Risk actors are abusing SourceForge to distribute pretend Microsoft add-ins that set up malware on victims’ computer systems to each mine and steal cryptocurrency.
SourceForge.web is a authentic software program internet hosting and distribution platform that additionally helps model management, bug monitoring, and devoted boards/wikis, making it highly regarded amongst open-source undertaking communities.
Though its open undertaking submission mannequin provides loads of margin for abuse, truly seeing malware distributed by it’s a uncommon prevalence.
The brand new marketing campaign noticed by Kaspersky has impacted over 4,604 techniques, most of that are in Russia.
Whereas the malicious undertaking is now not out there on SourceForge, Kaspersky says the undertaking had been listed by search engines like google and yahoo, bringing visitors from customers looking for “workplace add-ins” or related.
 SourceForge web page internet hosting the malware on search outcomes
SourceForge web page internet hosting the malware on search outcomes
Supply: Kaspersky
Faux Workplace add-ins
The “officepackage” undertaking presents itself as a set of Workplace Add-in growth instruments, with its description and recordsdata being a duplicate of the authentic Microsoft undertaking ‘Workplace-Addin-Scripts,’ out there on GitHub.
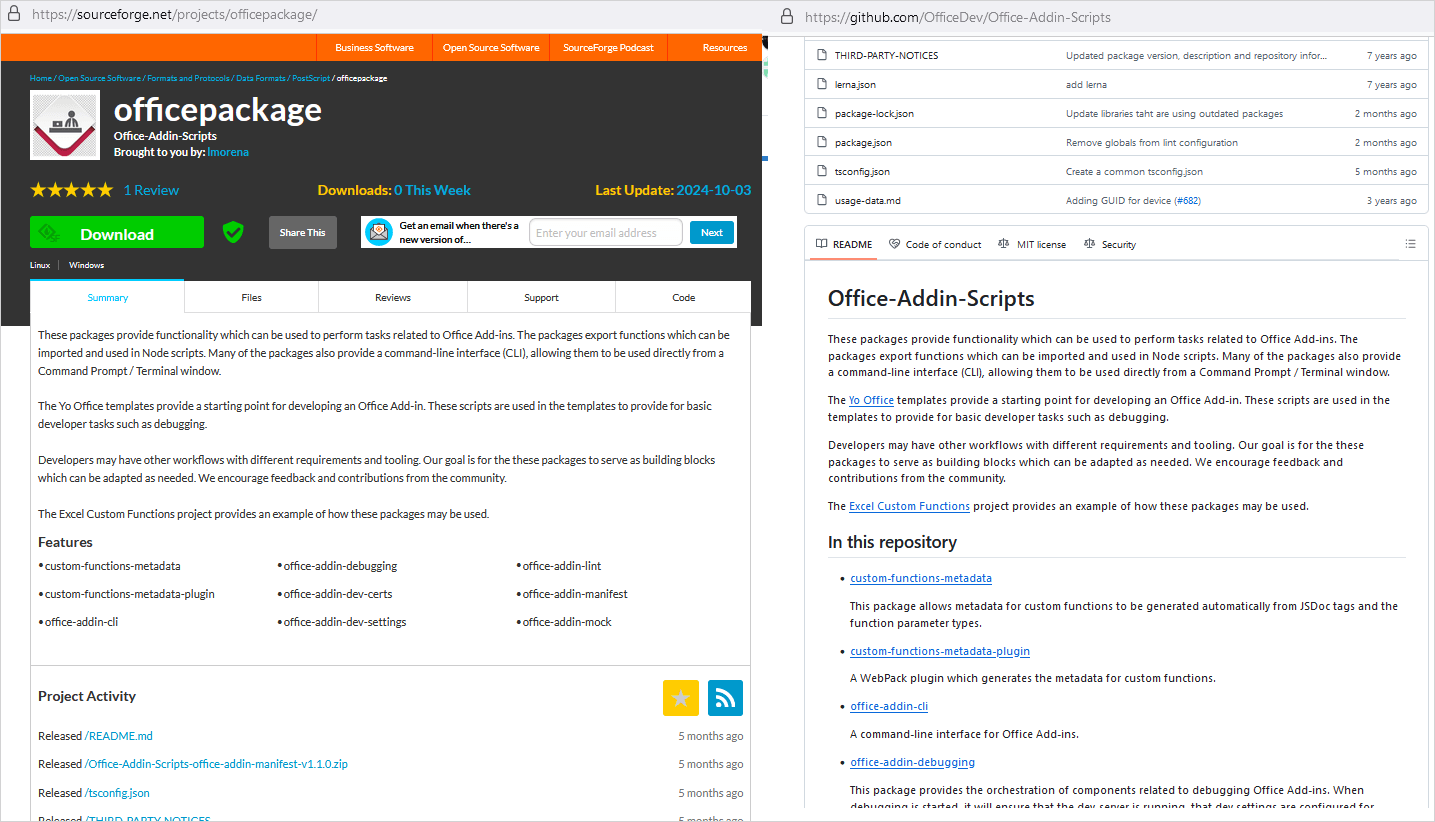 Malicious undertaking (left) and legit instrument (proper)
Malicious undertaking (left) and legit instrument (proper)
Supply: Kaspersky
Nonetheless, when customers seek for workplace add-ins on Google Search (and different engines), they get outcomes pointing to “officepackage.sourceforge.io,” powered by a separate webhosting function SourceForge provides to undertaking house owners.
