A brand new marketing campaign using ClickFix assaults has been noticed focusing on each Home windows and Linux programs utilizing directions that make infections on both working system attainable.
ClickFix is a social engineering tactic the place pretend verification programs or software errors are used to trick web site guests into operating console instructions that set up malware.
These assaults have historically focused Home windows programs, prompting targets to execute PowerShell scripts from the Home windows Run command, leading to info-stealer malware infections and even ransomware.
Nonetheless, a 2024 marketing campaign utilizing bogus Google Meet errors additionally focused macOS customers.
ClickFix focusing on Linux customers
A newer marketing campaign noticed by Hunt.io researchers final week is among the many first to adapt this social engineering method for Linux programs.
The assault, which is attributed to the Pakistan-linked menace group APT36 (aka “Clear Tribe”), makes use of a web site that impersonates India’s Ministry of Defence with a hyperlink to an allegedly official press launch.
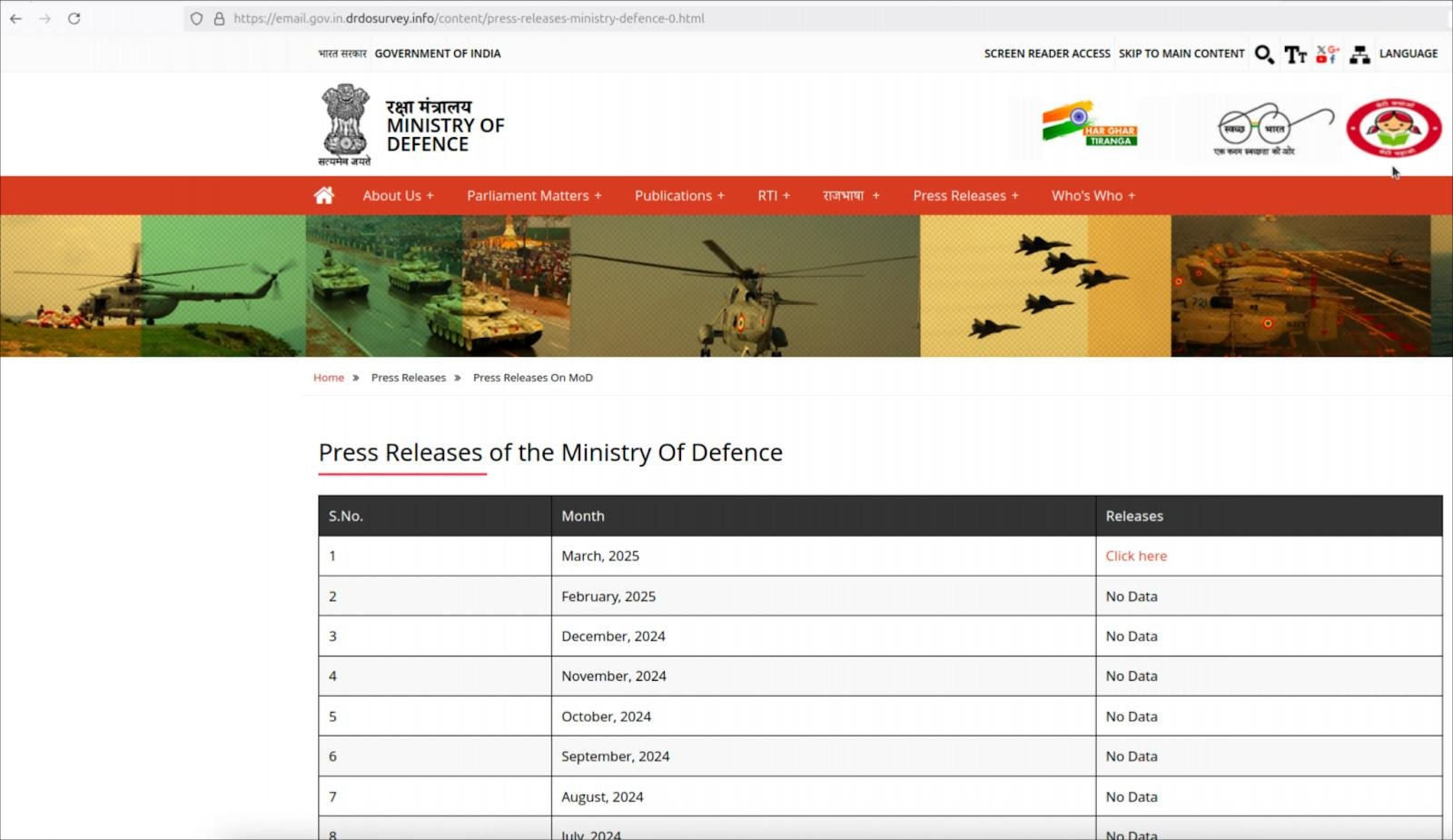 Malicious web site mimicking India’s Ministry of Defence
Malicious web site mimicking India’s Ministry of Defence
Supply: Hunt.io
When guests click on on this web site hyperlink, they’re profiled by the platform to find out their working system, after which redirected to the proper assault move.
