Microsoft warns {that a} cyber-espionage group linked to Russia’s Federal Safety Service (FSB) is concentrating on diplomatic missions in Moscow utilizing native web service suppliers.
The hacking group tracked by Microsoft as Secret Blizzard (also referred to as Turla, Waterbug, and Venomous Bear) has been noticed exploiting its adversary-in-the-middle (AiTM) place on the web service supplier (ISP) degree to contaminate the methods of diplomatic missions with customized ApolloShadow malware.
To do that, they redirect targets to captive portals, tricking them into downloading and executing a malware payload disguised as a Kaspersky antivirus replace, which installs a trusted root certificates.
As soon as deployed, ApolloShadow helps trick compromised gadgets into recognizing malicious web sites as official, permitting risk actors to keep up long-term entry for intelligence gathering after infiltrating diplomatic methods.
“That is the primary time Microsoft can affirm Secret Blizzard’s functionality to conduct espionage on the ISP degree, which means diplomatic personnel utilizing native web suppliers and telecommunications in Russia are at excessive threat of being targets of Secret Blizzard’s AiTM place inside these providers,” Microsoft mentioned.
“This marketing campaign, which has been ongoing since a minimum of 2024, poses a excessive threat to overseas embassies, diplomatic entities, and different delicate organizations working in Moscow, notably to these entities who depend on native web suppliers.”
Whereas Microsoft first detected the assaults in February 2025, the corporate believes this cyber-espionage marketing campaign has been lively since a minimum of 2024.
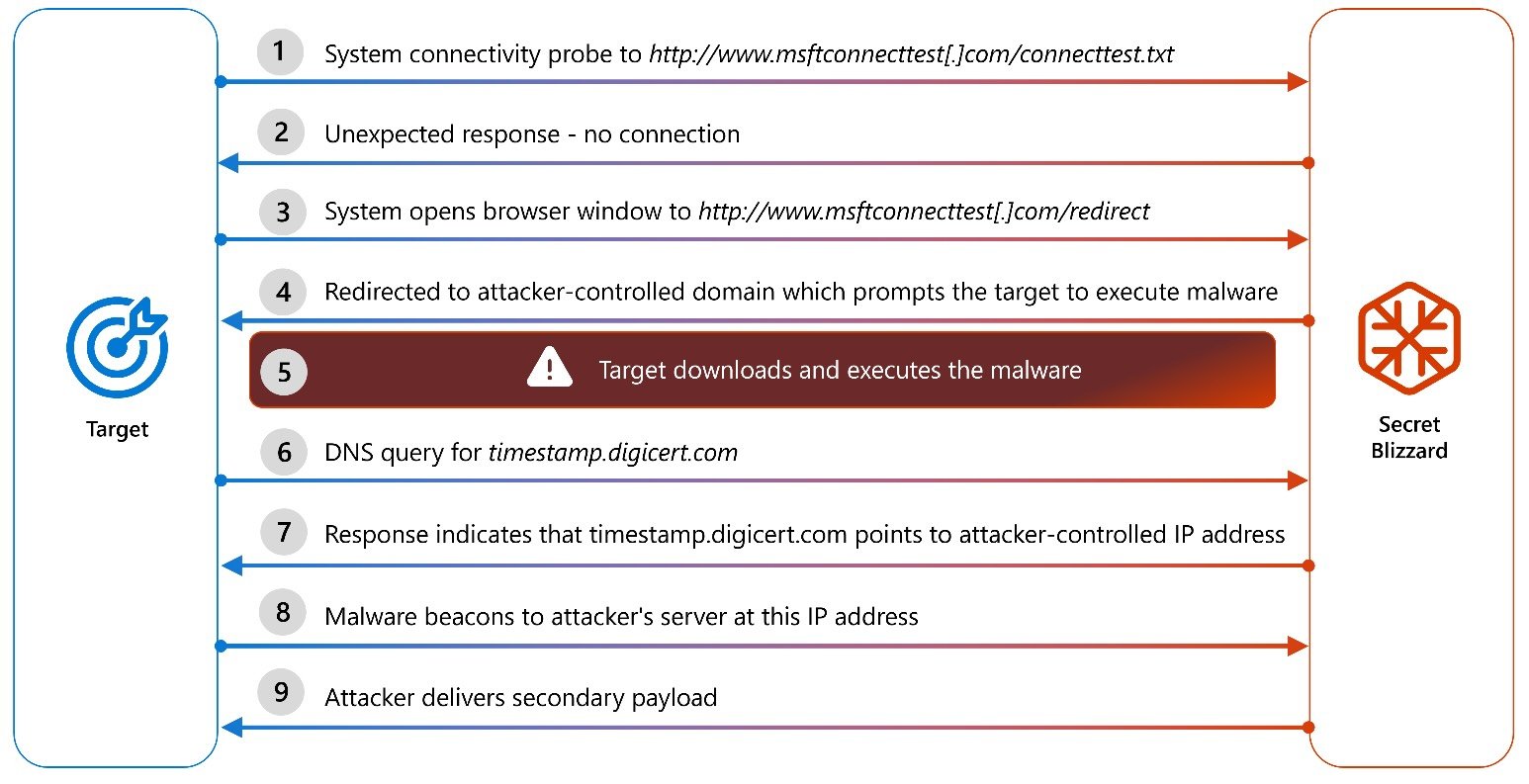 Secret Blizzard an infection chain (Microsoft)
Secret Blizzard an infection chain (Microsoft)
Secret Blizzard hackers are additionally profiting from Russia’s home interception methodstogether with the System for Operative Investigative Actions (SORM), to hold out their large-scale AiTM campaigns.
Unorthodox cyberspies targeted on high-profile targets
Turla has been orchestrating cyber-espionage and data theft campaigns concentrating on embassies, governments, and analysis amenities throughout over 100 nations since a minimum of 1996.
Two years in the past, CISA linked the group to Heart 16 of Russia’s Federal Safety Service (FSB) and a peer-to-peer (P2P) community of computer systems contaminated with Snake cyber-espionage malware that was later taken down in a joint motion involving 5 Eyes cybersecurity and intelligence businesses.
These Russian state-backed hackers are additionally the first suspects behind assaults concentrating on the U.S. Central Command, NASA, the Pentagona number of Japanese European Ministries of Overseas Affairsthe Finnish Overseas Ministryand EU governments and embassies.
This risk group is understood for its unconventional techniques, together with the management of malware by means of feedback on Britney Spears’ Instagram photographs and using backdoor trojans with their very own APIs.
Turla additionally utilized the hijacked infrastructure and malware of the Iranian APT OilRig in their very own campaigns to mislead and deceive defenders into attributing their assaults to Iranian state hackers.
Most lately, they’ve additionally been noticed hijacking the infrastructure of Pakistani risk actor Storm-0156 to focus on Ukrainian army gadgets related through Starlink.
Malware concentrating on password shops surged 3X as attackers executed stealthy Good Heist eventualities, infiltrating and exploiting essential methods.
Uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and tips on how to defend towards them.





