Lately, human-operated cyberattacks have undergone a dramatic transformation. These assaults, as soon as characterised by sporadic and opportunistic assaults, have advanced into extremely subtle, focused campaigns geared toward inflicting most harm to organizations, with the common value of a ransomware assault reaching $9.36 million in 2024.1 A key catalyst to this evolution is the rise of ransomware as a major instrument for monetary extortion—an strategy that hinges on crippling a corporation’s operations by encrypting crucial information and demanding a ransom for its launch. Microsoft Defender for Endpoint disrupts ransomware assaults in a mean of three minutes, solely kicking in when greater than 99.99% assured within the presence of a cyberattack.
The evolution of ransomware assaults
Fashionable ransomware campaigns are meticulously deliberate. Cyberattackers perceive that their possibilities of securing a ransom enhance considerably if they will inflict widespread harm throughout a sufferer’s surroundings. The rationale is straightforward: paying the ransom turns into probably the most viable choice when the choice—restoring the surroundings and recovering information—is technically unfeasible, time-consuming, and expensive.
This degree of injury occurs in minutes and even seconds, the place unhealthy actors embed themselves inside a corporation’s surroundings, laying the groundwork for a coordinated cyberattack that may encrypt dozens, a whole lot, and even hundreds of units inside minutes. To execute such a marketing campaign, risk actors should overcome a number of challenges resembling evading safety, mapping the community, sustaining their code execution capability, and preserving persistency within the surroundings, constructing their technique to securing two main conditions essential to execute ransomware on a number of units concurrently:
Excessive-privilege accounts: Whether or not cyberattackers select to drop recordsdata and encrypt the units domestically or carry out distant operations over the community, they need to get hold of the flexibility to authenticate to a tool. In an on-premises surroundings, cyberattackers often goal area admin accounts or different high-privilege accounts, as these can authenticate to probably the most crucial assets within the surroundings.
Entry to central community property: To execute the ransomware assault as quick and as extensive as doable, risk actors intention to realize entry to a central asset within the community that’s uncovered to many endpoints. Thus, they will leverage the possession of high-privilege accounts and hook up with all units seen of their line of sight.
The position of area controllers in ransomware campaigns
Area controllers are the spine of any on-premises surroundings, managing identification and entry by way of Lively Listing (AD). They play a pivotal position in enabling cyberattackers to realize their targets by fulfilling two crucial necessities:
1. Compromising extremely privileged accounts
Area controllers home the AD database, which accommodates delicate details about all person accounts, together with extremely privileged accounts like area admins. By compromising a website controller, risk actors can:
Extract password hashes: Dumping the NTDS.dit file permits cyberattackers to acquire password hashes for each person account.
Create and elevate privileged accounts: Cyberattackers can generate new accounts or manipulate current ones, assigning them elevated permissions, guaranteeing continued management over the surroundings.
With these capabilities, cyberattackers can authenticate as extremely privileged customers, facilitating lateral motion throughout the community. This degree of entry allows them to deploy ransomware on a scale, maximizing the impression of their assault.
2. Exploiting centralized community entry
Area controllers deal with essential duties like authenticating customers and units, managing person accounts and insurance policies, and holding the AD database constant throughout the community. Due to these vital roles, many units have to work together with area controllers repeatedly to make sure safety, environment friendly useful resource administration, and operational continuity. That’s why area controllers should be central within the community and accessible to many endpoints, making them a primary goal for cyberattackers seeking to trigger most harm with ransomware assaults.
Given these elements, it’s no shock that area controllers are ceaselessly on the middle of ransomware operations. Cyberattackers persistently goal them to achieve privileged entry, transfer laterally, and quickly deploy ransomware throughout an surroundings. We’ve seen in additional than 78% of human-operated cyberattacks, risk actors efficiently breach a website controller. Moreover, in additional than 35% of circumstances, the first spreader system—the system liable for distributing ransomware at scale—is a website controller, highlighting its essential position in enabling widespread encryption and operational disruption.
