A Chinese language hacking group is deploying Warlock ransomware on Microsoft SharePoint servers susceptible to widespread assaults focusing on the just lately patched ToolShell zero-day exploit chain.
Tracked as Storm-2603, these China-based risk actors have been additionally beforehand linked by Microsoft researchers to Lockbit ransomware assaults.
“Microsoft tracks this risk actor in affiliation with makes an attempt to steal MachineKeys utilizing the on-premises SharePoint vulnerabilities,” the corporate stated in a Wednesday report. “Beginning on July 18, 2025, Microsoft has noticed Storm-2603 deploying ransomware utilizing these vulnerabilities.”
After breaching the victims’ networks, Storm-2603 operators use the Mimikatz hacking software to extract plaintext credentials from LSASS reminiscence.
They then transfer laterally with PsExec and the Impacket toolkit, executing instructions by way of Home windows Administration Instrumentation (WMI), and modifying Group Coverage Objects (GPOs) to ship Warlock ransomware throughout compromised programs.
“The group that Microsoft tracks as Storm-2603 is assessed with average confidence to be a China-based risk actor. Microsoft has not recognized hyperlinks between Storm-2603 and different recognized Chinese language risk actors,” the corporate added.
“Prospects ought to apply the on-premises SharePoint Server safety updates instantly and observe the detailed mitigation steerage in our weblog,” Microsoft warned.
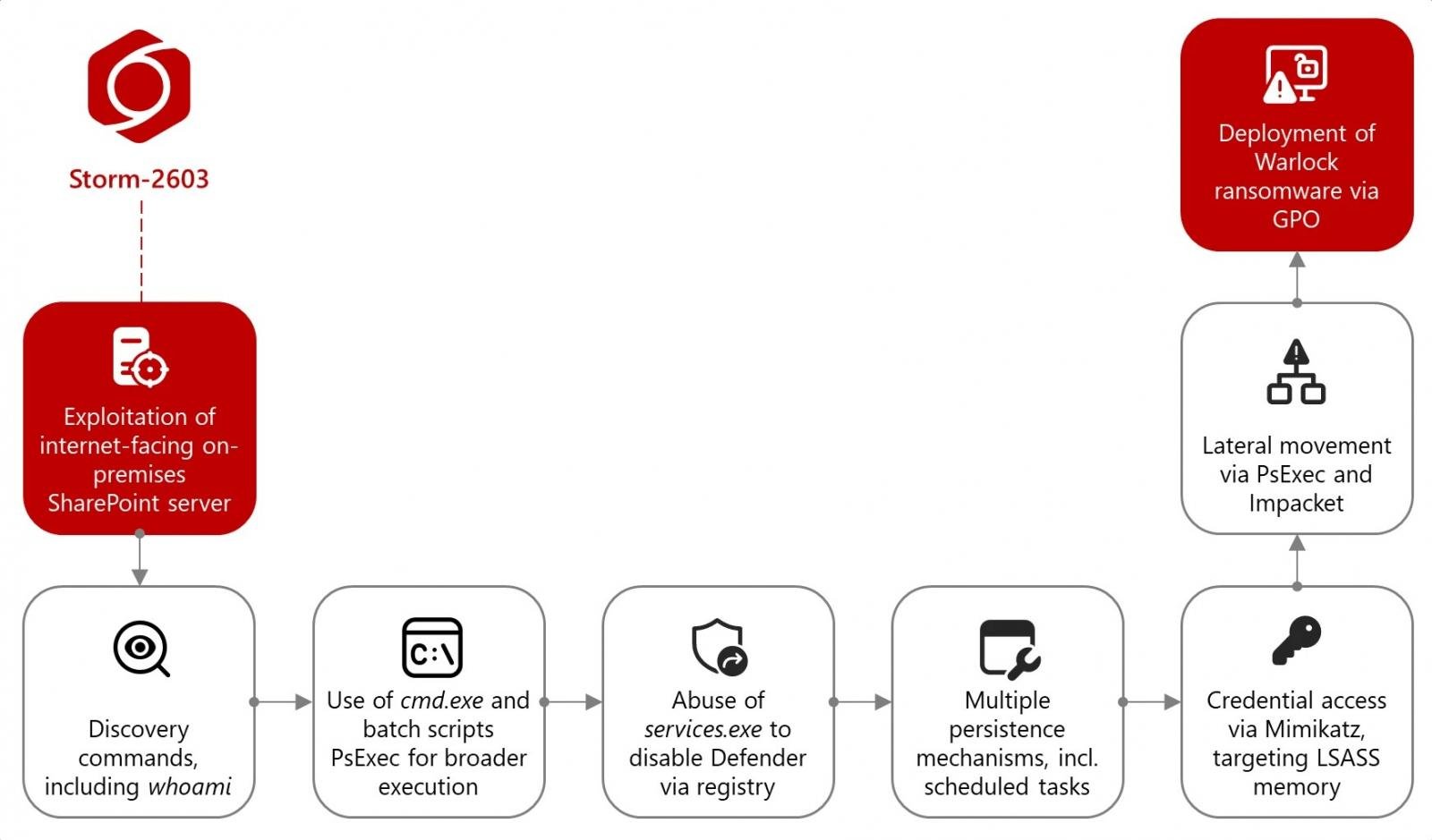 Storm-2603 ransomware assault movement (Microsoft)
Storm-2603 ransomware assault movement (Microsoft)
Microsoft Risk Intelligence researchers have additionally linked the Linen Hurricane and Violet Hurricane Chinese language state-backed hacking teams with these assaults on Tuesday, days after Dutch cybersecurity agency Eye Safety first detected zero-day assaults exploiting the CVE-2025-49706 and CVE-2025-49704 vulnerabilities.
Since then, Eye Safety CTO Piet Kerkhofs informed BleepingComputer that the variety of breached entities is far bigger, with “most of them already compromised for a while already.” In line with the cybersecurity firm’s statistics, the attackers have up to now contaminated no less than 400 servers with malware and breached 148 organizations worldwide.
Cisa Additionally added the CVE-2025-53770 distant code execution flawa part of the identical ToolShell exploit chain, to its catalog of vulnerabilities exploited within the wild, ordering US federal companies to safe their programs inside a day.
Nonetheless, earlier this week, the Division of Vitality confirmed that the Nationwide Nuclear Safety Administration’s networks have been breached within the ongoing Microsoft SharePoint assaults, though the company has but to seek out proof that delicate or categorised info was compromised within the incident.
In line with a Bloomberg reportthe attackers have additionally hacked into programs on the US Division of Schooling, the Rhode Island Basic Meeting, and Florida’s Division of Income, in addition to networks of nationwide governments in Europe and the Center East.
Include rising threats in actual time – earlier than they impression what you are promoting.
Find out how cloud detection and response (CDR) provides safety groups the sting they want on this sensible, no-nonsense information.





