In the present day, Microsoft Risk Intelligence Heart is worked up to announce the discharge of RIFT, a device designed to help malware analysts automate the identification of attacker-written code inside Rust binaries. Identified for its effectivity, kind security, and strong reminiscence security, Rust has more and more turn out to be a device for creating malware, particularly amongst financially motivated teams and nation-state entities. This shift has launched new challenges for malware analysts because the distinctive traits of Rust binaries make static evaluation extra advanced.
One of many main challenges in reverse engineering malware developed with Rust lies in its layers of abstraction added by means of options resembling reminiscence security and concurrency dealing with, making it more difficult to determine the conduct and intent of the malware. In comparison with conventional languages, Rust binaries are sometimes bigger and extra advanced because of the incorporation of intensive library code. Consequently, reverse engineers should undertake the demanding process of distinguishing attacker-written code from customary library code, necessitating superior experience and specialised instruments.
To handle these urgent challenges, Microsoft Risk Intelligence Heart has developed RIFT. RIFT underscores the rising want for specialised instruments as cyber risk actors proceed to leverage Rust’s options to evade detection and complicate evaluation. The adoption of Rust by risk actors is a stark reminder of the ever-changing techniques employed within the cyber area, and the growing sophistication required to fight these threats successfully. On this weblog publish, we discover how risk actors are more and more adopting Rust for malware growth as a result of its versatility and the way RIFT can be utilized to fight this risk by enhancing the effectivity and accuracy of Rust-based malware evaluation.
Risk actors proceed adopting Rust
As Rust positive factors reputation as a quickly rising programming language, its use by malware authors is turning into extra noticeable. Over the previous 5 years, Microsoft Risk Intelligence Heart and the broader safety business have noticed financially motivated and state-supported teams more and more utilizing Rust for malware growth.
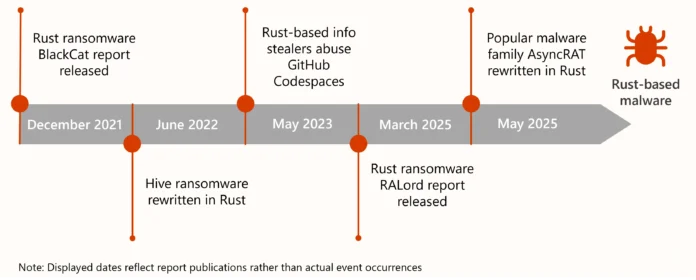
Determine 1. Timeline of Rust-based threats
In 2021, the group behind the infamous BlackCat ransomware was among the many first vital entities within the ransomware area to put in writing their malicious packages in Rust. Following the looks of the primary malware households written in Rust, reverse engineers indicated that such malware presents a singular problem for evaluation.
Subsequently, a number of different teams started growing or rewriting their instruments within the programming language. Nation-state risk actors have additionally selectively developed their malware in Rust.
Rust as a preferred language for malware growth
Rust is a flexible language identified for its efficiency, kind security, concurrency, and reminiscence security. Whereas these options profit authentic growth, additionally they complicate static evaluation of malicious information. The neighborhood has extensively addressed many of those challenges. One of many core points in analyzing Rust binaries is differentiating between library code and code written by malware authors.
For instance the importance of this drawback, Microsoft Risk Intelligence Heart performed a easy experiment. A small PE EXE file that downloads knowledge from a web site and saves it on disk as sample_data.txt is generated with Microsoft 365 Copilot. This system is first compiled in C++ after which in Rust. The C++ program is compiled utilizing Microsoft Visible C++ (MSVC) with Visible Studio 2022, in launch mode for the 64-bit structure and dynamically linked, utilizing default settings. The Rust binary is compiled utilizing compiler model rustc 1.89.0-nightly (16d2276fa 2025-05-16), additionally in launch mode and with default settings.
 Determine 2. Easy downloader program in C++ to the left and Rust to the correct
Determine 2. Easy downloader program in C++ to the left and Rust to the correct
Subsequent, each packages are loaded into IDA Professional, and a easy complexity evaluation is carried out by counting and evaluating the variety of disassembled and recognized capabilities. Moreover, capabilities are categorized as annotated or not annotated. An annotated operate is one that’s mechanically detected by IDA’s built-in signatures or algorithms. It needs to be famous that IDA has capabilities to boost library recognition, however these weren’t used for this experiment.