Case research: Ransomware assault utilizing a compromised area controller
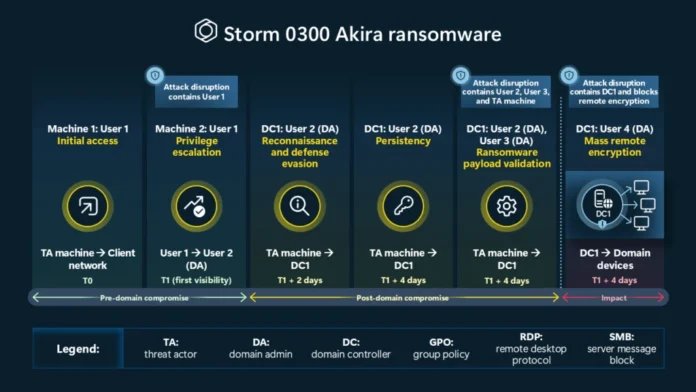
In a single notable case, a small-medium producer fell sufferer to a well known, extremely expert risk actor, generally recognized as Storm-0300, trying to execute a widespread ransomware assault:
Pre domain-compromise exercise
After gaining preliminary entry, presumably by way of leveraging the client’s VPN infrastructure, and previous to acquiring area admin privileges, the cyberattackers initiated a sequence of actions targeted on mapping potential property and escalating privileges. A large, distant execution of secrets and techniques dump is detected on Microsoft Defender for Endpoint-onboarded units and Consumer 1 (area person) is contained by assault disruption.
Publish domain-compromise exercise
As soon as securing area admin (Consumer 2) credentials, doubtlessly by way of leveraging the sufferer’s non-onboarded property, the attacker instantly makes an attempt to connect with the sufferer’s area controller (DC1) utilizing Distant Desktop Protocol (RDP) from the cyberattacker’s managed system. When having access to DC1, the cyberattacker leverages the system to carry out the next set of actions:
Reconnaissance—The cyberattacker leverages the area controller’s extensive community visibility and excessive privileges to map the community utilizing totally different instruments, specializing in servers and community shares.
Protection evasion—Leveraging the area controller’s native group coverage performance, the cyberattacker makes an attempt to tamper with the sufferer’s antivirus by modifying security-related group coverage settings.
Persistence—The cyberattacker leverages the direct entry to Lively Listing, creating new area customers (Consumer 3 and Consumer 4) and including them to the area admin group, thus establishing a set of extremely privileged customers that will afterward be used to execute the ransomware assault.
Encryption over the community
As soon as the cyberattacker takes management over a set of extremely privileged customers, this supplies them entry to any domain-joined useful resource, together with complete community entry and visibility. It’ll additionally enable them to arrange instruments for the encryption part of the cyberattack.
Assuming they’re capable of validate a website controller’s effectiveness, they start by operating the payload domestically on the area controller. Assault disruption detects the risk actor’s try and run the payload and accommodates Consumer 2, Consumer 3, and the cyberattacker-controlled system used to RDP to the area controller.
After efficiently containing Customers 2 and three, the cyberattacker proceeded to log in to the area controller utilizing Consumer 4, who had not but been utilized. After logging into the system, the cyberattacker tried to encrypt quite a few units over the community from the area controller, leveraging the entry offered by Consumer 4.
Assault disruption detects the initiation of encryption over the community and mechanically granularly accommodates system DC1 and Consumer 4, blocking the tried distant encryption on all Microsoft Defender for Endpoint-onboarded and focused units.
Defending your area controllers
Given the central position of area controllers in ransomware assaults, defending them is crucial to stopping large-scale harm. Nonetheless, securing area controllers is especially difficult on account of their basic position in community operations. Not like different endpoints, area controllers should stay extremely accessible to authenticate customers, implement insurance policies, and handle assets throughout the surroundings. This degree of accessibility makes it tough to use conventional safety measures with out disrupting enterprise continuity. Therefore, safety groups consistently face the advanced problem of placing the fitting steadiness between safety and operational performance.
To handle this problem, Defender for Endpoint launched comprise excessive worth property (HVA), an growth of our comprise system functionality designed to mechanically comprise HVAs like area controllers in a granular method. This characteristic builds on Defender for Endpoint’s functionality to categorise system roles and criticality ranges to ship a customized, role-based containment coverage, that means that if a delicate system, such a website controller, is compromised, it’s instantly contained in lower than three minutes, stopping the cyberattacker from transferring laterally and deploying ransomware, whereas on the similar time sustaining the operational performance of the system. The power of the area controller to tell apart between malicious and benign habits helps maintain important authentication and listing companies up and operating. This strategy supplies fast, automated cyberattack containment with out sacrificing enterprise continuity, permitting organizations to remain resilient in opposition to subtle human-operated cyberthreats.
Now your group’s area controllers can leverage computerized assault disruption as an additional line of protection in opposition to malicious actors attempting to overhaul excessive worth property and exert pricey ransomware assaults.
Be taught extra
Discover these assets to remain up to date on the newest computerized assault disruption capabilities:
To be taught extra about Microsoft Safety options, go to our web site. Bookmark the Safety weblog to maintain up with our knowledgeable protection on safety issues. Additionally, comply with us on LinkedIn (Microsoft Safety) and X (@MSFTSecurity) for the newest information and updates on cybersecurity.
1Common value per information breach in the USA 2006-2024Ani petrosyan. October 10, 2024.