In a reasonably intelligent assault, hackers leveraged a weak spot that allowed them to ship a faux e mail that appeared delivered from Google’s techniques, passing all verifications however pointing to a fraudulent web page that collected logins.
The attacker leveraged Google’s infrastructure to trick recipients into accessing a legitimate-looking “assist portal” that asks for Google account credentials.
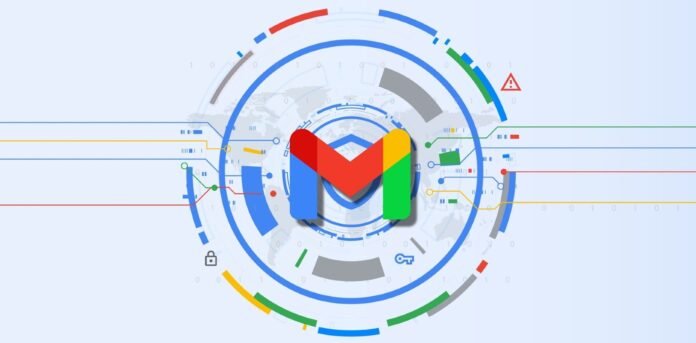
The fraudulent message appeared to come back from “no-reply@google.com” and handed the DomainKeys Recognized Mail (DKIM) authentication technique however the actual sender was totally different.
Faux e mail with Google’s DKIM stamp
Nick Johnsonthe lead developer of the Ethereum Title Service (ENS), obtained a safety alert that appeared to be from Google, informing him of a subpoena from a legislation enforcement authority asking for his Google Account content material.
Nearly all the things seemed authentic and Google even positioned it with different authentic safety alerts, which might doubtless trick much less technical customers that don’t know the place to search for the indicators of fraud.
 Phishing e mail relayed by way of Google techniques
Phishing e mail relayed by way of Google techniques
supply: Nick Johnson
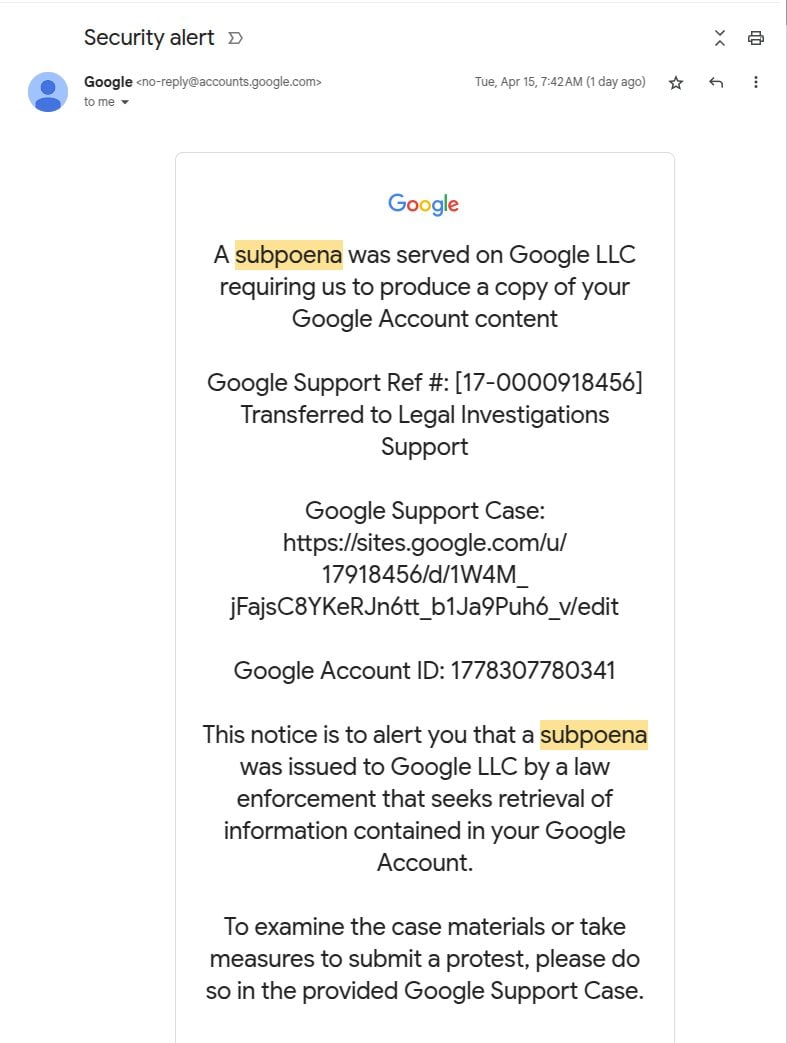
Nonetheless, Johnson’s eager eye noticed that the faux assist portal within the e mail was hosted on websites.google.com – Google’s free web-building platform, which raised suspicion.
Being on a Google area, the probabilities of the recipient to understand they’re being focused are decrease.
