Greater than 46,000 internet-facing Grafana situations stay unpatched and uncovered to a client-side open redirect vulnerability that enables executing a malicious plugin and account takeover.
The flaw is tracked as CVE-2025-4123 and impacts a number of variations of the open-source platform used for monitoring and visualizing infrastructure and utility metrics.
The vulnerability was found by bug bounty hunter ALVARO BALADA and was addressed in safety updates that Grafana Labs launched on Could 21.
Nonetheless, as of scripting this, greater than a 3rd of all Grafana situations reachable over the general public web haven’t been patched, in keeping with researchers at aplication safety firm OX Safety, who check with the bug as ‘The Grafana Ghost’.
The analysts informed BleepingComputer that their work centered on demonstrating the power to weaponize Balada’s discovering.
After figuring out variations susceptible to the assault, they assesed the publicity by correlating the info with the platform’s distribution throughout the ecosystem.
They discovered 128,864 situations uncovered on-line, with 46,506 nonetheless operating susceptible variations that may nonetheless be exploited. This corresponds to a share of about 36%.
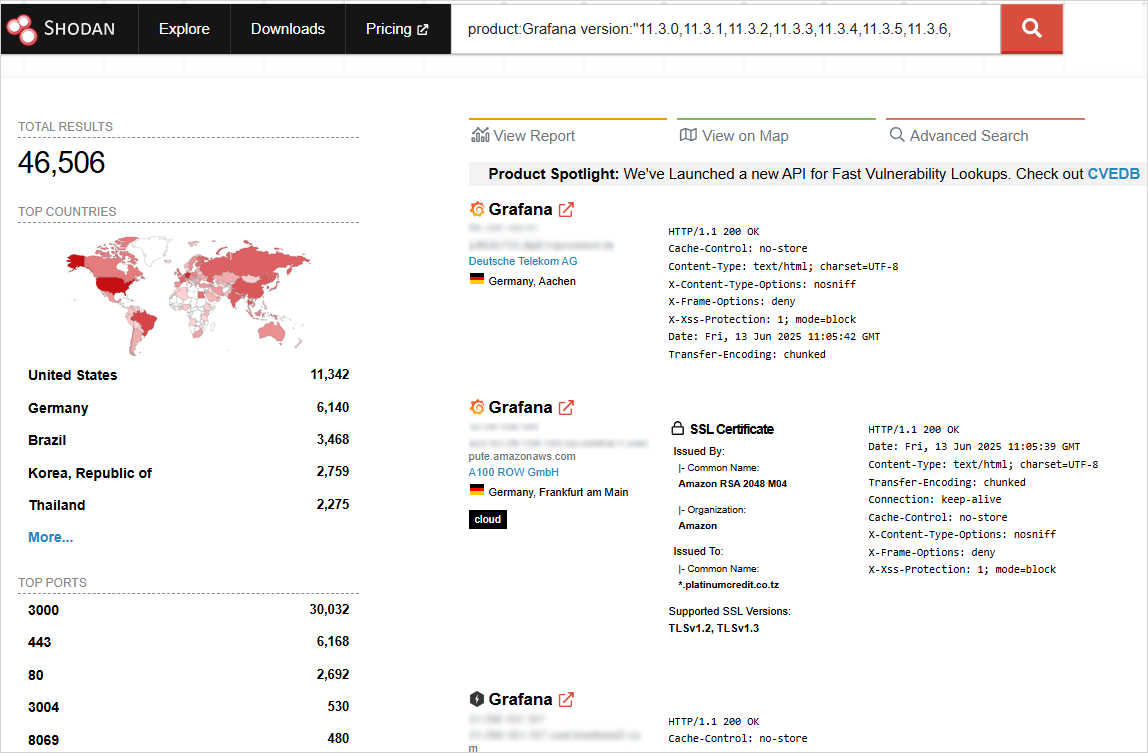 Weak Grafana endpoints
Weak Grafana endpoints
Supply: BleepingComputer
OX Safety’s in-depth evaluation of CVE-2025-4123 uncovered that, via a sequence of exploitation steps combining client-side path traversal with open redirect mechanics, attackers can lure victims into clicking URLs that result in loading a malicious Grafana plugin from a web site managed by the risk actor.
The malicious hyperlinks could possibly be used to execute arbitrary JavaScript within the person’s browser, the researchers say.
