A safety lapse at courting app Uncooked publicly uncovered the non-public knowledge and personal location knowledge of its customers, TechCrunch has discovered.
The uncovered knowledge included customers’ show names, dates of delivery, courting and sexual preferences related to the Uncooked app, in addition to customers’ location. A number of the location knowledge included coordinates that had been particular sufficient to find Uncooked app customers with street-level accuracy.
Uncooked, which launched in 2023, is a courting app that claims to supply extra real interactions with others partly by asking customers to add each day selfie pictures. The corporate doesn’t disclose what number of customers it has, however its app itemizing on the Google Play Retailer notes greater than 500,000 Android downloads so far.
Information of the safety lapse is available in the identical week that the startup introduced a {hardware} extension of its courting app, the Uncooked Ring, an unreleased wearable machine that it claims will permit app customers to trace their associate’s coronary heart price and different sensor knowledge to obtain AI-generated insights, ostensibly to detect infidelity.
However the ethical and moral problems with monitoring romantic companions and the dangers of emotional surveillanceUncooked claims on its web site and in its privateness coverage that its app, and its unreleased machine, each use end-to-end encryption, a safety characteristic that stops anybody aside from the consumer — together with the corporate — from accessing the information.
Once we tried the app this week, which included an evaluation of the app’s community visitors, TechCrunch discovered no proof that the app makes use of end-to-end encryption. As a substitute, we discovered that the app was publicly spilling knowledge about its customers to anybody with an internet browser.
Uncooked mounted the information publicity on Wednesday, shortly after TechCrunch contacted the corporate with particulars of the bug.
“All beforehand uncovered endpoints have been secured, and we’ve carried out further safeguards to forestall comparable points sooner or later,” Marina Anderson, the co-founder of Uncooked courting app, advised TechCrunch by e-mail.
When requested by TechCrunch, Anderson confirmed that the corporate had not carried out a third-party safety audit of its app, including that its “focus stays on constructing a high-quality product and fascinating meaningfully with our rising group.”
Anderson wouldn’t decide to proactively notifying affected customers that their info was uncovered, however stated the corporate would “submit an in depth report back to the related knowledge safety authorities beneath relevant rules.”
It’s not instantly recognized how lengthy the app was publicly spilling its customers’ knowledge. Anderson stated that the corporate was nonetheless investigating the incident.
Concerning its declare that the app makes use of end-to-end encryption, Anderson stated Uncooked “makes use of encryption in transit and enforces entry controls for delicate knowledge inside our infrastructure. Additional steps will probably be clear after totally analyzing the state of affairs.”
Anderson wouldn’t say, when requested, whether or not the corporate plans to regulate its privateness coverage, and Anderson didn’t reply to a follow-up e-mail from TechCrunch.
How we discovered the uncovered knowledge
TechCrunch found the bug on Wednesday throughout a short check of the app. As a part of our check, we put in the Uncooked courting app on a virtualized Android machine, which permits us to make use of the app with out having to supply any real-world knowledge, similar to our bodily location.
We created a brand new consumer account with dummy knowledge, similar to a reputation and date of delivery, and configured our digital machine’s location to look as if we had been at a museum in Mountain View, California. When the app requested our digital machine’s location, we allowed the app entry to our exact location down to some meters.
We used a community visitors evaluation device to watch and examine the information flowing out and in of the Uncooked app, which allowed us to grasp how the app works and what varieties of knowledge the app was importing about its customers.
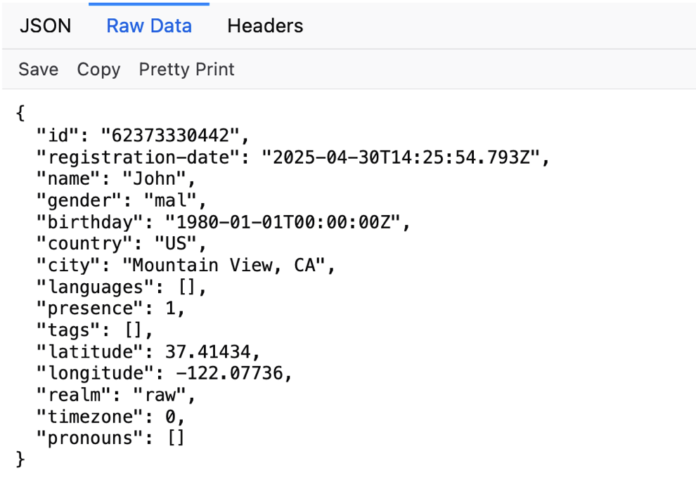
TechCrunch found the information publicity inside a couple of minutes of utilizing the Uncooked app. Once we first loaded the app, we discovered that it was pulling the consumer’s profile info straight from the corporate’s servers, however that the server was not defending the returned knowledge with any authentication.
In follow, that meant anybody might entry some other consumer’s personal info by utilizing an internet browser to go to the net deal with of the uncovered server — api.uncooked.app/customers/ adopted by a singular 11-digit quantity corresponding to a different app consumer. Altering the digits to correspond with some other consumer’s 11-digit identifier returned personal info from that consumer’s profile, together with their location knowledge.
Picture Credit:TechCrunch
 Picture Credit:TechCrunch
Picture Credit:TechCrunch
This type of vulnerability is named an insecure direct object reference, or IDOR, a sort of bug that may permit somebody to entry or modify knowledge on another person’s server due to a scarcity of correct safety checks on the consumer accessing the information.
As we’ve defined earlier than, IDOR bugs are akin to having a key to a non-public mailbox, for instance, however that key may unlock each different mailbox on that very same road. As such, IDOR bugs might be exploited with ease and in some instances enumerated, permitting entry to report after report of consumer knowledge.
U.S. cybersecurity company CISA has lengthy warned of the dangers that IDOR bugs current, together with the power to entry sometimes delicate knowledge “at scale.” As a part of its Safe By Design initiative, CISA stated in a 2023 advisory that builders ought to guarantee their apps carry out correct authentication and authorization checks.
Since Uncooked mounted the bug, the uncovered server not returns consumer knowledge within the browser.