The creators of StealC, a widely-used data stealer and malware downloader, have launched its second main model, bringing a number of stealth and information theft enhancements.
The newest model of StealC was really made obtainable to cybercriminals in March 2025, however Zscaler researchers who analyzed it simply revealed an in depth write-up.
Within the weeks that adopted its launch, a number of minor bug fixes and level releases added new options, with the most recent being model 2.2.4.
StealC is a light-weight info-stealer malware that gained traction on the darkish internet in early 2023, promoting entry for $200/month.
In 2024, it was noticed in large-scale malvertising campaigns and assaults locking methods into inescapable kiosk modes.
In late 2024, it was confirmed that StealC improvement remained very lively, with its builders including a bypassing mechanism for Chrome’s ‘App-Certain Encryption’ cookie-theft defenses, permitting the “regeneration” of expired cookies for hijacking Google accounts.
New in newest model
Model 2 (and later) was introduced in March 2025. In accordance with Zscaler’s evaluation, it brings the next main enhancements:
Payload supply enhancements with assist for EXE information, MSI packages, and PowerShell scripts, and configurable payload triggering.
RC4 encryption was added for code strings and command-and-control (C2) communications, with random parameters in C2 responses for higher evasion.
Structure and execution enhancements with new payloads compiled for 64-bit methods, resolving API features dynamically at runtime, and introducing a self-deletion routine.
New embedded builder that permits operators to generate new StealC builds utilizing templates and customized information theft guidelines.
Added Telegram bot assist for real-time alerts to operators.
Added functionality to screenshot the sufferer’s desktop with multi-monitor assist.
 StealC v2 new admin panel
StealC v2 new admin panel
Supply: Zscaler
Nonetheless, aside from the function additions, there have additionally been some notable removals, just like the anti-VM checks and DLL downloading/execution.
These would possibly point out an effort to make the malware leaner, however they could even be collateral harm from main code rework and may very well be re-introduced in higher type in future variations.
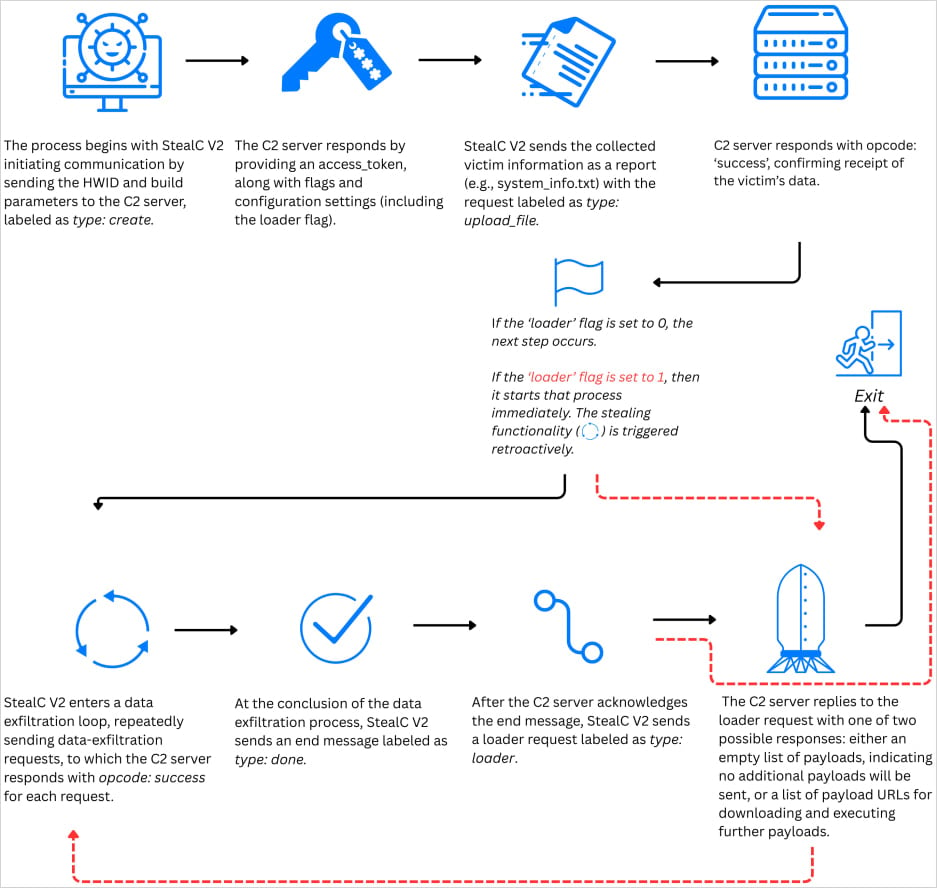 StealC’s C2 communication move
StealC’s C2 communication move
Supply: Zscaler
In the newest assaults seen by Zscaler, StealC was deployed by Amadey, a separate malware loader, although totally different operators might differentiate the supply strategies or assault chains.
To guard your information from info-stealer malware, keep away from storing delicate data in your browser for comfort, use multi-factor authentication to guard your accounts, and by no means obtain pirated or different software program from obscure sources.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and the right way to defend in opposition to them.






Looks like my earlier comment didn’t appear, but I just wanted to say—your blog is so inspiring! I’m still figuring things out as a beginner,and reading your posts makes me want to keep going with my own writing journey.