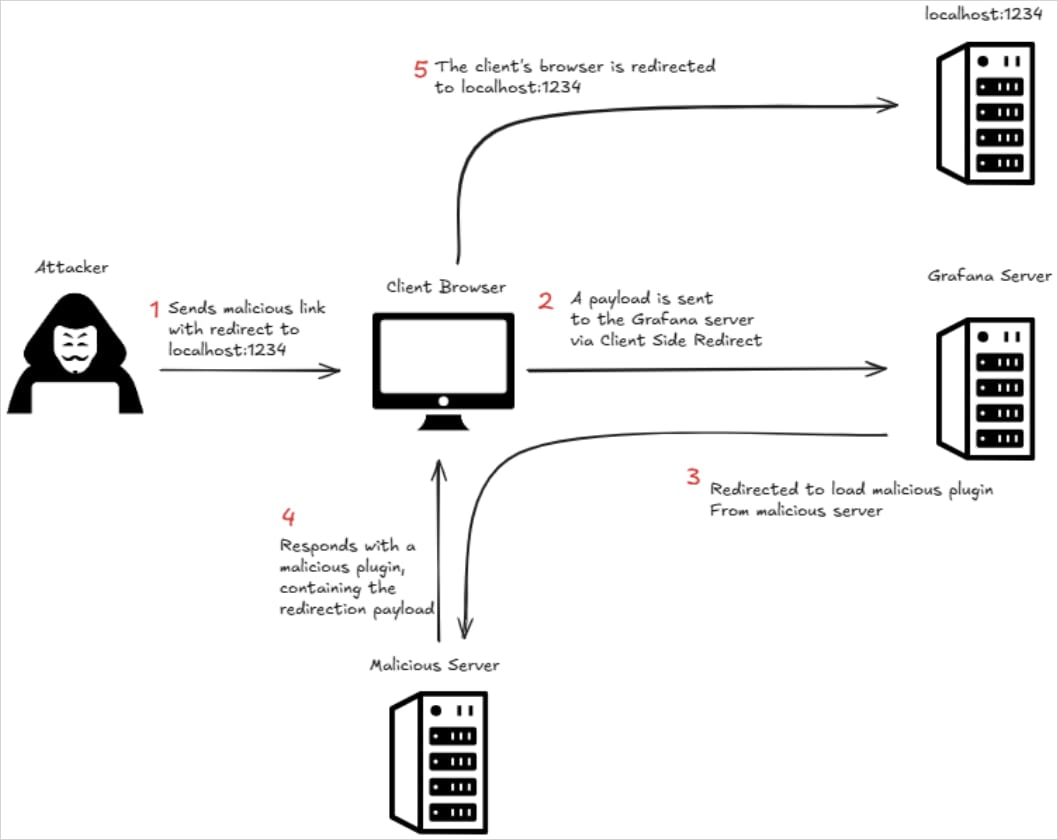 The exploitation course of
The exploitation course of
Supply: OX Safety
The exploit doesn’t require elevated privileges and might operate even when nameless entry is enabled.
The flaw permits attackers to hijack person classes, change account credentials, and, in instances the place the Grafana Picture Renderer plugin is put in, carry out server-side request forgery (SSRF) to learn inside assets.
Whereas the default Content material Safety Coverage (CSP) in Grafana gives some safety, it doesn’t forestall exploitation attributable to limitations in client-side enforcement.
OX Safety’s exploit demonstrates that CVE-2025-4123 could be exploited client-side and could possibly be leveraged to bypass fashionable browser normalization mechanisms by via JavaScript routing logic native to Grafana.
This permits attackers to take advantage of URL dealing with inconsistencies to serve malicious plugins, which in flip modify person electronic mail addresses, making account hijacking through password resets trivial.
Though CVE-2025-4123 has a number of exploitation necessities, like person interplay, an energetic person session when the sufferer clicks the hyperlink, and having the plugin function enabled (is enabled by default), the massive variety of uncovered situations and the dearth for want of authentication create a big assault floor.
To mitigate the danger of exploitation, it is strongly recommended that Grafana directors improve to variations 10.4.18+security-01, 11.2.9+security-01, 11.3.6+security-01, 11.4.4+security-01, 11.5.4+security-01, 11.6.1+security-01, and 12.0.0+security-01.
Patching used to imply advanced scripts, lengthy hours, and infinite fireplace drills. Not anymore.
On this new information, Tines breaks down how fashionable IT orgs are leveling up with automation. Patch quicker, scale back overhead, and concentrate on strategic work — no advanced scripts required.





