4 vulnerabilities dubbed PerfektBlue and affecting the BlueSDK Bluetooth stack from OpenSynergy will be exploited to realize distant code execution and doubtlessly enable entry to important parts in autos from a number of distributors, together with Mercedes-Benz AG, Volkswagen, and Skoda.
OpenSynergy confirmed the failings final yr in June and launched patches to clients in September 2024 however many automakers have but to push the corrective firmware updates. Not less than one main OEM discovered solely not too long ago concerning the safety dangers.
The safety points will be chained collectively into an exploit that researchers name a Excellent Blue Assault and will be delivered over-the-air by an attacker, requiring “at most 1-click from a person.”
Though OpenSynergy’s BlueSDK is broadly used within the automotive trade, distributors from different sectors additionally use it.
Excellent Blue Assaults
The pentesters staff at PCA Cyber Safetyan organization specialised in automotive safety, found the PerfektBlue vulnerabilities and reported them to OpenSynergy in Could 2024. They’re common contributors at Pwn2Own Automotive competitions and have uncovered over 50 vulnerabilities in automobile programs since final yr.
In line with them, the PerfektBlue assault impacts “hundreds of thousands of units in automotive and different industries.”
Discovering the failings in BlueSDK was attainable by analyzing a compiled binary of the software program product, for the reason that didn’t have entry to the supply code.
The glitches, listed beneath, vary in severity from low to excessive and might present entry to the automobile’s internals by way of the infotainment system.
CVE-2024-45434 (excessive severity) – use-after-aree within the AVRCP service for Bluetooth profile that enables distant management over media units
CVE-2024-45431 (low severity) – improper validation of an L2CAP ((Logical Hyperlink Management and Adaptation Protocol)) channel’s distant channel identifier (CID)
CVE-2024-45433 (medium severity) – incorrect perform termination within the Radio Frequency Communication (RFCOMM) protocol
CVE-2024-45432 (medium severity) – perform name with incorrect parameter within the RFCOMM protocol
The researchers didn’t share full technical particulars about exploiting the PerfektBlue vulnerabilities however mentioned that an attacker paired to the affected gadget may exploit them to “manipulate the system, escalate privileges and carry out lateral motion to different elements of the goal product.”
PCA Cyber Safety demonstrated PerfektBlue assaults on infotainment head items in Volkswagen ID.4 (ICAS3 system), Mercedes-Benz (NTG6), and Skoda Excellent (MIB3), and obtained a reverse shell on prime of the TCP/IP that enables communication between units on a community, resembling elements in a automobile.
The researchers say that with distant code execution on in-vehicle infotainment (IVI) a hacker may monitor GPS coordinates, snoop on conversations within the automobile, entry telephone contacts, and doubtlessly transfer laterally to extra important subsystems within the car.
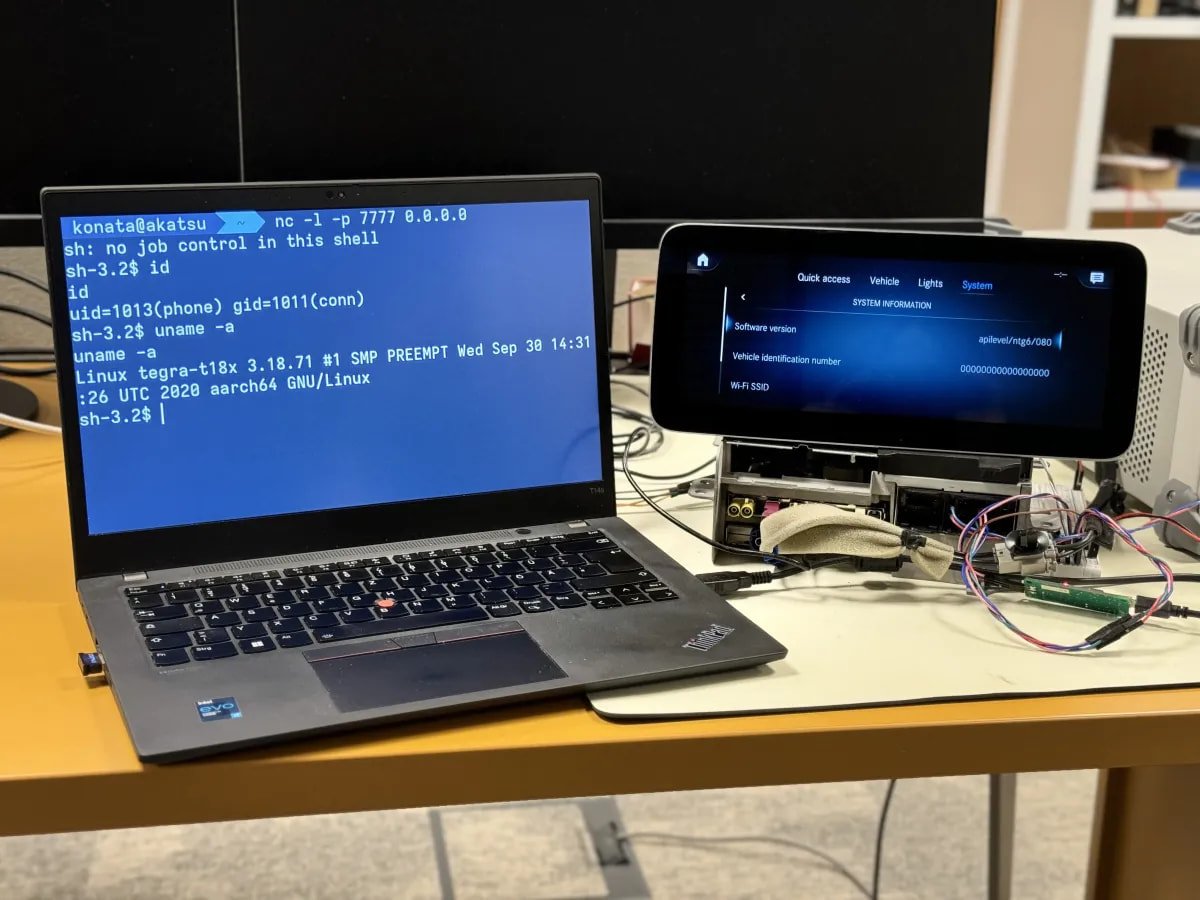 Getting a reverse shell on a Mercedes-Benz NTG6 system
Getting a reverse shell on a Mercedes-Benz NTG6 system
Supply: PCA Cyber Safety
Threat and publicity
OpenSynergy’s BlueSDK is broadly used within the automotive trade however it’s tough to find out what distributors depend on it because of customization and repackaging processes, in addition to lack of transparency relating to the embedded software program elements of a automobile.
PerfektBlue is principally a 1-click RCE as a result of many of the occasions it requires tricking the person to permit pairing with an attacker gadget. Nevertheless, some automakers configure infotainment programs to pair with none affirmation.
