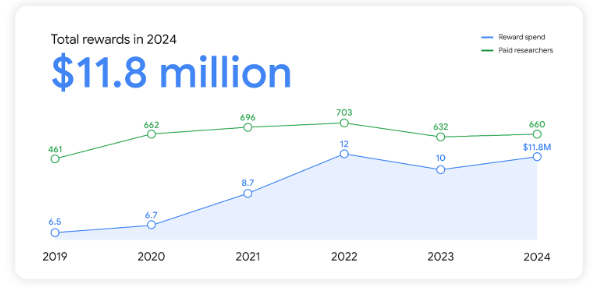
In 2024, our Vulnerability Reward Program confirmed the continued worth of participating with the safety analysis neighborhood to make Google and its merchandise safer. This was evident as we awarded simply shy of $12 million to over 600 researchers primarily based in nations across the globe throughout all of our applications.
Vulnerability Reward Program 2024 in Numbers
You may study who’s reporting to the Vulnerability Reward Program by way of our Leaderboard – and discover out extra about our youngest safety researchers who’ve not too long ago joined the ranks of Google bug hunters.
VRP Highlights in 2024
In 2024 we made a collection of modifications and enhancements coming to our vulnerability reward applications and associated initiatives:
The Google VRP revamped its reward constructionbumping rewards as much as a most of $151,515, the Cell VRP is now providing as much as $300,000 for vital vulnerabilities in top-tier apps, Cloud VRP has a top-tier award of up $151,515, and Chrome awards now peak at $250,000 (see the beneath part on Chrome for particulars).
We rolled out InternetCTF – to get rewarded, uncover novel code execution vulnerabilities in open supply and supply Tsunami plugin patches for them.
The Abuse ribbon noticed a 40% YoY improve in payouts – we obtained over 250 legitimate bugs concentrating on abuse and misuse points in Google merchandise, leading to over $290,000 in rewards.
To enhance the cost course of for rewards going to bug hunters, we launched Bugcrowd as an extra cost possibility on bughunters.google.com alongside the present customary Google cost possibility.
We hosted two editions of bugSWAT for coaching, talent sharing, and, in fact, some dwell hacking – in August, we had 16 bug hunters in attendance in Las Vegas, and in October, as a part of our annual safety convention ESCAL8 in Malaga, Spainwe welcomed 40 of our prime researchers. Between these two occasions, our bug hunters had been rewarded $370,000 (and loads of swag).
We doubled down on our dedication to assist the following era of safety engineers by internet hosting 4 init.g workshops (Las Vegas, São Paulo, Parisand Malaga). Observe the Google Rove Channel on X to remain tuned on future occasions.
Extra detailed updates on chosen applications are shared within the following sections.
Android and Google Gadgets
In 2024, the Android and Google Gadgets Safety Reward Program and the Google Cell Vulnerability Reward Program, each a part of the broader Google Bug Hunters program, continued their mission to fortify the Android ecosystem, attaining new heights in each affect and severity. We awarded over $3.3 million in rewards to researchers who demonstrated distinctive talent in uncovering vital vulnerabilities inside Android and Google cell functions.
The above numbers mark a major change in comparison with earlier years. Though we noticed an 8% lower within the whole variety of submissions, there was a 2% improve within the variety of vital and excessive vulnerabilities. In different phrases, fewer researchers are submitting fewer, however extra impactful bugs, and are citing the improved safety posture of the Android working system because the central problem. This showcases this system’s sustained success in hardening Android.
This 12 months, we had a heightened give attention to Android Automotive OS and WearOS, bringing precise automotive units to a number of dwell hacking occasions and conferences. At ESCAL8, we hosted a live-hacking problem centered on Pixel units, leading to over $75,000 in rewards in a single weekend, and the invention of a number of reminiscence security vulnerabilities. To facilitate studying, we launched a brand new Android hacking course in collaboration with exterior safety researchers, centered on cell app safety, designed for newcomers and veterans alike. Keep tuned for extra.