That web page mimics a legit developer instrument web page, displaying the “Workplace Add-ins” and “Obtain” buttons. If any are clicked, the sufferer receives a ZIP containing a password-protected archive (installer.zip) and a textual content file with the password.
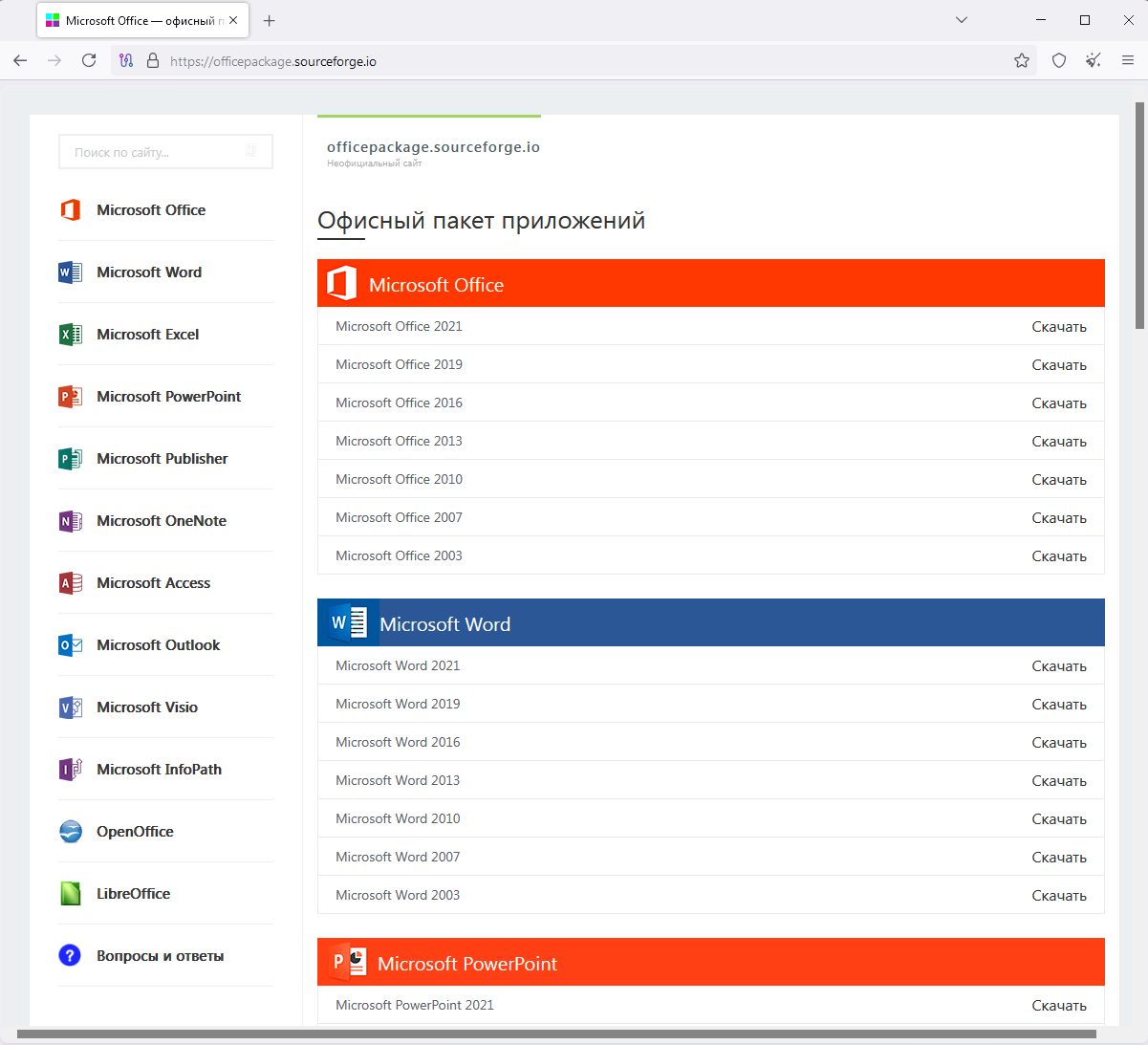 The malware-distributing website
The malware-distributing website
Supply: BleepingComputer
The archive incorporates an MSI file (installer.msi) inflated to 700MB in dimension to evade AV scans. Working it drops ‘UnRAR.exe’ and ‘51654.rar,’ and executes a Visible Fundamental script that fetches a batch script (confvk.bat) from GitHub.
The script performs checks to find out whether or not it runs on a simulated setting and what antivirus merchandise are energetic, after which downloads one other batch script (confvz.bat) and unpacks the RAR archive.
