Phishing stays certainly one of cybersecurity’s most enduring threats, not as a result of defenders aren’t evolving, however as a result of attackers are adapting even sooner.
At the moment’s only campaigns aren’t simply constructed on spoofed emails or shady domains. They exploit one thing much more insidious: belief within the instruments and companies we use each day, resulting in zero-hour phishing.
The Rise of ChainLink Phishing
Conventional phishing relied on simply identifiable pink flags reminiscent of suspicious senders and questionable URLs. However trendy phishing has matured.
Attackers now deploy chained sequences, funneling a sufferer from electronic mail via trusted infrastructure earlier than harvesting credentials.
An worker may obtain a hyperlink from what seems to be Google Drive or Dropbox. At first look, there’s nothing uncommon. However after the preliminary click on, the consumer is quietly routed via a collection of prompts, every trying credible on respected websites, till they unknowingly hand over business-essential credentials to an attacker.
This system, which we name Chainlink phishingdepends on leveraging the reputable platforms and respected domains that enterprise instruments enable and that IT safety groups are oblivious to.
Hold Conscious stops phishing assaults in real-time the place they begin: contained in the browser.
By analyzing consumer habits, type submissions, and web site context, not simply URLs, Hold Conscious shuts down threats earlier than credentials ever depart the web page. Equip your safety staff with exact visibility, coverage enforcement, and speedy risk response all from throughout the present internet browsers throughout the group.
Why These Assaults Are So Efficient
The browser has grow to be the middle of the information employee’s universe. From code opinions to HR duties, practically each motion begins and ends in a browser tab.
This centralization offers attackers a singular floor to use, but it has been vastly underprotected.
Even essentially the most security-aware staff will be deceived when a hyperlink seems to return from a recognized area and follows the anticipated habits. The consumer typically believes they’re participating in regular exercise till it’s too late.
By utilizing reputable hyperlinks, passing electronic mail authentication checks, and even inserting CAPTCHAs alongside the best way, attackers sidestep conventional defenses and allow zero-hour phishing to succeed undetected.
