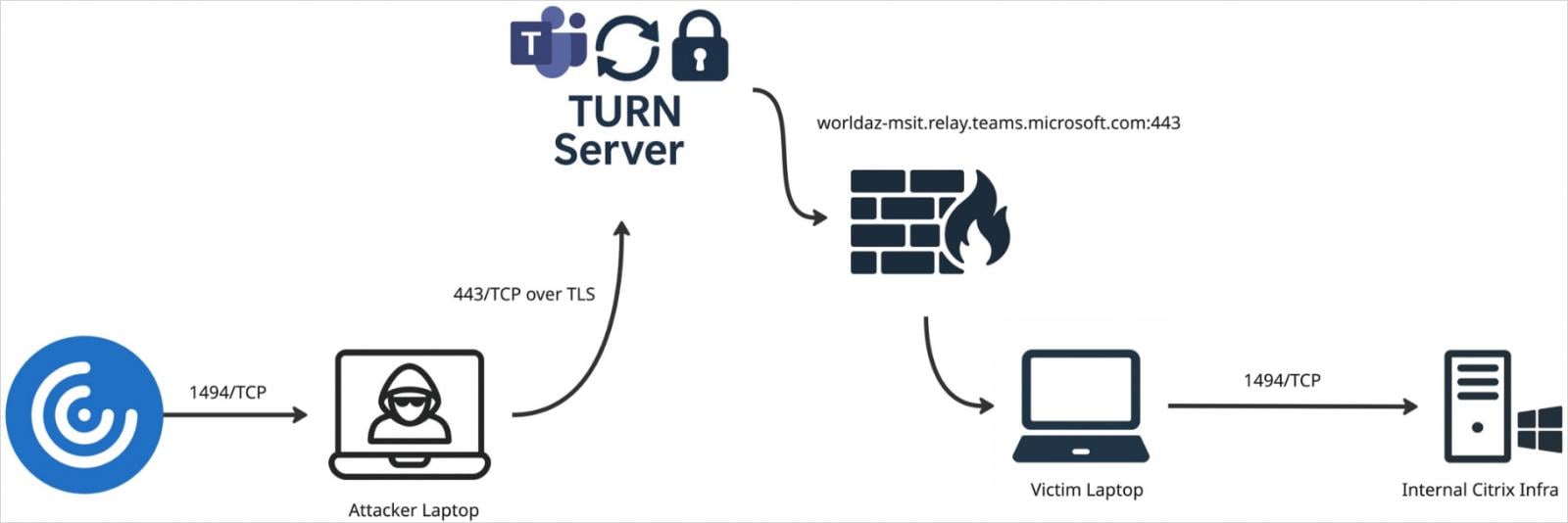 Native port forwarding through Ghost Calls
Native port forwarding through Ghost Calls
Supply: Praetorian
TURNt-ing it
Crosser’s analysis culminated with the event of a customized open-source (accessible on GitHub) utility known as ‘TURNt’ that can be utilized for tunneling C2 site visitors through WebRTC TURN servers offered by Zoom and Groups.
TURNt consists of two elements, particularly a Controller working on the attacker’s facet, and a Relay deployed on a compromised host.
The Controller runs a SOCKS proxy server to simply accept connections tunneled by means of TURN. Relay connects again to the Controller utilizing TURN credentials, and units up a WebRTC information channel by means of the supplier’s TURN server.
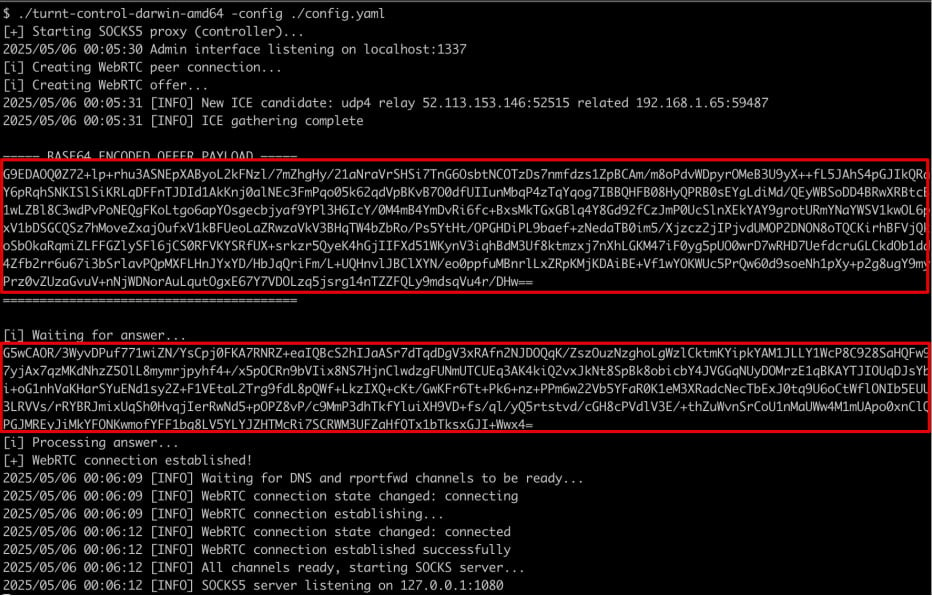 SOCKS proxying on TURNt
SOCKS proxying on TURNt
Supply: Praetorian
TURNt can carry out SOCKS proxying, native or distant port forwarding, information exfiltration, and facilitate hidden VNC (Digital Community Computing) site visitors tunneling.
Though Ghost Calls doesn’t exploit any vulnerabilities in Zoom or Microsoft Groups, BleepingComputer has contacted each distributors to ask in the event that they plan to introduce further safeguards to scale back its feasibility. We are going to replace this publish as soon as we obtain a response from both.
Malware focusing on password shops surged 3X as attackers executed stealthy Good Heist situations, infiltrating and exploiting crucial methods.
Uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and how you can defend in opposition to them.