Whereas each packages implement comparable functionalities, the full variety of disassembled capabilities within the C++ program is decrease than 100, whereas the Rust packages pack virtually 10,000 capabilities. Moreover, the scale of the C++ program is decrease than 20 KB, whereas the Rust program is bigger than 3 MB.
Applications written in Rust are usually statically linked, embedding all dependencies immediately into the executable. Consequently, binaries are bigger with a excessive quantity of capabilities, requiring analysts to tell apart first between third-party library code and attacker-authored logic.
To handle this key drawback, Microsoft Risk Intelligence Heart is releasing an internally developed device: RIFT.
This open-source undertaking is designed to assist reverse engineers and analysts extra effectively determine attacker-authored logic inside Rust-based malware.
From supply code to binary
 Determine 3. Overview of Rust developer toolset
Determine 3. Overview of Rust developer toolset
Earlier than delving into the inside workings of RIFT, it’s important to have a elementary understanding of how Rust binaries are compiled. As illustrated within the diagram above, Rust builders usually have interaction with three main parts and two endpoints:
cargo – The bundle supervisor
rustc – The Rust compiler
rustup – The Rust replace supervisor
static.rust-lang.org – S3 bucket that hosts pre-compiled compilers and toolchains
crates.io – Rust neighborhood’s crate registry
As soon as a developer has conceptualized what they intend to develop, a typical workflow could proceed as follows:
Utilizing the cargo device, the developer initializes a brand new projected named “check”.
They choose to not use the newest Rust compiler however a particular model. They execute rustup set up 1.84.0-x86_64-pc-windows-msvc to put in the specified compiler model and configure the undertaking to make use of the put in compiler.
They decide that their undertaking ought to talk through HTTP and incorporate a third-party dependency. They run cargo add request to put in the newest model of the third-party library, request.
Following these steps will lead to a completely configured undertaking. Upon completion, the developer could run cargo construct to finalize the binary, compiling the undertaking.
Static artifacts and the place to seek out them
Reverse engineers are normally handed the ultimate growth product of the malware writer, oftentimes with out data such because the compiler used or third-party dependencies. Whereas it’s extremely possible that malware authors use the identical instruments as reverse engineers for growth, no insights into the precise atmosphere can be found.
Nonetheless, understanding the event toolchain can help in rapidly distinguishing library code from writer written logic. Luckily, varied indicators may be extracted that present insights.
Rust compiler model
Rust binaries usually embody metadata from the compiler that identifies the Rust model used to compile the binary. A config.toml file is offered alongside pre-compiled Rust compilers and toolchains. This configuration file comprises the commit hash and the corresponding Rust compiler model of the pre-compiled product. By extracting the commit hash from the ultimate binary output, it’s attainable to map the Git commit hash again to the suitable Rust compiler model by parsing all obtainable config.toml information from the official launch channels.
Rust crates
As talked about above, cargo is used so as to add dependencies to a undertaking. Subsequent to the Git commit hash, metadata extracted from Rust binaries additionally embody the statically linked dependencies and their variations.
 Determine 4. Extractable dependencies from strings
Determine 4. Extractable dependencies from strings
The above picture exhibits how filtering for sure strings can show which dependencies have been possible statically linked into RALord ransomware.
Introducing RIFT
RIFT is an open-source device consisting of a set of IDA Professional (supporting variations >=9.0) plugins and Python scripts that goal to help reverse engineers and different software program analysts in annotating library code in Rust malware. It primarily consists of three parts:
RIFT Static Analyzer: IDA Professional plugin to extract the Rust compiler commit hash and embedded dependencies from a binary.
RIFT Generator: A Python program to automate the method of Rust compiler identification, FLIRT signature era of used Rust compiler and dependencies, in addition to automation of binary diffing.
RIFT Diff Applier: IDA Professional plugin to devour binary diffing data generated by RIFT Generator.
Within the earlier part, we listed which indicators may be extracted from Rust binaries that give insights into which Rust compiler and dependencies have been used. RIFT Static Analyzer automates the extraction course of and shops the knowledge in a JSON file for additional processing. Moreover, the plugin additionally extracts the structure the binary was compiled for and the goal working system. Within the under picture, the goal working system is labeled as target_triple.
 Determine 5. Overview of RIFT Static Analyzer
Determine 5. Overview of RIFT Static Analyzer
RIFT Generator: Automating FLIRT signature era and auto diffing
Data gathered and saved by RIFT Static Analyzer can then be additional processed by RIFT Generator.