CAPTCHAs and verification steps at the moment are so frequent in on a regular basis searching that attackers exploit them as social engineering ways, not solely in phishing campaigns, but in addition in different browser-based threats like ClickFix.
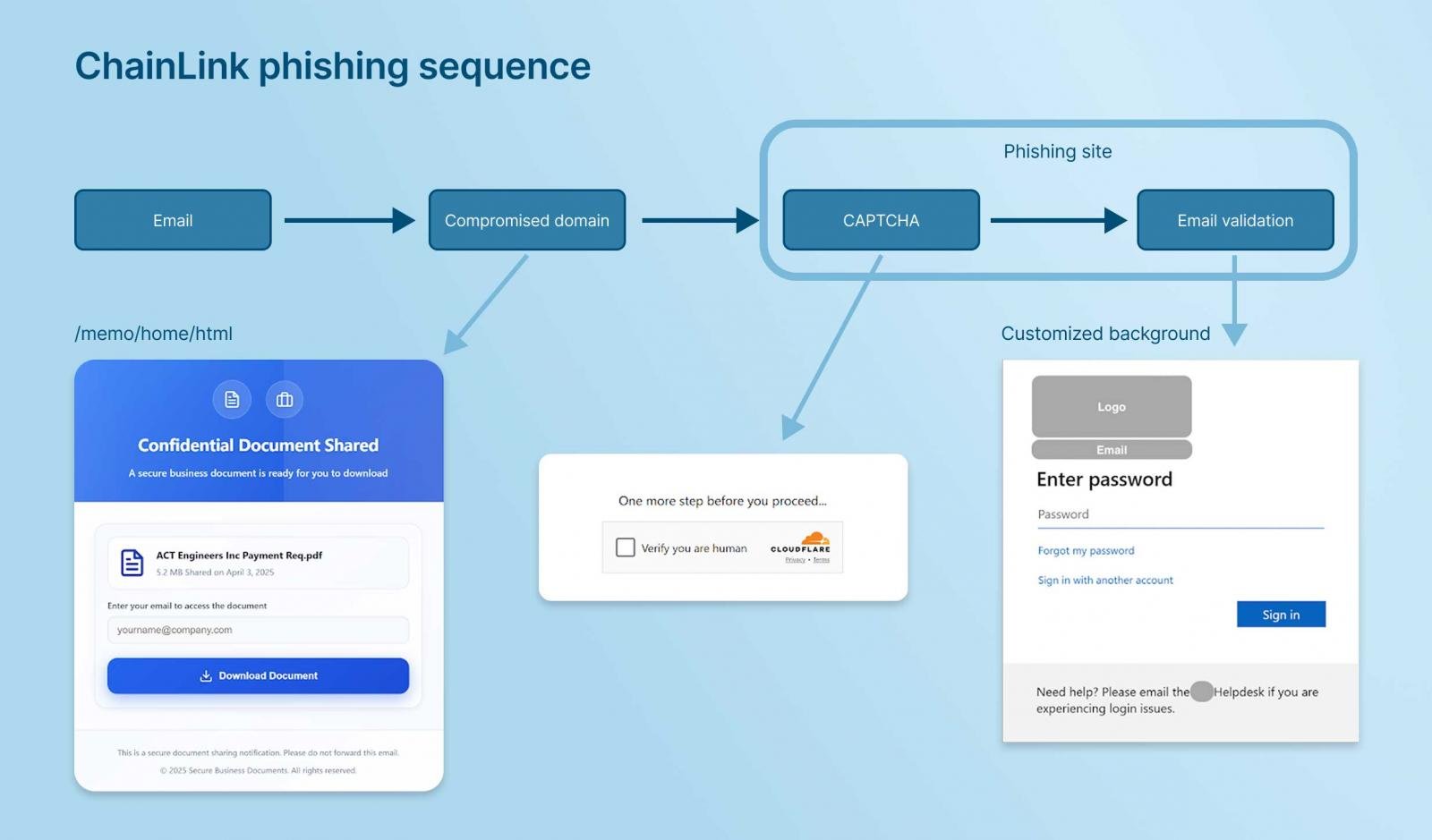 Instance of ChainLink Phishing Leveraging Compromised Area, CAPTCHA, and Electronic mail Validation
Instance of ChainLink Phishing Leveraging Compromised Area, CAPTCHA, and Electronic mail Validation
“Recognized Good” Is No Longer Secure
This shift highlights a painful fact: “recognized good” is not a dependable safety sign. Actually, it’s grow to be the proper disguise for dangerous actors.
To really tackle threats like ChainLink Phishing, we have to transfer past static blocklists and domain-based filtering. The way forward for phishing safety lies in real-time evaluation of internet pages and customers’ interactions with them.
 Among the reputable platforms utilized in ChainLink Phishing assaults
Among the reputable platforms utilized in ChainLink Phishing assaults
When the Safety Stack Can’t See the Risk
A phishing hyperlink that originates from a trusted service will typically sail previous electronic mail and community filters. Visitors to the phishing web site is allowed unimpeded as a result of the area isn’t on an intel feed and its repute is undamaged. And since no malware is deployed, simply credential harvesting, endpoint instruments don’t have anything to detect.
Regardless of having layered defenses like:
Safe electronic mail gateways (SEGs)
DNS filtering
Safe internet gateways (SWGs)
EDR/AV
Native browser protections
… Most organizations stay susceptible. Why? As a result of these instruments are designed to dam recognized malicious internet habits and endpoint options are oblivious to credential-harvesting internet varieties. The refined misuse of reputable domains, mixed with further evasive methods, results in customers falling sufferer to zero-hour phishing.
Defend The place Phishing Actually Strikes
These sequenced assaults exploit trusted pathways, main customers to phishing websites that simply bypass conventional defenses. By the point credentials are entered, it’s typically too late—and most organizations by no means noticed it coming. To successfully mitigate these threats, safety must shift to the place the chance materializes: the browser. It’s time to cease phishing on the root supply, not simply on the perimeter.
To know how these chained phishing sequences work, and detect and cease them earlier than harm is finished, watch Hold Conscious’s newest on-demand webinar:
ChainLink Phishing: The Chained Sequences of Trendy Phishing
Sponsored and written by Hold Conscious.




