Enterprise Safety
Ransomware
Your organization’s means to deal with the ransomware menace head-on can finally be a aggressive benefit
31 Mar 2025
•
,
3 min. learn

“Everyone has a plan till they get punched within the mouth.”
Mike Tyson’s punchy (pun meant) adage rings all too true for organizations reeling from a ransomware assault. In recent times, ransomware has confirmed able to bringing even a thriving enterprise to its knees in a matter of hours, and it’s protected to say that it’ll proceed to sucker-punch organizations of all stripes, testing their cyber-mettle and contingency plans in methods few different threats can match.
There’s no scarcity of knowledge and precise incidents to bear this out. In keeping with Verizon’s 2024 Information Breach Investigations Reportone-third of all information breaches contain ransomware or one other extortion approach. “Ransomware was a high menace throughout 92% of industries,” reads the report.
If this sounds disconcerting, it’s as a result of it’s. The stakes are additionally excessive as a result of ransomware can also come on the again of a provide chain assault – as was the case with the Kaseya incident in 2021 that exploited a vulnerability within the firm’s IT administration platform to vastly amplify the attain of ransomware throughout an untold variety of organizations worldwide.
Bruised and battered
When the information of a ransomware assault breaks, headlines typically concentrate on the dramatic ransom calls for and the moral and authorized conundrums over fee. What they typically fail to seize, nevertheless, is the organizational and human trauma suffered by the victims, doubly so when the incident is compounded by information exfiltration and threats to make the stolen information public.
When techniques go darkish, companies don’t merely pause – they hemorrhage cash whereas watching new alternatives slip away and model status endure. The injuries deepen exponentially as frantic restoration efforts stretch from hours into days, weeks and probably even months. The brutally easy premise of ransomware – encrypt important enterprise information and demand fee for its launch – truly belies a fancy cascade of operational, monetary and reputational harm that unfolds within the wake of the assault.
Once more, there’s ample information to indicate {that a} profitable ransomware incident prices victims dearly. IBM’s Value of a Information Breach Report 2024for instance, places the typical value of restoration from such an assault at near US$5 million.
Scarab ransomware additionally goals to hinder restoration efforts
Throwing a lifeline
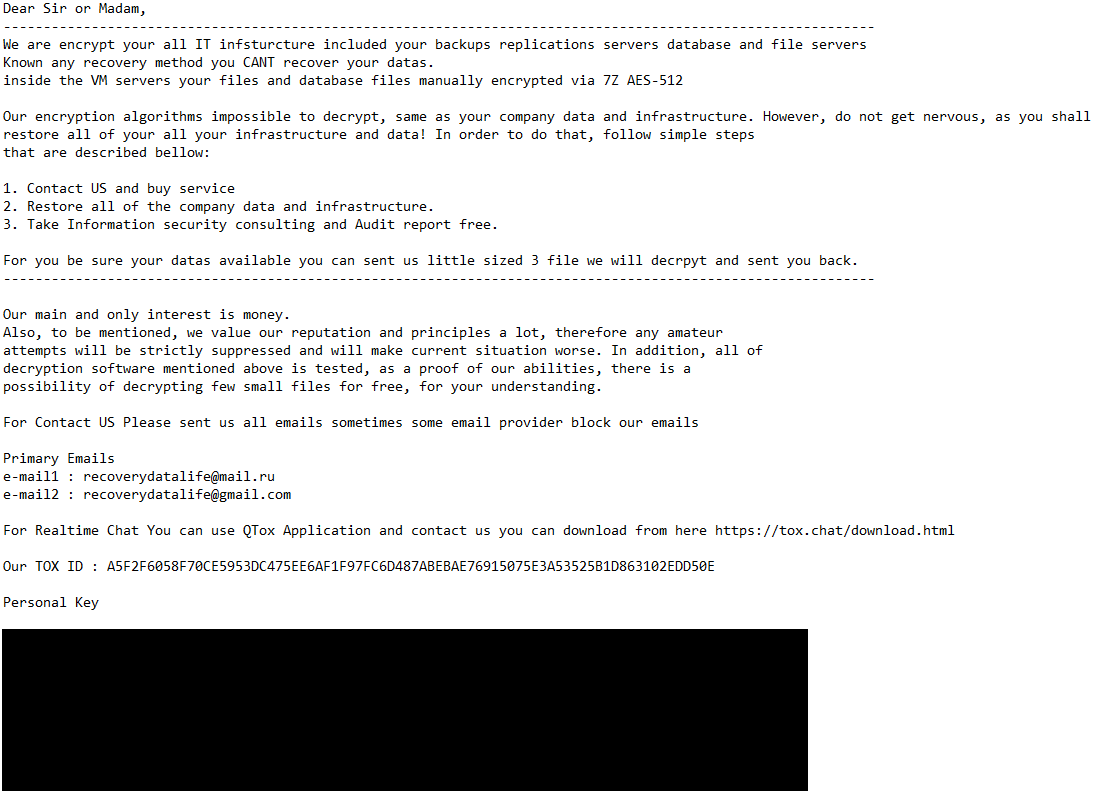
Organizations hit by ransomware sometimes depend on three escape routes: restoring from backups, receiving a decryption device from safety researchers (similar to these concerned with the No Extra Ransom initiative, which incorporates ESET as a member) or paying the ransom in return for a decryptor. However what if none of those choices seems to be workable?
First, attackers typically tighten the screw on victims by focusing on additionally their backup techniques, corrupting or encrypting them earlier than deploying ransomware on manufacturing environments. Second, decryption instruments from researchers are higher considered a last-resort choice because it typically can not match the urgency of enterprise restoration wants.
What about chucking up the sponge and paying the ransom? Leaving apart the potential authorized and regulatory pitfalls, fee ensures precisely nothing whereas typically simply including insult to damage. Colonial Pipeline discovered this the onerous means when the decryption instruments offered to it in alternate for a ransom fee of US$4.4 million had been so shoddy that restoring techniques from backups turned out to be the one viable choice anyway. (Word: the U.S. Division of Justice later recovered a lot of the ransom.)
ESET Ransomware Remediation brings a brand new strategy to this conundrum, successfully combining prevention and remediation into one. It creates focused file backups which might be out of attain for dangerous actors throughout a course of that kicks in when the danger is straight forward; i.e., as soon as a potential ransomware try is detected. Since attackers additionally typically take purpose at information backups, this strategy addresses the danger of unknowingly counting on compromised backups.
Bracing for impression
Ransomware is a full-blown disruptor able to unraveling enterprise operations thread by thread and with alarming velocity, however organizations with tried-and-true prevention and restoration capabilities won’t solely survive within the face of ransomware and different cyberthreats – their means to sidestep such blows could change into their final aggressive benefit.
Within the ever-shifting digital panorama, change is the one fixed, and resilience hinges on anticipating the surprising. Plan for the unknown like your online business is dependent upon it – as a result of it does.




I love how you write—it’s like having a conversation with a good friend. Can’t wait to read more!This post pulled me in from the very first sentence. You have such a unique voice!Seriously, every time I think I’ll just skim through, I end up reading every word. Keep it up!Your posts always leave me thinking… and wanting more. This one was no exception!Such a smooth and engaging read—your writing flows effortlessly. Big fan here!Every time I read your work, I feel like I’m right there with you. Beautifully written!You have a real talent for storytelling. I couldn’t stop reading once I started.The way you express your thoughts is so natural and compelling. I’ll definitely be back for more!Wow—your writing is so vivid and alive. It’s hard not to get hooked!You really know how to connect with your readers. Your words resonate long after I finish reading.