 Determine 6. RIFT Generator command line choices
Determine 6. RIFT Generator command line choices
The Python program automates the method of compilation, knowledge assortment, FLIRT signature era, and binary comparability.
It’s primarily a wrapper across the following instruments:
Cargo (Rust bundle supervisor) to handle the downloading and compiling of dependencies
Hexray’s FLAIR instruments, particularly sigmake.exe and pcf.exe, to generate FLIRT signatures
Hexray’s textual content interface model of IDA, idat.exe, to automate binary evaluation and disassembly
The open-source device Diaphora to facilitate binary diffing
 Determine 7. Phases of RIFT Generator
Determine 7. Phases of RIFT Generator
The above picture offers an summary of the phases RIFT Generator processes by means of. RIFT Generator reads the JSON file produced by RIFT Static Analyzer and downloads the corresponding Rust compiler, in addition to the dependencies.
It’s value noting that upon completion of part 1, each the code of the downloaded compiler and compiled crates are compressed as COFF information into RLIB information. RLIB is basically a Rust-specific archive format just like TAR. As soon as decompressed in part 2, the COFF information are extracted and additional processed.
FLIRT signatures and binary diffing
To offer data vital for annotating library code in Rust binaries precisely, RIFT makes use of two identified strategies for sample matching: FLIRT signatures and binary diffing.
FLIRT stands for Quick Library Identification and Recognition Expertise and allows IDA to determine customary library capabilities produced by its supported compilers. A attribute of this know-how is that library recognition could be very exact. Subsequently, capabilities which have a excessive similarity might not be flagged by FLIRT signatures as a result of their strict standards.
Moreover, RIFT automates the method of binary diffing the collected COFF information towards the goal binary by leveraging IDA’s command line utility (idat.exe) and the Diaphora plugin.
 Determine 8. Overview of experimental batch binary diffing course of
Determine 8. Overview of experimental batch binary diffing course of
On the whole, each approaches have their very own benefits and downsides, that are listed under.
FLIRT signatures approachBinary diffing approachHighly dependable annotation, low false optimistic rateHigher false optimistic fee, however much less strict and might fill gaps the place FLIRT signatures fail as a result of strictnessWith RIFT, in majority of circumstances, FLIRT signatures may be generated quicklyIn present state, batch binary diffing method would possibly take a number of hoursNot effectively relevant if dependencies and Rust compiler model usually are not availableApproach would possibly yield helpful outcomes even when Rust compiler model and dependencies weren’t obtainable
Consuming binary diffing data
If the binary diffing method is utilized, a second IDA plugin referred to as RIFT Diff Applier can be utilized to use the diffing outcomes. In distinction to FLIRT signatures, the RIFT Diff Applier affords analysts an interactive, semi-manual technique for figuring out library code. It operates in two modes:
Interactive mode
Auto rename mode
 Determine 9. GUI of RIFT Diff Applier
Determine 9. GUI of RIFT Diff Applier
By default, image names in COFF information are mangled. Consequently, if RIFT Generator generates the binary diffing data and shops it within the JSON format, the image names are additionally mangled. To handle this concern, enabling Title Demangling can help in trying to demangle these names. We’re constantly enhancing the device, and at present, rust-demangler is getting used for this objective.
For each modes, a minimal similarity ratio may be specified. Features will solely be displayed or renamed in the event that they meet or exceed the required similarity threshold. As soon as the consumer clicks “OK”, a brand new window will seem in IDA with the title RIFT. Customers can now proper click on on a operate title and show the highest three matching capabilities with the best similarity decided by means of binary diffing or use the CTRL+X shortcut.
 Determine 10. RIFT window in IDA displaying prime matching capabilities
Determine 10. RIFT window in IDA displaying prime matching capabilities
Making use of RIFT on RALord ransomware
Having launched the functionalities of RIFT, we are going to now study its sensible utility in analyzing RALord ransomware and the way RIFT’s FLIRT signature era can be utilized to immensely cut back time figuring out library capabilities in RALord.
First, RIFT Static Analyzer is used to dump the extractable dependencies, Git commit hash of the Rust compiler, goal structure, and goal working system. Subsequent, the knowledge is fed into RIFT Generator.
As soon as RIFT Generator has completed producing FLIRT signatures, they’ll both be loaded one after the other manually or by utilizing our script shared within the RIFT GitHub repository named “ida_apply_flirt_from_folder.py”.