We prolong our deepest gratitude to the devoted researchers who make the Android ecosystem safer. We’re proud to work with you! Particular due to Zinuo Han (@ Elquoxxh) for his or her experience in Bluetooth safety, blunt (@blunt_qian) for holding the file for essentially the most legitimate experiences submitted to the Google Play Safety Reward Program, and WANG,YONG (@ThomasKing2014) for groundbreaking analysis on rooting Android units with kernel MTE enabled. We additionally respect all researchers who participated in final 12 months’s bugSWAT occasion in Málaga. Your contributions are invaluable!
Chrome
Chrome did some transforming in 2024 as we up to date our reward quantities and construction to incentivize deeper analysis. For instance, we elevated our most reward for a single problem to $250,000 for demonstrating RCE within the browser or different non-sandboxed course of, and extra if accomplished straight with out requiring a renderer compromise.
In 2024, UAF mitigation MiraclePtr was totally launched throughout all platforms, and a 12 months after the preliminary launch, MiraclePtr-protected bugs are not being thought of exploitable safety bugs. In tandem, we elevated the MiraclePtr Bypass Reward to $250,128. Between April and November, we additionally launched the primary and second iterations of the V8 Sandbox Bypass Rewards as a part of the development in the direction of the V8 sandbox, finally changing into a safety boundary in Chrome.
We obtained 337 experiences of distinctive, legitimate safety bugs in Chrome throughout 2024, and awarded 137 Chrome VRP researchers $3.4 million in whole. The best single reward of 2024 was $100,115 and was awarded to Mickey for his or her report of a MiraclePtr Bypass after MiraclePtr was initially enabled throughout most platforms in Chrome M115 in 2023. We rounded out the 12 months by saying the prime 20 Chrome VRP researchers for 2024all of whom had been gifted new Chrome VRP swag, that includes our new Chrome VRP mascot, Bug.
Cloud VRP
The Cloud VRP launched in October as a Cloud-focused vulnerability reward program devoted to Google Cloud services. As a part of the launch, we additionally up to date our product tiering and improved our reward construction to raised align our experiences with their affect on Google Cloud. This resulted in over 150 Google Cloud merchandise coming underneath the highest two reward tiers, enabling higher rewards for our Cloud researchers and a safer cloud.
Since its launch, Google Cloud VRP triaged over 400 experiences and filed over 200 distinctive safety vulnerabilities for Google Cloud services resulting in over $500,000 in researcher rewards.
Our spotlight final 12 months was launching on the bugSWAT occasion in Málaga the place we bought to fulfill lots of our wonderful researchers who make our program so profitable! The overwhelming optimistic suggestions from the researcher neighborhood continues to propel us to mature Google Cloud VRP additional this 12 months. Keep tuned for some thrilling bulletins!
Generative AI
We’re celebrating an thrilling first 12 months of AI bug bounties. We obtained over 150 bug experiences – over $55,000 in rewards to this point – with one-in-six resulting in key enhancements.
Regulate Gen AI in 2025 as we give attention to increasing scope and sharing extra methods for our researcher neighborhood to contribute.
In 2025, we will probably be celebrating 15 years of VRP at Google, throughout which now we have remained totally dedicated to fostering collaboration, innovation, and transparency with the safety neighborhood, and can proceed to take action sooner or later. Our purpose stays to remain forward of rising threats, adapt to evolving applied sciences, and proceed to strengthen the safety posture of Google’s services.
We wish to ship an enormous thanks to our bug hunter neighborhood for serving to us make Google merchandise and platforms extra secure and safe for our customers world wide – and invite researchers not but engaged with the Vulnerability Reward Program to hitch us in our mission to maintain Google secure!
Thanks to Dirk Göhmann, Amy Ressler, Eduardo Vela, Jan Keller, Krzysztof Kotowicz, Martin Straka, Michael Cote, Mike Antares, Sri Tulasiram, and Tony Mendez.
Tip: Wish to learn of latest developments and occasions round our Vulnerability Reward Program? Observe the Google Rove Channel on X to remain within the loop and make sure to take a look at the Safety Engineering weblog, which covers subjects starting from VRP updates to safety practices and vulnerability descriptions (30 posts in 2024)!