Johnson says the faux assist portal was “a precise duplicate of the actual factor” and “the one trace it is a phish is that it is hosted on websites.google.com as an alternative of accounts.google.com.”
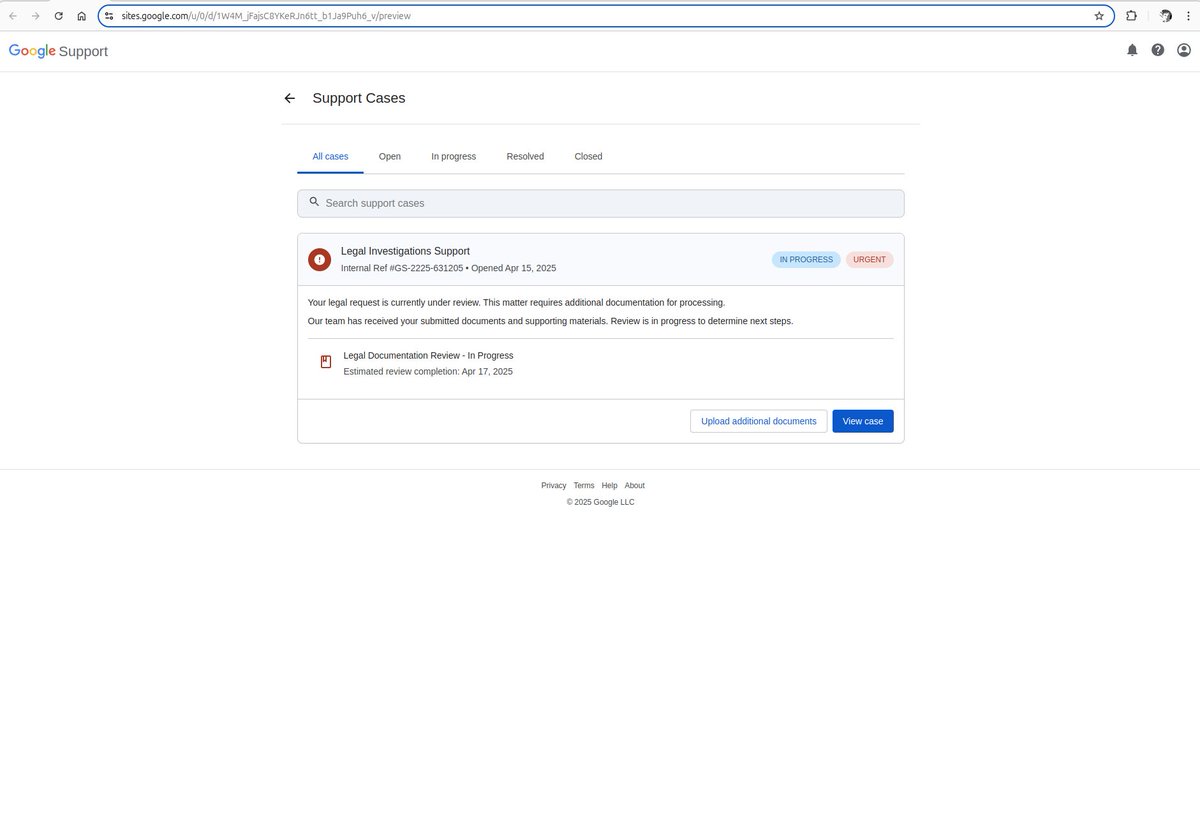 Faux Google assist portal
Faux Google assist portal
supply: Nick Johnson
The developer believes that the aim of the fraudulent web site was to gather credentials to compromise the recipient’s account.
The faux portal is simple to clarify within the rip-off however the intelligent half is delivering a message that seems to have handed Google’s DKIM verification in what is known as a DKIM replay phishing assault.
A more in-depth have a look at the e-mail particulars reveals that the mailed-by header exhibits a special tackle than Google’s no-reply and the recipient is a me@ tackle at a site made to appear like it’s managed by Google.
However, the message was signed and delivered by Google.