The picture under compares elements of the primary operate earlier than and after utility of RIFT. After making use of the FLIRT signatures generated from the extracted dependencies and Rust compiler, nearly all of library and compiler code is recognized in the primary operate. Consequently, reverse engineers can focus solely on the risk actor code as an alternative of spending time hunting down the library code.
 Determine 11. Evaluating decompiled code earlier than and after making use of generated FLIRT signatures
Determine 11. Evaluating decompiled code earlier than and after making use of generated FLIRT signatures
Making use of RIFT on SPICA
In some use circumstances, FLIRT signature utility won’t be sufficient, for instance when conducting a deep dive. RIFT’s binary diffing method can present extra data to enhance library code recognition along with FLIRT signatures.
Having demonstrated the effectiveness of RIFT in making use of FLIRT signatures to streamline the evaluation of RALord ransomware, we now flip our focus to making use of the binary diffing method on SPICA, a backdoor written in Rust. This transition highlights situations the place FLIRT signatures alone may be inadequate, necessitating a deeper, complementary evaluation.
Much like earlier than, RIFT Static Analyzer is used first and the extracted data is fed into RIFT Generator. Nonetheless, this time, we apply FLIRT signature era and binary diffing.
 Determine 12. Enabling FLIRT signature era and binary diffing
Determine 12. Enabling FLIRT signature era and binary diffing
To make use of the binary diffing method, Diaphora should be used first to generate the corresponding SQLite file. It’s value noting that relying on the scale of the binary and extracted dependencies, the binary diffing process can take a number of hours.
As soon as carried out, RIFT Diff Applier can be utilized to load the binary diffing output file.
 Determine 13. Rift Diff Applier in use
Determine 13. Rift Diff Applier in use
A good thing about this method is that for sure capabilities the place FLIRT signatures didn’t correctly label the library operate as a result of its strictness, RIFT Diff Applier can present helpful and dependable data the place the similarity is excessive. Moreover, excited about detection engineering, the method may assist determine or filter out potential library capabilities, particularly when writing signatures on code segments.
Afterwords: Open sourcing RIFT
Rust’s robust efficiency, safety-focused design, cross-compilation help, and concurrency options have led to its elevated adoption by risk actors for growing advanced malware. This rising shift in direction of Rust represents a yet one more evolution within the risk panorama, enabling attackers to create malware that’s not extra immune to detection and evaluation.
For malware analysts, this pattern introduces a frightening set of challenges. Rust’s progressive options typically lead to binaries which are tougher to decompile and analyze, making reverse engineering a time-intensive course of. Analysts are ceaselessly left grappling with unfamiliar patterns and library-heavy outputs, which additional complicate their efforts to dissect malware and develop detection strategies.
To handle these challenges, we’re proud to announce the open sourcing of RIFT. Designed to assist speed up Rust malware evaluation by aiding reverse engineers to acknowledge library code in Rust malware by means of FLIRT signatures and binary diffing, RIFT additional reinforces international efforts to equip safety professionals with correct instruments to defend towards threats. By making RIFT freely obtainable to the cybersecurity neighborhood, we goal to foster collaboration and innovation in combating the rise of Rust-based malware. We wish to prolong a particular because of the writer of the Diaphora undertaking for his or her invaluable contribution to the reverse engineering neighborhood.
Microsoft’s ongoing analysis and growth efforts, together with the creation of instruments like RIFT, underscore our dedication to defending clients and securing the cyber panorama. By enhancing the effectivity and accuracy of malware evaluation, we goal to maintain tempo with evolving threats and make sure the security of customers worldwide. This analysis highlights the crucial want for superior safety measures to safeguard towards such more and more refined cyber threats.
References
Acknowledgments
Be taught extra
Meet the specialists behind Microsoft Risk Intelligence, Incident Response, and the Microsoft Safety Response Heart at our VIP Mixer at Black Hat 2025. Uncover how our end-to-end platform might help you strengthen resilience and elevate your safety posture.
For the newest safety analysis from the Microsoft Risk Intelligence neighborhood, try the Microsoft Risk Intelligence Weblog.
To get notified about new publications and to affix discussions on social media, comply with us on LinkedIn, X (previously Twitter), and Bluesky.
To listen to tales and insights from the Microsoft Risk Intelligence neighborhood in regards to the newest adjustments within the broader risk panorama, hearken to the Microsoft Risk Intelligence podcast.