The confvz.bat script establishes persistence through Registry modifications and the addition of Home windows providers.
The RAR file incorporates an AutoIT interpreter (Enter.exe), the Netcat reverse shell instrument (ShellExperienceHost.exe), and two payloads (Icon.dll and Kape.dll).
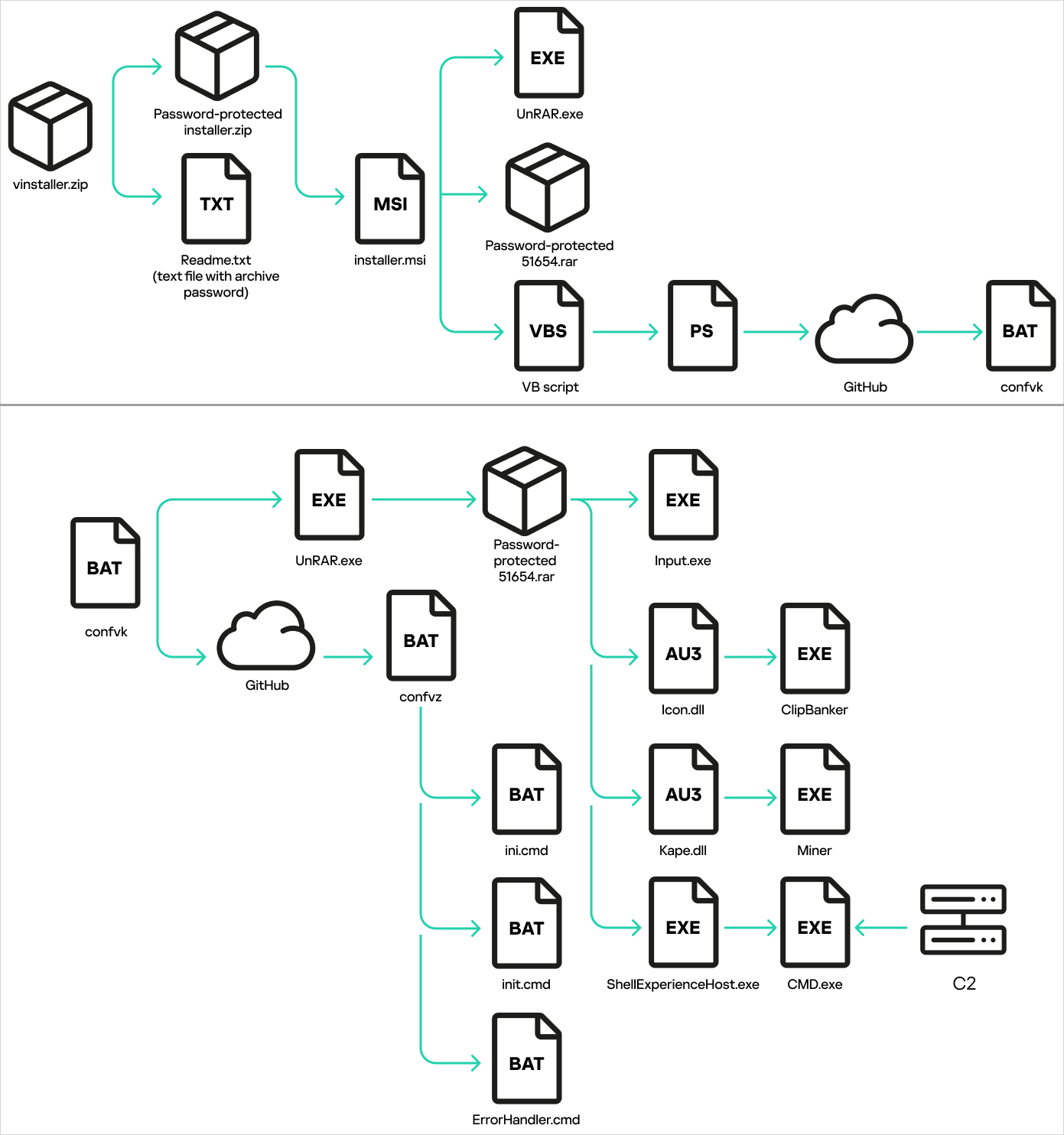 The entire an infection chain
The entire an infection chain
Supply: Kaspersky
The DLL recordsdata are a cryptocurrency miner and a clipper. The previous hijacks the machine’s computational energy to mine cryptocurrency for the attacker’s account, and the latter screens the clipboard for copied cryptocurrency addresses and replaces them with attacker-controlled ones.
The attacker additionally receives the contaminated system’s data through Telegram API calls and may use the identical channel to introduce further payloads to the compromised machine.
This marketing campaign is one other instance of menace actors exploiting any authentic platform to realize false legitimacy and bypass protections.
Customers are really useful to solely obtain software program from trusted publishers who they’ll confirm, want the official undertaking channels (on this case Girub), and scan all downloaded recordsdata with an up-to-date AV instrument earlier than execution.
Based mostly on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and the way to defend in opposition to them.