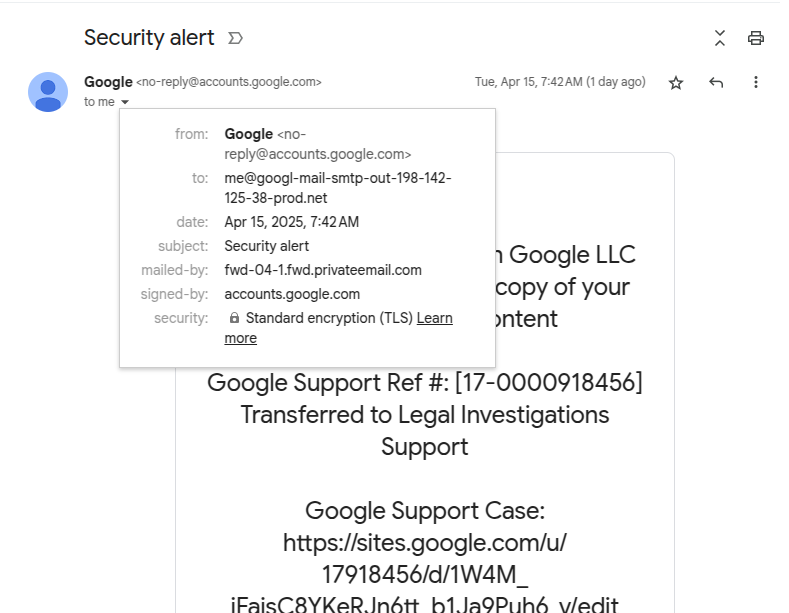 Electronic mail headers present actual recipient and supply addresses
Electronic mail headers present actual recipient and supply addresses
supply: Nick Johnson
Johnson put the clues collectively and found the fraudster’s tips.
“First, they register a site and create a Google account for me@area’. The area is not that vital however it helps if (sic) appears like some type of infra. The selection of ‘me’ for the username is intelligent,” the developer explains.
The attacker then created a Google OAuth app and used for its identify your entire phishing message. At one level, the message contained plenty of whitespace to make it appear like it ended and to separate it from Google’s notification about accessing the attacker’s me@area e mail tackle.
When the attacker granted their OAuth app entry to their e mail tackle in Google Workspace, Google mechanically despatched a safety alert to that inbox.
“Since Google generated the e-mail, it is signed with a sound DKIM key and passes all of the checks,” Johnson says, including that the final step was to ahead the safety alert to victims.
The weak spot in Google’s techniques is that DKIM checks solely the message and the headers, with out the envelope. Thus, the faux e mail passes signature validation and seems authentic within the recipient’s inbox.
Moreover, by naming the fraudulent tackle me@, Gmail will present the message as if it was delivered to the sufferer’s e mail tackle.
EasyDMARC, an e mail authentication firm, additionally detailed the DKIM replay phishing assault Johnson described and supplied technical explanations for every step.
PayPal choice abused in the identical approach
An identical trick has been tried on different platforms than Google. In March, a marketing campaign focusing on PayPal customers relied on the identical technique, the place fraudulent messages originated from the monetary firm’s mail servers and handed DKIM safety checks.
BleepingComputer’s checks revealed that the attacker used the “reward tackle” choice to hyperlink a brand new e mail to their PayPal account.
There are two fields when including a brand new tackle and the attacker crammed one with an e mail and pasted the phishing message into the second.
PayPal mechanically sends a affirmation to the attacker’s tackle, which forwards it to a mailing record that relays it to all of the potential victims within the group.
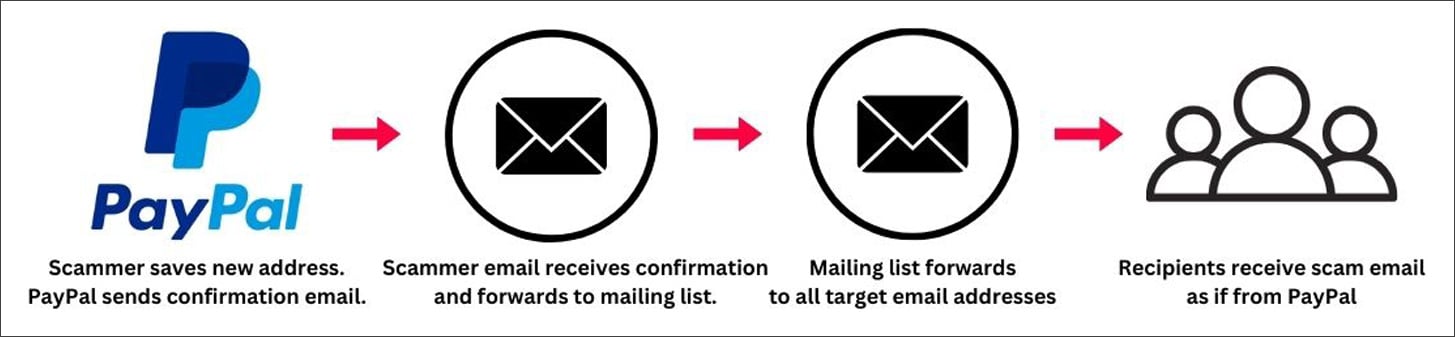 PayPal rip-off makes use of comparable trick
PayPal rip-off makes use of comparable trick
supply: BleepingComputer
BleepingComputer reached out to PayPal concerning the difficulty however by no means obtained a response.
Johnson additionally submitted a bug report back to Google and the corporate’s preliminary reply was that the method was working as meant.
Nonetheless, Google later reconsidered the problem, recognizing it as a threat to its customers, and is at present working to repair the OAuth weak spot.