Regardless of Oracle denying a breach of its Oracle Cloud federated SSO login servers and the theft of account knowledge for six million individuals, BleepingComputer has confirmed with a number of firms that related knowledge samples shared by the menace actor are legitimate.
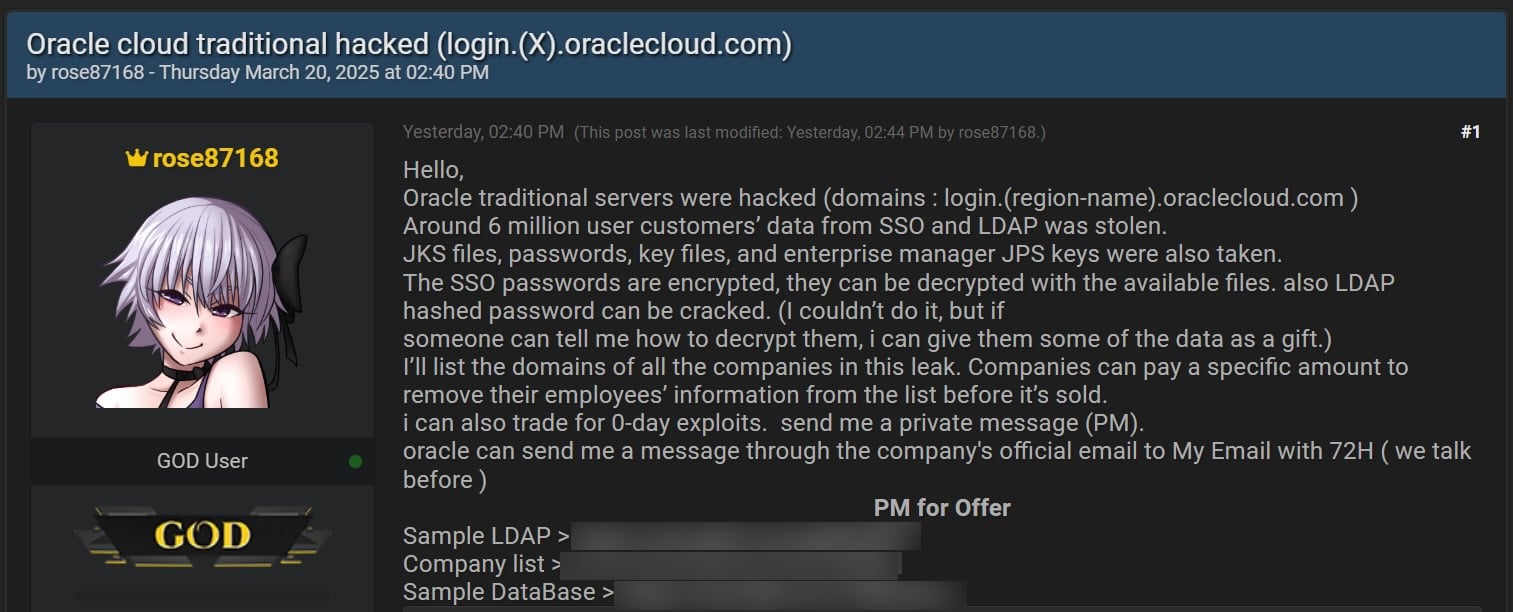
Final week, an individual named ‘rose87168’ claimed to have breached Oracle Cloud servers and started promoting the alleged authentication knowledge and encrypted passwords of 6 million customers. The menace actor additionally stated that stolen SSO and LDAP passwords might be decrypted utilizing the data within the stolen recordsdata and provided to share a number of the knowledge with anybody who may assist get better them.
The menace actor launched a number of textual content recordsdata consisting of a database, LDAP knowledge, and an inventory of 140,621 domains of firms that had been allegedly impacted by the breach. It must be famous that a number of the firm domains seem like assessments, and there are a number of domains per firm.
 Menace actor promoting allegedly stolen Oracle Cloud knowledge
Menace actor promoting allegedly stolen Oracle Cloud knowledge
Supply: BleepingComputer
Along with the info, rose87168 shared an Archive.org URL with BleepingComputer for a textual content file hosted on the “login.us2.oraclecloud.com” server that contained their e-mail handle. This file signifies that the menace actor may create recordsdata on Oracle’s server, indicating an precise breach.
Nonetheless, Oracle has denied that it suffered a breach of Oracle Cloud and has refused to reply to any additional questions in regards to the incident.
“There was no breach of Oracle Cloud. The revealed credentials aren’t for the Oracle Cloud. No Oracle Cloud prospects skilled a breach or misplaced any knowledge,” the corporate instructed BleepingComputer final Friday.
This denial, nonetheless, contradicts findings from BleepingComputer, which obtained further samples of the leaked knowledge from the menace actor and contacted the related firms.
Representatives from these firms, all who agreed to verify the info below the promise of anonymity, confirmed the authenticity of the knowledge. The businesses acknowledged that the related LDAP show names, e-mail addresses, given names, and different figuring out data had been all right and belonged to them.
The menace actor additionally shared emails with BleepingComputer, claiming to be a part of an change between them and Oracle.
One e-mail exhibits the menace actor contacting Oracle’s safety e-mail (secalert_us@oracle.com) to report that they hacked the servers.
“I’ve dug into your cloud dashboard infrastructure and located a large vulnerability that has handed me full entry to data on 6 million customers,” reads the e-mail seen by BleepingComputer.
One other e-mail thread shared with BleepingComputer exhibits an change between the menace actor and somebody utilizing a ProtonMail e-mail handle who claims to be from Oracle. BleepingComputer has redacted the e-mail handle of this different individual as we couldn’t confirm their identification or the veracity of the e-mail thread.
On this e-mail change, the menace actor says somebody from Oracle utilizing a @proton.me e-mail handle instructed them that “We obtained your emails. Let’s use this e-mail for all communications any more. Let me know if you get this.”
Cybersecurity agency Cloudsek has additionally discovered an Archive.org URL exhibiting that the “login.us2.oraclecloud.com” server was working Oracle Fusion Middleware 11g as of February 17, 2025. Oracle has since taken this server offline after information of the alleged breach was reported.
This model of the software program was impacted by a vulnerability tracked as CVE-2021-35587 that allowed unauthenticated attackers to compromise Oracle Entry Supervisor. The menace actor claimed that this vulnerability was used within the alleged breach of Oracle’s servers.
BleepingComputer has emailed Oracle quite a few occasions about this data however has not obtained any response.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and find out how to defend towards them.