PCA Cyber Safety instructed BleepingComputer that they knowledgeable Volkswagen, Mercedes-Benz, and Skoda concerning the vulnerabilities and gave them enough time to use the patches however the researchers obtained no reply from the distributors about addressing the problems.
BleepingComputer has contacted the three automakers asking in the event that they pushed OpenSynergy’s fixes. A press release from Mercedes was not instantly avaialable and Volkswagen mentioned that they began investigating the influence and methods to handle the dangers immediatelly after studying concerning the points.
“The investigations revealed that it’s attainable below sure circumstances to hook up with the car’s infotainment system through Bluetooth with out authorization,” a Volkwagen spokesperson instructed us.
The German automobile maker mentioned that leveraging the vulnerabilities is feasible provided that a number of circumstances are met on the similar time:
The attacker is inside a most distance of 5 to 7 meters from the car.
The car’s ignition should be switched on.
The infotainment system should be in pairing mode, i.e., the car person should be actively pairing a Bluetooth gadget.
The car person should actively approve the exterior Bluetooth entry of the attacker on the display screen.
Even when these circumstances happen and an attacker connects to the Bluetooth interface, “they need to stay inside a most distance of 5 to 7 meters from the car” to take care of entry, the Volkswagen consultant mentioned.
The seller underlined that within the case of a profitable exploit, a hacker couldn’t intervene with important car capabilities like steering, driver help, engine, or brakes as a result of they’re “on a unique management unit protected in opposition to exterior interference by its personal safety capabilities.”
PCA Cyber Safety instructed BleepingComputer that final month they confirmed PerfektBlue at a fourth OEM within the automotive trade, who mentioned that OpenSynergy hadn’t knowledgeable them of the problems.
“We determined to not disclose this OEM as a result of there was not sufficient time for them to react,” the researchers instructed us.
“We plan to reveal the small print about this affected OEM in addition to the total technical particulars of PerfektBlue in November 2025, within the format of a convention speak.”
BleepingComputer has additionally contacted OpenSynergy to inquire concerning the influence PerfektBlue has on its clients and what number of are affected however now we have not obtained a reply at publishing time.
Whereas cloud assaults could also be rising extra subtle, attackers nonetheless succeed with surprisingly easy methods.
Drawing from Wiz’s detections throughout 1000’s of organizations, this report reveals 8 key methods utilized by cloud-fluent menace actors.






your blog is fantastic! I’m learning so much from the way you share your thoughts.
I love how you write—it’s like having a conversation with a good friend. Can’t wait to read more!This post pulled me in from the very first sentence. You have such a unique voice!Seriously, every time I think I’ll just skim through, I end up reading every word. Keep it up!Your posts always leave me thinking… and wanting more. This one was no exception!Such a smooth and engaging read—your writing flows effortlessly. Big fan here!Every time I read your work, I feel like I’m right there with you. Beautifully written!You have a real talent for storytelling. I couldn’t stop reading once I started.The way you express your thoughts is so natural and compelling. I’ll definitely be back for more!Wow—your writing is so vivid and alive. It’s hard not to get hooked!You really know how to connect with your readers. Your words resonate long after I finish reading.