On Home windows, victims are served a full-screen web page warning them of restricted content material utilization rights. Clicking on ‘Proceed’ triggers JavaScript that copies a malicious MSHTA command to the sufferer’s clipboard, who’s instructed to stick and execute it on the Home windows terminal.
This launches a .NET-based loader which connects to the attacker’s handle, whereas the consumer sees a decoy PDF file to make the whole lot seem official and as anticipated.
On Linux, victims are redirected to a CAPTCHA web page that copies a shell command to their clipboard when clicking the “I am not a robotic button.”
The sufferer is then guided to press ALT+F2 to open a Linux run dialog, paste the command into it, after which press Enter to execute it.
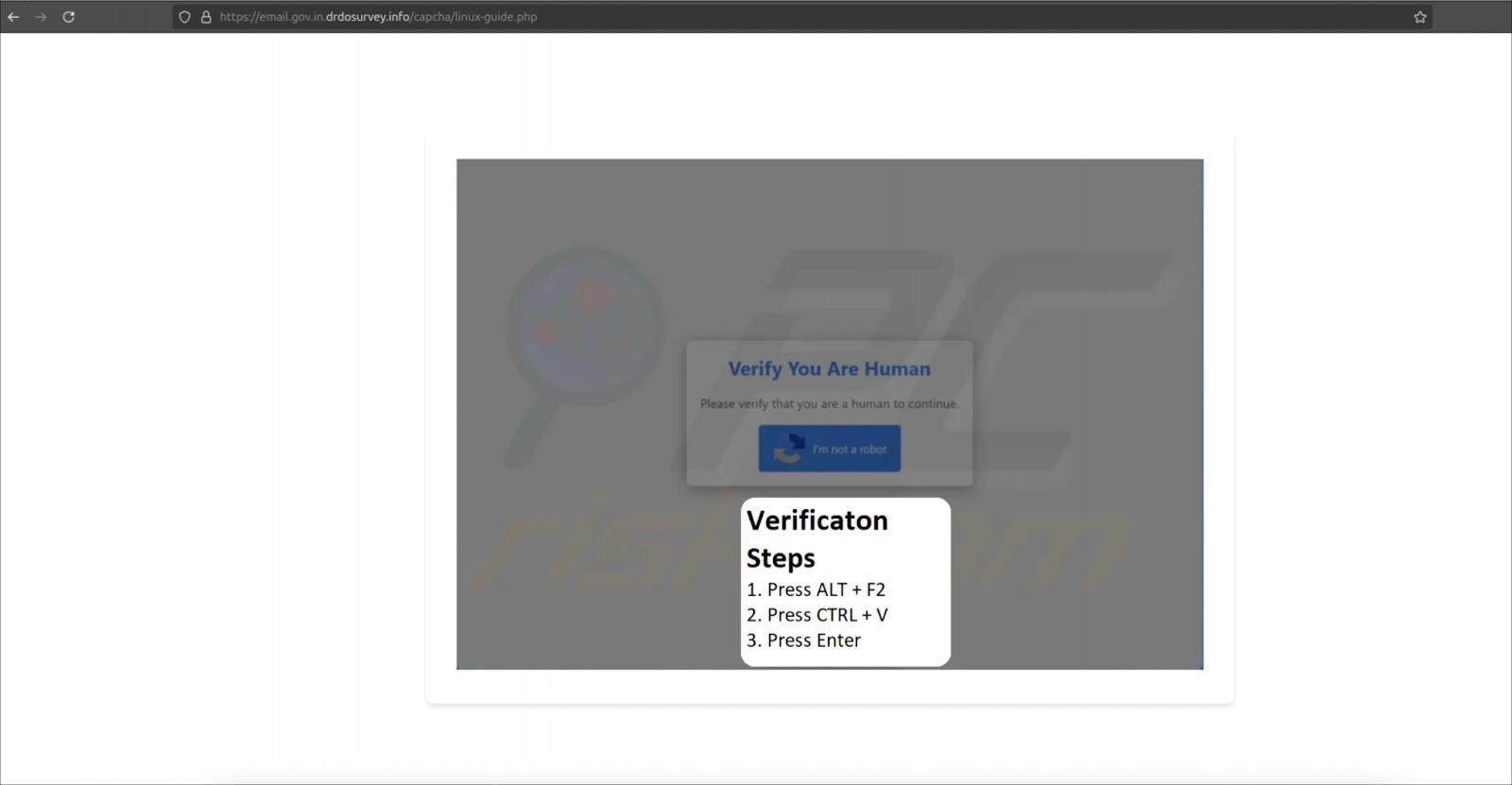 Directions for Linux customers
Directions for Linux customers
Supply: Hunt.io
The command drops the ‘mapeal.sh’ payload on the goal’s system, which, in keeping with Hunt.io, doesn’t carry out any malicious actions in its present model, restricted to fetching a JPEG picture from the attacker’s server.
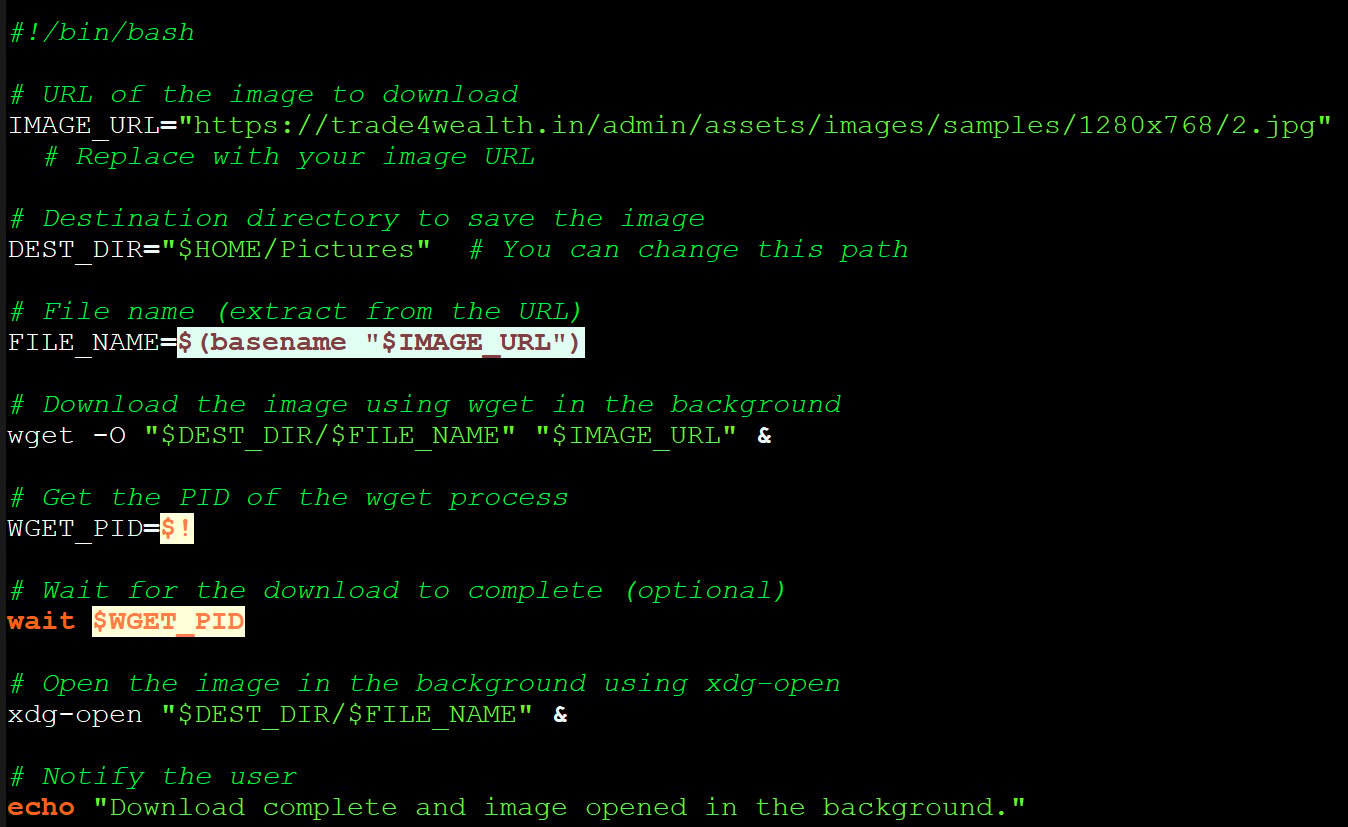 Linux ClickFix script
Linux ClickFix script
Supply: BleepingComputer
“The script downloads a JPEG picture from the identical trade4wealth(.)in listing and opens it within the background,” explains Hunt.io.
“No extra exercise, similar to persistence mechanisms, lateral motion, or outbound communication, was noticed throughout execution.”
Nonetheless, it’s attainable that APT36 is at present experimenting to find out the effectiveness of the Linux an infection chain, as they might simply have to swap out the picture for a shell script to put in malware or carry out different malicious exercise.
The variation of ClickFix to hold out assaults on Linux is one other testomony to its effectiveness, because the assault kind has now been used in opposition to all three main desktop OS platforms.
As a basic coverage, customers shouldn’t copy and paste any instructions into Run dialogs with out realizing precisely what the command does. Doing so solely will increase the danger of a malware an infection and theft of delicate information.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK strategies behind 93% of assaults and how one can defend in opposition to them.





